Kaspersky Lab analysis shows that at least half of the ExPetr encryption malware targets were various industrial organizations. The list includes electricity, oil and gas, transportation, logistics and other companies.
ExPetr is a type of encryption malware. Upon infection of victim’s computer it encrypts the hard drive and makes the computer inoperable, showing a message to the victim demanding a ransom.
As Kaspersky Lab researchers have recently discovered, ExPetr is built in a way that means it is completely impossible to decrypt files, even if the ransom is payed. For industrial facilities and critical infrastructure, the consequences of a successful attack using this malware could be devastating.
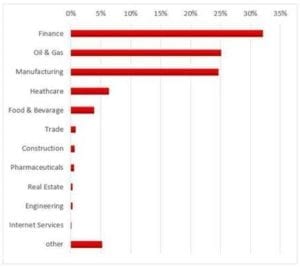
Figure: The distribution of ExPetr targets based on Kaspersky Lab telemetry as of 28 June.
“At the moment it is hard to say whether ExPetr is specifically targeting any particular industry, or if it has hit so many industrial entities coincidentally. However, the nature of this malware is such that it could easily stop the operation of a production facility for a considerable amount of time. That is why this attack is such a vivid example of why industrial entities should be reliably protected from cyberthreats”, said Kirill Kruglov, security expert at Kaspersky Lab.
The global ExPetr outbreak was unleashed on June 27. The malware attacked at least 2000 targets – mostly organizations in Ukraine and Russia. Attacks have also been registered in Poland, Italy, Germany, United Kingdom, China, France and several other countries.
Kaspersky Lab confirmed that the malware shares some strings with Petya and also uses PsExec tools; but has an entirely different functionality to Petya – that is why it has been named ExPetr.
Kaspersky Lab detects the threat as:
- UDS:DangerousObject.Multi.Generic
- Trojan-Ransom.Win32.ExPetr.a
- HEUR:Trojan-Ransom.Win32.ExPetr.gen
Our behavior detection engine SystemWatcher detects the threat as:
- PDM:Trojan.Win32.Generic
- PDM:Exploit.Win32.Generic
According to Kaspersky Lab experts, cybercriminals are shifting their focus from regular users to attacks on organizations. These attacks pose a particular threat to businesses with critical infrastructure as malware activity can crash and stop the production process. The ExPetr incident is yet another example of this worrying trend.
[su_box title=”About Kaspersky Lab” style=”noise” box_color=”#336588″][short_info id=’59584′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



