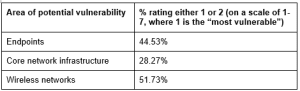
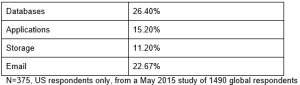According to a May 2015 global survey of IT decision makers (ITDMs), wireless networks are a significant source of risk and vulnerability for their organizations. Among US respondents, in fact (as with their global counterparts), more ITDMs identified wireless networks as the most vulnerable part of the enterprise than any other component.
Wireless networks have traditionally been easy targets – easy targets for hackers and sketchy places for guests to conduct business. Yet they’re not only ubiquitous, but expected features on networks of all sizes. Reconciling security with ready access both for internal and external users is no easy task.
Take for example the current keyboard hack issue affecting the Samsung Galaxy line and nearly 600 million Samsung customers. When a user is connected to a compromised wireless network, hackers (with the right tools) can gain access to their Galaxy device and all of the data – corporate or personal – connected to it.
To that end, LightSpeed GMI recently conducted a survey of almost 1500 IT decision makers (ITDMs) from mid-size and large organizations around the globe about their security concerns. The 375 U.S. respondents, like their global counterparts, identified one area above all others as the “most vulnerable” from a security standpoint: their wireless networks.
A closer look at the U.S. data, in particular, reveals that most ITDMs consider their wireless networks to be a weak link in their security, whether wireless was used exclusively for internal purposes or opened up for guest access. On a scale of 1-7, where 1 was “most vulnerable” and 7 was “least vulnerable,” more than half rated their wireless networks a 1 or 2. Almost 70% rated them 1, 2, or 3.
Compare those numbers to databases and applications, for example, and the picture becomes even clearer:
Only endpoints even come close in terms of concern for ITDMs.
Not surprisingly, organizations are taking steps to address these concerns, especially for wireless networks used for internal access. The majority of respondents had implemented firewalls, authentication measures, and anti-virus to secure their internal wireless networks. However, almost half of the U.S. respondents allow guest access to their wireless networks. Of these respondents, more than 16% use no authentication whatsoever. Another 16% use a captive portal with no registration, while another 22% use a shared username and password (the sort that gets posted on a conference room wall).
In this context, it’s no wonder that wireless networks have IT decision makers worried. Again, it’s no surprise that BYOD implementations further complicate matters. Over half of the respondents who reported allowing BYOD also allow personal devices to access sensitive corporate resources. This isn’t a problem in and of itself – BYOD programs are often hobbled by restrictions on the use of personal devices. However, without adequate security measures in place, the risk of malicious apps or careless employees exposing sensitive data remains high.
In fact, the loss of sensitive corporate and/or customer data was the top concern related to wireless security among both U.S. and international respondents. Industrial espionage was second, with regulatory compliance, reputation damage, and service disruption rounding out the major areas of concern.
So what can organizations do? Layered approaches to security, meant to protect the network from malicious attempts at every entry point, are an essential component of any security strategy, including those related to wireless networks. New advances in wireless controller and monitoring technologies can also bring robust security directly to the wireless networks themselves, improving both security and access for employees and guests alike.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.