Overview:
This is the second in a series of blogs collecting the recent activity of the current top exploit kits. Exploit kits are rapidly deployable software packages designed to leverage vulnerabilities in web browsers to deliver a malicious payload to a victim’s computer. Authors of exploit kits offer their services for sale, distributing malware for other malicious actors.
Find our previous round-up here (https://www.zscaler.com/blogs/research/top-exploit-kit-activity-roundup).
Neutrino Exploit Kit
In our previous roundup, we noted that the EITest campaign had begun redirecting primarily to Neutrino landing pages since Angler exploit kit activity abruptly stopped in early June 2016.
EITest gates have continued redirecting to Neutrino landing pages, as well as RIG, throughout Summer 2016.
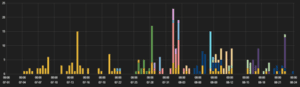
(Neutrino hits)
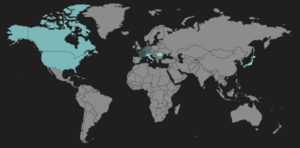
(Neutrino heat map)
Neutrino landing pages still primarily use top TLD names and target Adobe Flash Player. The majority of Neutrino hosts observed were hosted in Western Europe and North America.
Starting in mid-June, the EITest Neutrino landing pages began distributing CryptXXX ransomware payloads. Prior to its shutdown, Angler was the main distributor of CryptXXX ransomware, and its stoppage caused a significant decline in CryptXXX infections. The increased usage of Neutrino to distribute CryptXXX helped fill the void left by Angler.
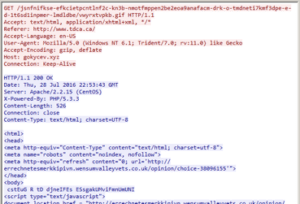
(EITest gate redirect to Neutrino landing page)
In late July, EITest Neutrino landing pages began delivering CrypMIC ransomware, a new variant of CryptXXX. Non-EITest Neutrino campaigns involving malvertising continue to drop Tofsee, Gamarue, and various ransomware payloads.
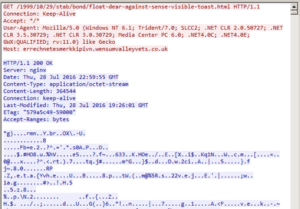
(CrypMIC payload from Neutrino infection chain)
CrypMIC ransomware communicates with its C&C server via plain text over TCP port 443 (typically reserved for HTTPS/SSL traffic).
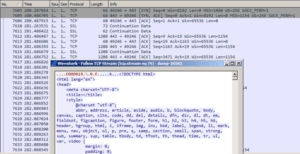
(CrypMIC callback and ransom page)
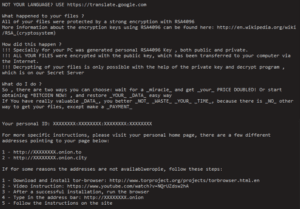
(Example CrypMIC ransom instructions)
RIG Exploit Kit
RIG remains active over several campaigns. The usual compromised sites and malvertising redirects are prevalent, as well as redirections to RIG from EITest gates.

(RIG hits)
Observed hits on RIG domains have been relatively consistent throughout the summer.
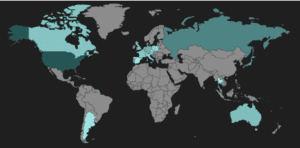
(RIG heat map)
The United States is still the largest host of RIG domains, though this summer we have seen an increase of hosts in Russia, as well as in several countries in Western Europe and the Americas.
The “topgunnphoto” gate mentioned in our previous round-up is still visible, but infection cycles from this gate declined through late July and early August. A thorough overview of recent RIG activity was published by Malwarebytes in late July, which illustrates several common RIG campaigns.
Not covered in the Malwarebytes article is a non-standard RIG campaign that originates with casino-themed malvertising. This campaign uses an atypical landing page URL scheme mentioned in the previous round-up, which breaks from the pattern of a two-character third-level domain.

(RIG casino-based malvertising infection cycle)
RIG continues to drop Tofsee payloads and a new variant of Zeus, as we have previously described. Recently, RIG has started dropping the Gootkit banking trojan through the EITest campaign, as well as Vawtrak and Cerber payloads.
Other Exploit Kits
Magnitude
Magnitude is a long-running exploit kit that has been active since October 2013. Through summer, it has continued its recent trend of dropping Cerber ransomware payloads through malvertising campaigns.
(Magnitude infection cycle)
Angler Exploit Kit
Angler EK shut down in early June 2016, and is now considered to be defunct. EITest gates which had been primarily redirecting to Angler landing pages have since begun redirecting to Neutrino and RIG landing pages
Nuclear Exploit Kit
Nuclear has had no activity since late April 2016, and is now considered to be defunct. Some compromised site injection artifacts are still observed, but no active redirectors or gates.
Sundown Exploit Kit
In early July, Zscaler’s ThreatLabZ published an article analysing the activity of Sundown over the previous month (https://www.zscaler.com/blogs/research/sundown-chronicles-observations-exploit-kits-evolution). Most recently, variations to Sundown’s landing page obfuscation structure have been observed, and Sundown has begun dropping a variant of the Kasidet backdoor with modified callback protocols.
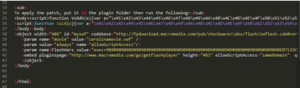
(Sundown landing page excerpt)
In early July, Sundown EK quickly integrated the recently-published exploit CVE-2016-0189 (https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2016-0189), a VBScript memory corruption vulnerability in IE11, into new landing pages. The standard Sundown landing page was replaced entirely with a modified version of the open source POC for the exploit.

(Sundown EK using CVE-2016-0189)
Conclusion
Exploit kits pose a significant threat to users during simple web browsing. In the case of ransomware infections, the result could be the inability of a user to access his or her files. The techniques exploit kit authors use to hide their activities are frequently changing, and security researchers work hard to analyse and block these new threats.
To help avoid infections such as these, users should always block untrusted third-party scripts and resources, and avoid clicking on suspicious advertisements. Zscaler’s ThreatLabZ has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organisations using Zscaler’s Internet security platform.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



