Last week High-Tech Bridge’s Security Research Team was preparing our web vulnerabilities statistics report for 2013 [to be published next week]. Critical web vulnerabilities such as SQL Injections or Remote Command Executions are becoming rare and difficult to exploit as web developers are more and more aware of them. However, the number of medium-risk vulnerabilities, such as XSS (Cross-Site Scripting) is permanently growing. Being a medium-risk vulnerability, XSS usually provides a larger number of attack and exploitation opportunities to hackers than other web vulnerabilities, as it does not target the web application, but rather website visitors and administrators. Stealing cookies, website’s credentials and browser history is probably the least harmful vector of XSS attack. However, drive-by attacks via XSS that can infect a website visitor’s machine and turn it into a zombie just by clicking on a specially crafted link on the vulnerable website are much more dangerous.
Last week while surfing the website of World Economic Forum (WEF) – world-known organization that is holding its annual meeting in Davos (Switzerland) these days (22-26 of January) – we unintentionally discovered an XSS vulnerability in one of their subdomains:
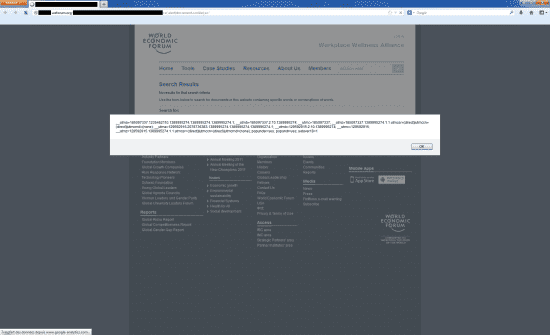
1. XSS vulnerability on a weforum.org subdomain
A quick and absolutely harmless test of their main website [www.weforum.org] revealed two more XSS vulnerabilities on it:
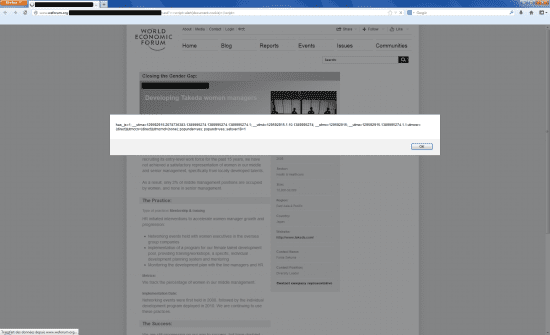
2. XSS vulnerability on www.weforum.org
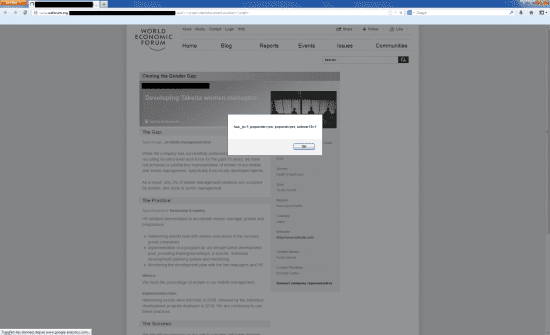
3. XSS vulnerability on www.weforum.org
Being a bit surprised that such a respectable organization has security vulnerabilities on their website, we notified them via common security emails (abuse@, security@, admin@, etc) and all appropriate emails found on their website. As the WEF was already a victim of fictitious emails attack we expected a quick reply from them. However, on the fifth day since the notification we still didn’t get a single word from their side. We started searching for additional technical contacts so that we could reach them, but instead we found an additional quite serious information disclosure vulnerability.
