Just 7 years ago, SAP Security associated with Segregation of Duties only. SAP code issues and platform vulnerabilities were terra incognita even for cybersecurity experts.
The reality showed that it was rather careless. Just within the last 3 years, several highly significant incidents related to the SAP cybersecurity occurred (NVidia breach in 2014, OPM Breach in 2015, and US-CERT alert on an SAP vulnerability). And this is just a beginning, 89% of security professionals anticipate the number of attacks on ERP systems to increase.
A common but true truism states you should be a step ahead of hackers to stay protected. To make accurate predictions, we should first get to know what the state of SAP Cybersecurity today is by revealing the latest data point.
State of SAP Security
To give a full picture of SAP Cybersecurity posture, we focused on 2 aspects: SAP Product Security and SAP Implementation Security.
Product Security
As you may know, the second Tuesday of a month is known as a Patch Tuesday. SAP’s Security Patch Day coincides with Patch Tuesday to allow admins to install all fixes on one scheduled day. On the SAP Security day, the vendor releases a set of internal advisories containing instructions, patches, or both, which dubbed SAP Security Notes.
The number of released security patches released per year has slightly decreased. But it’s too early to rejoice. Surprisingly, it doesn’t mean that the number of the issues has dropped too. The vendor now can fix multiple vulnerabilities in one patch, while 3 years ago each patch addressed a particular one. Anyway, the number of patches is still quite high.
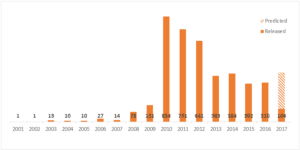
Number of SAP Security Notes released each year
In total, 3910 SAP Security Notes and Support Package Implementation Notes have been published as of April, 2017. An alarming 66% (2601 patches) were assessed by the vendor at High priority and Hot news (SAP’s term for patches addressing the most critical security issues), i.e. about 2/3 of the fixes must be applied as soon as possible.
The most common vulnerability types are XSS, Missing authorization check, and Directory traversal.

SAP Security Notes by type
Vulnerabilities touch almost every SAP module: Customer Relationship Management module takes the leading position among them, following by Enterprise Portal and Supplier Relationship Management solution. However, one shouldn’t underestimate vulnerabilities affecting SAP HANA and SAP Mobile apps. The traditional SAP modules (like ones mentioned first) were introduced about two dozens of years ago, but the first vulnerabilities were discovered just several years ago, meaning that SAP HANA and SAP Mobile apps attracted researchers’ (and, unfortunately, hackers’) attention quicker than the old ones.
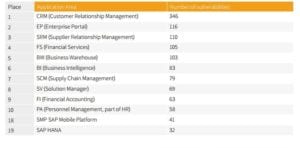
SAP Vulnerabilities by application area (as of mid-2016)
The number of security issues in industry-specific solutions totals 160. SAP for Banking, Retail, Advertising Management, Automotive, and Utilities lead this notorious list.
| Industry Solution | Number of vulnerabilities |
| Banking |
33 |
| Retail | 21 |
| Advertising Management (including Classified Advertising Management) | 27 |
| Automotive | 14 |
| Utilities | 14 |
| Healthcare | 13 |
| Campus Management | 12 |
| Oil and Gas | 10 |
| Defense Forces and Public Security | 6 |
| Aerospace and Defense | 4 |
SAP Vulnerabilities by application area (as of mid-2016)
SAP Implementation Security
This part describes how securely SAP Systems are implemented at the global scale.
The statistics related to exposed SAP web applications can be gained with well-known Google search requests or Shodan, but this approach can give false positive results. Because of that, we used our own scanning method.
As a result of the scan, more than 33000 different SAP web servers were identified (as of the end of 2016).
The research also reveals that most part of legitimate (one that can be exposed to the Internet) SAP application servers exposed to the Internet are located in the USA (2235), India (1000), and Germany (856).
The most interesting and complex research was performed for services which should not be accessible from the Internet, as they are designed only for internal use or require additional network filtration before being directly exposed to the Internet.
