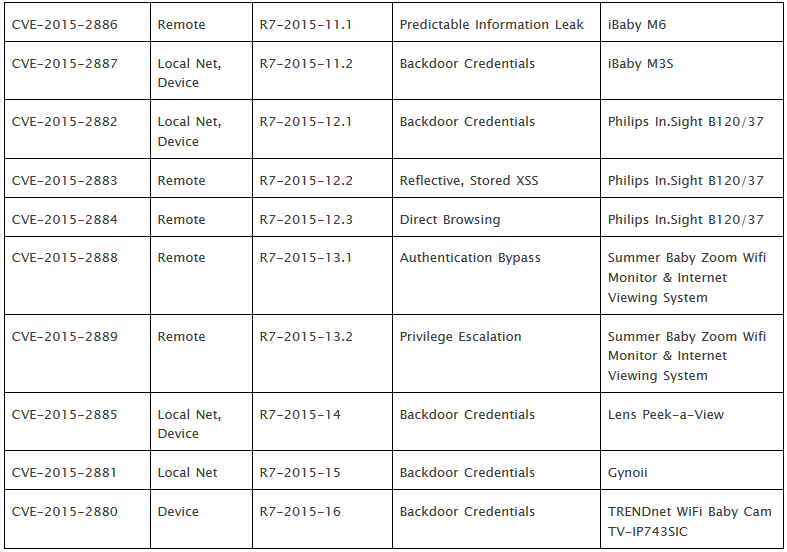
Usually, these disclosure notices contain one, maybe two vulnerabilities on one product. Not so for this one; we’ve got ten new vulnerabilities to disclose.
If you were out at DEF CON 23, you may have caught Mark Stanislav’s workshop, “The Hand that Rocks the Cradle: Hacking IoT Baby Monitors.” You may have also noticed some light redaction in the slides, since during the course of that research, Mark uncovered a number of new vulnerabilities across several video baby monitors.
Vendors were notified, CERT/CC was contacted, and CVEs have all been assigned, per the usual disclosure policy, which brings us to the public disclosure piece, here.
For more background and details on the IoT research we’ve performed here at Rapid7, we’ve put together a collection of resources on this IoT security research. There, you can find the whitepaper covering many more aspects of IoT security, some frequently asked questions around the research, and a registration link for next week’s live webinar with Mark Stanislav and Tod Beardsley.
Summary
Vendor: iBaby Labs, Inc.
The issues for the iBaby devices were disclosed to CERT under vulnerability note VU#745448.
Device: iBaby M6
The vendor’s product site for the device assessed is HERE.
Vulnerability R7-2015-11.1: Predictable public information leak (CVE-2015-2886)
The web site ibabycloud.com has a vulnerability by which any authenticated user to the ibabycloud.com service is able to view camera details for any other user, including video recording details, due to a direct object reference vulnerability.
The object ID parameter is eight hexadecimal characters, corresponding with the serial number for the device. This small object ID space enables a trivial enumeration attack, where attackers can quickly brute force the object IDs of all cameras.
Once an attacker is able to view an account’s details, broken links provide a filename that is intended to show available “alert” videos that the camera recorded. Using a generic AWS CloudFront endpoint found via sniffing iOS app functionality, this URL can have the harvested filename appended and data accessed from the account. This effectively allows anyone to view videos that were created from that camera stored on the ibabycloud.com service, until those videos are deleted, without any further authentication.
Relevant URLs
- Access camera’s details, including video-recording filenames: [any authenticated user]
- Access a camera’s video recording: [no authentication required]
Additional Details
The ibabycloud.com authentication procedure has been non-functional as of at least June, 2015, continuing through the publication of this paper in September, 2015. These errors started after testing was conducted for this research, and today, do not allow for logins to the cloud service. That noted, it may be possible to still get a valid session via the API and subsequently leverage the site and API to gain these details.
Mitigations
Today, this attack is more difficult without prior knowledge of the camera’s serial number, as all logins are disabled on the ibabycloud.com website. Attackers must, therefore, acquire specific object IDs by other means, such as sniffing local network traffic.