The WEF website has a function to contact a company representative via a web form without exposing his/her email address:
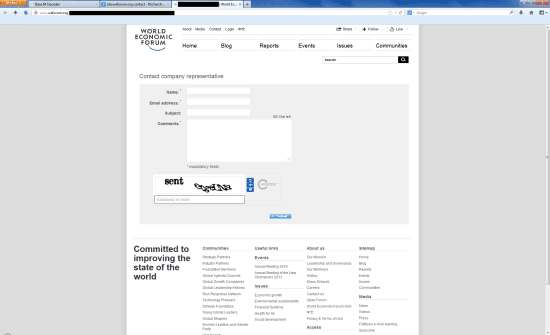
4. Company representative сontact form
However, if you have a look into the HTML source code of the page – you will find a hidden HTTP parameter named “cr” that is encoded with Base64:
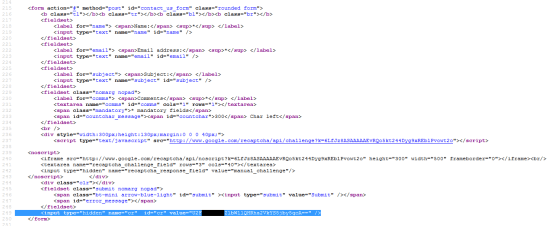
5. Contact form page HTML source
Being curious, we decoded the parameter and to our surprise we got a personal email address of the person in plaintext. For each ID (HTTP “n” parameter) email address was unique and belonged to a different person. Guided by ethics we obviously didn’t make a full list of the emails (the largest ID we found was 106,515), but we can presume that at least several thousands of forum stakeholders’ emails can be disclosed to spammers because of this vulnerability. The biggest risk here is that these personal emails can be used by hackers to perform targeted attacks in pair with XSS vulnerabilities that make quite an explosive and efficient hacking cocktail. The screenshot below demonstrates several of randomly disclosed emails:
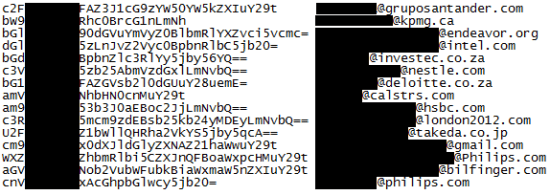
6. Random user emails disclosed via vulnerability
Last but not least, the SSL certificate on the www.weforum.org is invalid and therefore cannot correctly encrypt the traffic between the end-users and the web server putting website visitors’ privacy at risk:
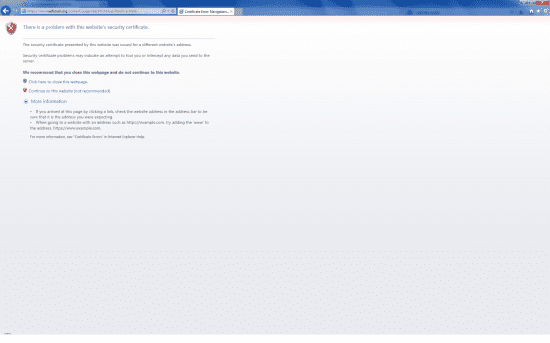
7. www.weforum.org SSL certificate error – Internet Explorer
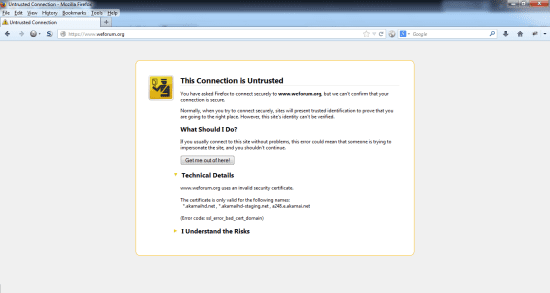
8. www.weforum.org SSL certificate error – Firefox
Ilia Kolochenko, High-Tech Bridge’s CEO, comments: “It’s regrettable that such respectable, large and important organizations like the WEF don’t pay enough attention to web security. This may not only put their own infrastructure at risk, but their stakeholders as well. Hopefully, they will change their security policy soon and provide security researchers with a responsive security contact, just like many other companies and organizations do today. Moreover, the vulnerabilities we reported are quite possibly just the tip of iceberg, as without their [WEF] permission we didn’t want to perform any further more “intrusive” security checks that can reveal much more serious vulnerabilities. I sincerely hope that these vulnerabilities were not exploited by hackers for whom WEF and its participants are very attractive targets.“
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