There were found almost 25000 such web-exposed SAP systems (namely, SAP Gateway, SAP Message server, SAP HostControl, SAP Visual Admin P4, SAPRouter, SAP MC, SAP Afaria). The risk lies in the fact that vulnerabilities and misconfigurations in such systems are well-known and described in public sources. It may sound even more worrisome, if you take into account that SAP users always slow and backward on installing patches.
Just a simple example – a notorious vulnerability affecting SAP Invoker Servlet intended for managing the J2EE engine remotely. The vulnerability allows bypassing authorization checks for remote access to the service. Last year, US-CERT released an alert that that 36 organizations have failed to correctly install the patch released in 2010 and might fall victim of attacks. The further research revealed that the number of such companies is larger and counts in the hundreds.
This case was widely covered by the media. Despite it got in the public eye, there are still jaw-dropping 922 Invoker Servlets (custom non-intrusive scan) that can be found on the Net.
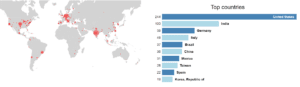 Invoker Servlet – country distribution
Invoker Servlet – country distribution
Near future
Now, when we have drawn a picture what the SAP threat landscape looks like, we can try to forecast what will be on the horizon for the near future.
In short, as SAP Cybersecurity is a part of Cybersecurity, SAP Cybersecurity experts can expect in the coming year to encounter the same trends as the industry in general.
– Cloud solutions. Enterprises are not thinking about migrating applications and data to the cloud, they are doing it. Threats posed by cloud solutions are rather well-known: data breaches, compromised credentials because of broken or missing authentication, exploited system vulnerabilities, to name a few.
As for SAP in particular, the vendor states, that its HANA in-memory technology have 110 million cloud subscribers around the world. The software developer has released more than 50 security patches for SAP HANA and all associated products. Taken together, the attack surface is rather wide.
– Internet of things – Vulnerabilities identified in different wearable devices hit the headlines of the major media a myriad of times in 2016. But what really represents a threat is industrial IoT, or IIot. Such technologies (e.g. sensor data, machine-to-machine communication and automation technologies) have a potential to drastically change the future of the whole vertical. It’s becoming increasingly apparent that IIoT widens attack surface – any device connected to plant floor and at the same time exposed to the Internet (and there are dozens of them) is susceptible to be hacked remotely.
In its portfolio, SAP has a set of solutions for the IoT that includes a platform, applications, underlying and technical services. Moreover, researchers have even already identified several vulnerabilities in modules responsible for plant floor integration (SAP Plant Connectivity, SAP xMII).
– Targeted attack vectors are inextricably linked with the previous item. Enterprises has become a major focus for attacks. Such attacks come in many faces. The first reason is quite banal – hackers look where money is. Industrial espionage conducted by a competitor poses another threat. Hactivists who desire to attract attention a problem often find enterprise hacks an ultimate way to achieve their aim.
The particular risks also depend on the industry. Stealing of personal information in Healthcare, Embezzlement in Financial institutions and even sabotage in industrial entities – all of them are no longer a movie plot about evil hackers.
Taking into account a huge number of vulnerabilities in industry solution from SAP (as aforesaid, 160), it’s safe to say that different kinds of cybercriminals may pay attention to such software security drawbacks, especially ones affecting critical infrastructure in the Oil & Gas, Automotive, and Manufacturing verticals.
- Ransomware dominated cyberthreat landscape in 2016 and is still one of the biggest threat affecting enterprises. Ransom attacks are constantly diversifying and growing in sophistication, new forms of malware appear constantly and no system seems to immune.
SAP is not an exception. For example, researchers have recently identified a remote code execution flaw in the SAP Windows client which opens the door for ransomware attacks targeting enterprises using SAP. Fortunately, there is no evidence of this vulnerability being exploited. With more than 345,000- customers and millions of individual users of SAP GUI, this vulnerability opens the door to mass exploitation.
[su_box title=”About Darya Maenkova” style=”noise” box_color=”#336588″][short_info id=’101913′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