In order to avoid local network traffic cleartext exposure, customers should inquire with the vendor about a firmware update, or cease using the device.
Device: iBaby M3S
The vendor’s product site for the device assessed is HERE.
Vulnerability R7-2015-11.2, Backdoor Credentials (CVE-2015-2887)
The device ships with hardcoded credentials, accessible from a telnet login prompt and a UART interface, which grants access to the underlying operating system. Those credentials are detailed below.
Operating System (via Telnet or UART)
- Username: admin
- Password: admin
Mitigations
In order to disable these credentials, customers should inquire with the vendor about a firmware update. UART access can be limited by not allowing untrusted parties physical access to the device. A vendor-provided patch should disable local administrative logins, and in the meantime, end-users should secure the device’s housing with tamper-evident labels.
Disclosure Timeline
- Sat, Jul 04, 2015: Initial contact to vendor
- Mon, Jul 06, 2015: Vendor reply, requesting details for ticket #4085
- Tue, Jul 07, 2015: Disclosure to vendor
- Tue, Jul 21, 2015: Disclosure to CERT
- Fri, Jul 24, 2015: Confirmed receipt by CERT
- Wed, Sep 02, 2015: Public disclosure
Vendor: Philips Electronics N.V.

Device: Philips In.Sight B120/37
The vendor’s product site for the device assessed is HERE.
Vulnerability R7-2015-12.1, Backdoor Credentials (CVE-2015-2882)
The device ships with hardcoded and statically generated credentials which can grant access to both the local web server and operating system.
The operating system “admin” and “mg3500” account passwords are present due to the stock firmware used by this camera, which is used by other cameras on the market today.
The web service “admin” statically-generated password was first documented by Paul Price at his blog[1].
In addition, while the telnet service may be disabled by default on the most recent firmware, it can be re-enabled via an issue detailed below.
Operating System (via Telnet or UART)
- Username: root
- Password: b120root
Operating System (via Telnet or UART)
- Username: admin
- Password: /ADMIN/
Operating System (via Telnet or UART)
- Username: mg3500
- Password: merlin
Local Web Server
Reachable via http://{device_ip}/cgi-bin/{script_path}
- Username: user
- Password: M100-4674448
Local Web Server
Reachable via http://{device_ip}/cgi-bin/{script_path}
- Username: admin
- Password: M100-4674448
- A recent update changes this password, but the new password is simply the letter ‘i’ prefixing the first ten characters of the MD5 hash of the device’s MAC address.
Vulnerability R7-2015-12.2, Reflective and Stored XSS (CVE-2015-2883)
A web service used on the backend of Philips’ cloud service to create remote streaming sessions is vulnerable to reflective and stored XSS. Subsequently, session hijacking is possible due to a lack of an HttpOnly flag.
When accessing the Weaved cloud web service[2] as an authenticated user, multiple pages have a mixture of reflective and stored XSS in them, allowing for potential session hijacking. With this access, a valid streaming session could be generated and eavesdropped upon by an attacker.
Two such examples are :
- Example 1
- Example 2
Vulnerability R7-2015-12.3, Direct Browsing via Insecure Streaming (CVE-2015-2884)
The method for allowing remote viewing uses an insecure transport, does not offer secure streams protected from attackers, and does not offer sufficient protection for the the camera’s internal web applications.
Once a remote viewing stream has been requested, a proxy connection to the camera’s internal web service via the cloud provider Yoics[3] is bound to a public hostname and port number. These port numbers appear to range from port 32,000 to 39,000 as determined from testing.This bound port is tied to a hostname with the pattern of proxy[1,3-14].yoics.net, limiting the potential number of port and host combinations to an enumerable level. Given this manageable attack space, attackers can test for for a HTTP 200 response in a reasonably short amount of time.
