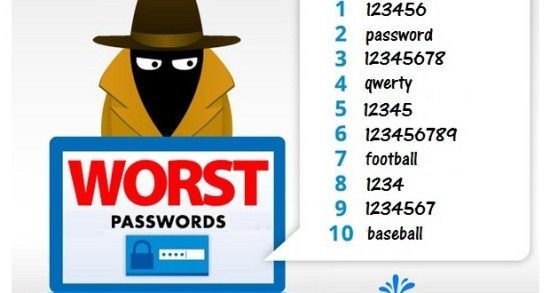
In response to a new report from Splash Data which revealed the most popular passwords stolen over the course of the year, Security experts at Imperva, Tripwire, ESET and Lieberman Software have the following comments on it.
[su_note note_color=”#ffffcc” text_color=”#00000″]Amichai Shulman, CTO of Imperva:
“As we pointed out in our Rockyou research, the abundant use of such easy passwords changes the way attackers are looking at brute force. Rather than trying all possible password combinations for each individual account, attackers are testing a small number of common passwords for all accounts, thus they guarantee a good rate of success. In one of Imperva’s recent papers on passwords we showed that the top 5,000 common passwords are used by 20 percent of internet users. This is a staggering success rate for an attacker with almost no cost. In fact, for the Rockyou data set we showed that such an attack would yield one compromised account per ~100 attempts. What this means for enterprises is that attackers can launch brute force attacks that have a smaller network footprint than expected. This essentially means more comprehensive account takeover mitigation measures are required.”[/su_note]
[su_note note_color=”#ffffcc” text_color=”#00000″]Lamar Bailey, Director of Security Research and Development at Tripwire:
“Common passwords like these are very dangerous because hackers use a technique called a Dictionary Attack to gain access to accounts. This method uses a file of known popular passwords and tries them one at a time until the correct match is found. When popular password lists or credentials from a data breach are published the attackers update their list to move the most popular passwords to the top of their dictionary. Users should never use any password published in a top password list, using a password manager that auto generates obscure passwords is much safer.”[/su_note]
[su_note note_color=”#ffffcc” text_color=”#00000″]Jonathan Sander, VP of product strategy at Lieberman Software Corporation:
“What computers are good at is taking clear instructions and sets of data to run through repetitive tasks in an automated manner. What could be simpler for an attacker than to take a list of the most common passwords and let a computer loose with the instruction to try these passwords everywhere it can connect to and report back every time it works? Today’s bad guys are automated. They leverage the power of computing to the highest degree. If you use any of these well-known passwords then you’ve made sure they will get into your account if they touch it. Many feel that they are not a target so it’s OK. But automation doesn’t care who you are or how little you have in that online bank account. Automation will simply see if it can get in, and may even be smart enough to drain that little bit in the account. At the end of the day, the automated bad guy has a fat account filled with all the little amounts drained from all the folks who didn’t think they were targets and used bad passwords.”[/su_note]
[su_note note_color=”#ffffcc” text_color=”#00000″]Mark James, Security Specialist at ESET:
“Passwords will always be the single biggest failure point of any network or login and it makes no difference how good your internal procedures are, or how tight your rules and policies are configured, if you’re using weak or easy passwords, you are already on the easy target list. We often hear about data breaches and ask the usual questions around whether the data was encrypted, but it makes no difference if the user is already authenticated due to you using inadequate login credentials. Simple password cracking procedures will take data that has been hacked and leaked, match it against a known word and bingo they now have your password. The hacker will then take those details and try every known online financial login and it’s quite possible they’re going to get a match. Easy to guess passwords have been around for a while, when you are forced to enter log in details for every site you visit sooner or later if you’re not using a password manager or algorithm you’re going to duplicate passwords, you may even suspect it’s not important enough to have its own unique password so 1234567 will do, the bad guys have access to the same lists we do, when passwords appear in these lists they will be in the top most data used for brute force matching, time is important when you’re trying to guess someone’s password, so they want to get it done and move on to the next one as quickly as possible, bear in mind if your using any of these passwords it won’t take a hacker minutes to guess your password, not even seconds, it will take them less time to find your password than it did for you to enter it.[/su_note]
[su_note note_color=”#ffffcc” text_color=”#00000″]Craig Young, Security Researcher at Tripwire:
“Industry best practices dictate that web site operators obfuscate passwords so that they cannot be recovered in the event of a breach. For a properly secure site, this means that an attacker with access to read from the password database can only check if a particular password is correct. If an account is set to use one of these common passwords, the attacker will likely guess it in seconds thereby undermining the security measures taken by the site.”[/su_note]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.