What you need to know right now to protect your site and customers from the Magento flaw
Imagine you owned a grocery store and someone simply walked into it, appointed himself manager and then used his newfound authority to help himself to customer credit card information and even change the prices of items. It’s such a seemingly unrealistic situation it borders on unfathomable, right? And yet, nearly 100,000 stores all over the world found themselves facing this exact threat this week.
Magento is the number one open-source content management system for e-commerce websites. That means that when a vulnerability was discovered in community and enterprise editions of Magento, almost 100,000 e-commerce websites were immediately at risk, which put the personal information of millions of consumers at risk at well. Here’s everything you need to know about the Magento flaw in order to protect your website and your customers.
Magento vulnerability details
What’s being called the Magento flaw or vulnerability is a remote-code execution hole in enterprise and community versions of the Magento content management system. This vulnerability is actually a series of vulnerabilities that give an attacker the ability to execute PHP code on the web server. This allows the attacker to bypass security, create a new administrator account, and seize control of not just the online store but its complete database, including the personal and financial information of customers.
While this vulnerability could potentially be exploited by any attacker with the necessary skills, so far there seems to be a couple of specific group of attackers taking advantage of it. If you suspect your website has been compromised, check for usernames default manager or vpwq, as these are the names security groups have seen cropping up in the attacks. You could also check for access from IP addresses 62.76.177.179 and 185.22.232.218.
Full access and full control
Because the Magento vulnerability allows attackers to create new administrator accounts, it gives those attackers all the same powers an administrator would have. And since the type of people who quickly take advantage of a newly-discovered vulnerability aren’t the type of people who would pop into your website just to change the name of your store to Pee Pants Enterprises and have themselves a little laugh, this is bad.
By exploiting the Magento vulnerability, attackers are able to dump database content to obtain credit card data and customers’ personal information like phone numbers, addresses and emails. Having all of that data properly encrypted is a good security measure, but attackers may still be able to insert a script that steals that information while it’s briefly being processed prior to encryption. The damage that could possibly be done from this attack may not be done immediately.
Attackers are also able to tinker with other admin settings, such as changing the prices of items in the online store, and could possibly set up malware to infect customers’ computers.
By the numbers
Magento is owned by ecommerce giant eBay, and their engineers were first informed of the vulnerability in January. They acted on the information and released a patch in February. However, as of last week, over 98,000 ecommerce sites still hadn’t installed it.
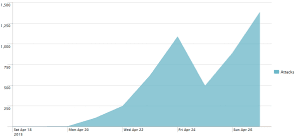
According to internet security firm Incapsula, the attack attempts began last Monday, with fewer than 250 attempted attacks on sites under the protection of Incapsula. According to Incapsula reports, the action ramped up on Tuesday and reached a peak last Sunday, with almost 1500 attempts on Incapsula-protected sites that day. Incapsula state that the attacks seem to be originating from Russia and China.
Number of attacks per date (source + Hi-res: Incapsula report)
What ecommerce sites need to do NOW
If you have a website utilizing the community or enterprise editions of the Magento CMS, you need to be on the Magento downloads page downloading patch SUPEE-5344 right now. If you haven’t done it, go do it.
Furthermore, whether your ecommerce site uses Magento or any other type of CMS, for the sake of your website and your valued customers, you need to be looking into a Web Application Firewall, preferably a SaaS WAF. Even if you’re not affected by this vulnerability, you could be affected by the next one. A good WAF will protect you from a wide range of security threats, including DDoS attacks, by dictating the way users, both humans and bots, are allowed to interact with your website.
With our increasingly online world, the surreal becomes more real every day, and unfathomable attacks on businesses are becoming all too fathomable. The best defense will always be a good offense. Protect your website before it becomes time to scramble for a patch.
By Benjamin Stone writer and technology enthusiast
 BIO : Benjamin is a seasoned writer and technology enthusiast. He has written various articles on the topic of cyber security and continues to research the latest state of the art tools for tackling cyber scares. In his spare time Benjamin enjoys reading finance magazines and enjoying outdoor sporting activities.
BIO : Benjamin is a seasoned writer and technology enthusiast. He has written various articles on the topic of cyber security and continues to research the latest state of the art tools for tackling cyber scares. In his spare time Benjamin enjoys reading finance magazines and enjoying outdoor sporting activities.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.