Once found, administrative privilege is available without authentication of any kind to the web scripts available on the device. Further, by accessing a Unicode-enabled streaming URL (known as an “m3u8” URL), a live video/audio stream will be accessible to the camera and appears to stay open for up to 1 hour on that host/port combination. There is no blacklist or whitelist restriction on which IP addresses can access these URLs, as revealed in testing.
Relevant URLs
- Open audio/video stream of a camera: http://proxy{1,3-14}.yoics.net:{32000-39000}/tmp/stream2/stream.m3u8 [no authentication required]
- Enable Telnet service on camera remotely: http://proxy{1,3-14}.yoics.net:{32000-39000}/cgi-bin/cam_service_enable.cgi [no authentication required]
Mitigations
In order to disable the hard-coded credentials, customers should inquire with the vendor about a firmware update. UART access can be limited by not allowing untrusted parties physical access to the device. A vendor-provided patch should disable local administrative logins, and in the meantime, end-users should secure the device’s housing with tamper-evident labels. In order to avoid the XSS and cleartext streaming issues with Philips’ cloud service, customers should avoid using the remote streaming functionality of the device and inquire with the vendor about the status of a cloud service update.
Additional Information
Prior to publication of this report, Philips confirmed with Rapid7 the tested device was discontinued by Philips in 2013, and the current manufacturer and distributor is Gibson Innovations. Gibson has developed a solution for the identified vulnerabilities, an expects to make updates available by September 4, 2015.
Disclosure Timeline
- Sat, Jul 04, 2015: Initial contact to vendor
- Mon, Jul 06, 2015: Vendor reply, requesting details
- Tue, Jul 07, 2015: Philips Responsible Disclosure ticket number 15191319 assigned
- Tue, Jul 17, 2015: Phone conference with vendor to discuss issues
- Tue, Jul 21, 2015: Disclosure to CERT
- Fri, Jul 24, 2015: Confirmed receipt by CERT
- Thu, Aug 27, 2015: Contacted by Weaved to validate R7-2015-12.2
- Tue, Sep 01, 2015: Contacted by Philips regarding the role of Gibson Innovations
- Wed, Sep 02, 2015: Public disclosure
Vendor: Summer Infant


Device: Summer Baby Zoom WiFi Monitor & Internet Viewing System
The vendor’s product site for the device assessed is HERE.
Vulnerability R7-2015-13.1, Authentication Bypass (CVE-2015-2888)
An authentication bypass allows for the addition of an arbitrary account to any camera, without authentication.
The web service MySnapCam[4] is used to support the camera’s functionality, including account management for access. A URL retrievable via an HTTP GET request can be used to add a new user to the camera. This URL does not require any of the camera’s administrators to have a valid session to execute this request, allowing anyone requesting the URL with their details against any camera ID to have access added to that device.
After a new user is successfully added, an e-mail will then be sent to an e-mail address provided by the attacker with authentication details for the MySnapCam web site and mobile application. Camera administrators are not notified of the new account.
Relevant URL
- Add an arbitrary user to any camera: [no authentication required]
Vulnerability R7-2015-13.2, Privilege Escalation (CVE-2015-2889)
An authenticated, regular user can access an administrative interface that fails to check for privileges, leading to privilege escalation.
A “Settings” interface exists for the camera’s cloud service administrative user and appears as a link in their interface when they login. If a non-administrative user is logged in to that camera and manually enters that URL, they are able to see the same administrative actions and carry them out as if they had administrative privilege. This allows an unprivileged user to elevate account privileges arbitrarily.
Relevant URL
- Access administrative actions as an unprivileged, but valid, user: [a user account for the camera is required]
Mitigations
In order to avoid exposure to the authentication bypass and privilege escalation, customers should use the device in a local network only mode, and use egress firewall rules to block the camera from the Internet. If Internet access is desired, customers should inquire about an update to Summer Infant’s cloud services.
Disclosure Timeline
- Sat, Jul 04, 2015: Initial contact to vendor
- Tue, Jul 21, 2015: Disclosure to CERT
- Fri, Jul 24, 2015: Confirmed receipt by CERT
- Tue, Sep 01, 2015: Confirmed receipt by vendor
- Wed, Sep 02, 2015: Public disclosure
Vendor: Lens Laboratories(f)


Device: Lens Peek-a-View
The vendor’s product site for the device assessed is HERE.
Of special note, it has proven difficult to find a registered domain for this vendor. All references to the vendor point at Amazon directly, but Amazon does not appear to be the manufacturer or vendor.
Vulnerability R7-2015-14, Backdoor Credentials (CVE-2015-2885)
The device ships with hardcoded credentials, accessible from a UART interface, which grants access to the underlying operating system, and via the local web service, giving local application access via the web UI.
Due to weak filesystem permissions, the local OS ‘admin’ account has effective ‘root’ privileges.
Operating System (via UART)
- Username: admin
- Password: 2601hx
Local Web Server
Site: http://{device_ip}/web/
- Username: user
- Password: user
Local Web Server
Site: via http://{device_ip}/web/
- Username: guest
- Password: guest
Mitigations
In order to disable these credentials, customers should inquire with the vendor about a firmware update. UART access can be limited by not allowing untrusted parties physical access to the device. A vendor-provided patch should disable local administrative logins, and in the meantime, end-users should secure the device’s housing with tamper-evident labels.
Disclosure Timeline
- Sat, Jul 04, 2015: Attempted to find vendor contact
- Tue, Jul 21, 2015: Disclosure to CERT
- Fri, Jul 24, 2015: Confirmed receipt by CERT
- Wed, Sep 02, 2015: Public disclosure
Vendor: Gynoii, Inc.


Device: Gynoii
The vendor’s product site for the device assessed is HERE.
Vulnerability R7-2015-15, Backdoor Credentials (CVE-2015-2881)
The device ships with hardcoded credentials, accessible via the local web service, giving local application access via the web UI.
Local Web Server
Site: http://{device_ip}/admin/
- Username: guest
- Password: guest
Local Web Server
Site: http://{device_ip}/admin/
- Username: admin
- Password: 12345
Mitigations
In order to disable these credentials, customers should inquire with the vendor about a firmware update.
Disclosure Timeline
- Sat, Jul 04, 2015: Initial contact to vendor
- Tue, Jul 21, 2015: Disclosure to CERT
- Fri, Jul 24, 2015: Confirmed receipt by CERT
- Wed, Sep 02, 2015: Public disclosure
Vendor: TRENDnet


Device: TRENDnet WiFi Baby Cam TV-IP743SIC
The vendor’s product site for the device under test is HERE.
Vulnerability R7-2015-16: Backdoor Credentials (CVE-2015-2880)
The device ships with hardcoded credentials, accessible via a UART interface, giving local, root-level operating system access.
Operating System (via UART)
- Username: root
- Password: admin
Mitigations
In order to disable these credentials, customers should inquire with the vendor about a firmware update. UART access can be limited by not allowing untrusted parties physical access to the device. A vendor-provided patch should disable local administrative logins, and in the meantime, end-users should secure the device’s housing with tamper-evident labels.
Disclosure Timeline
- Sat, Jul 04, 2015: Initial contact to vendor
- Mon, Jul 06, 2015: Vendor reply, details disclosed to vendor
- Sun, Jul 16, 2015: Clarification sought by vendor
- Mon, Jul 20, 2015: Clarification provided to vendor
- Tue, Jul 21, 2015: Disclosure to CERT
- Wed, Sep 02, 2015: Public disclosure
Not Just Baby Monitors
As you can see, there were several new findings across a range of vendors, all operating in the same space. Here at Rapid7, we believe this is not unique to the video baby monitor industry in particular, but is indicative of a larger, systemic problem with IoT in general. We’ve put together a collection of IoT resources, including a whitepaper and a FAQ, covering these issues, which should fill you in on where we’re at on this IoT security journey. In the meantime, keep an eye on those things keeping an eye on your infants and toddlers.[su_box title=”About Rapid7″ style=”noise” box_color=”#336588″]