When I turned 25, I saw this as a pretty big milestone in my life. At 25 years old, I felt like a true adult – I was now all grown up. I was educated, employed, experienced and stable. But when I look back, the journey from childhood to adulthood was really far from over at the age of 25. I still had so much growing to do – so much learning and so much to experience.
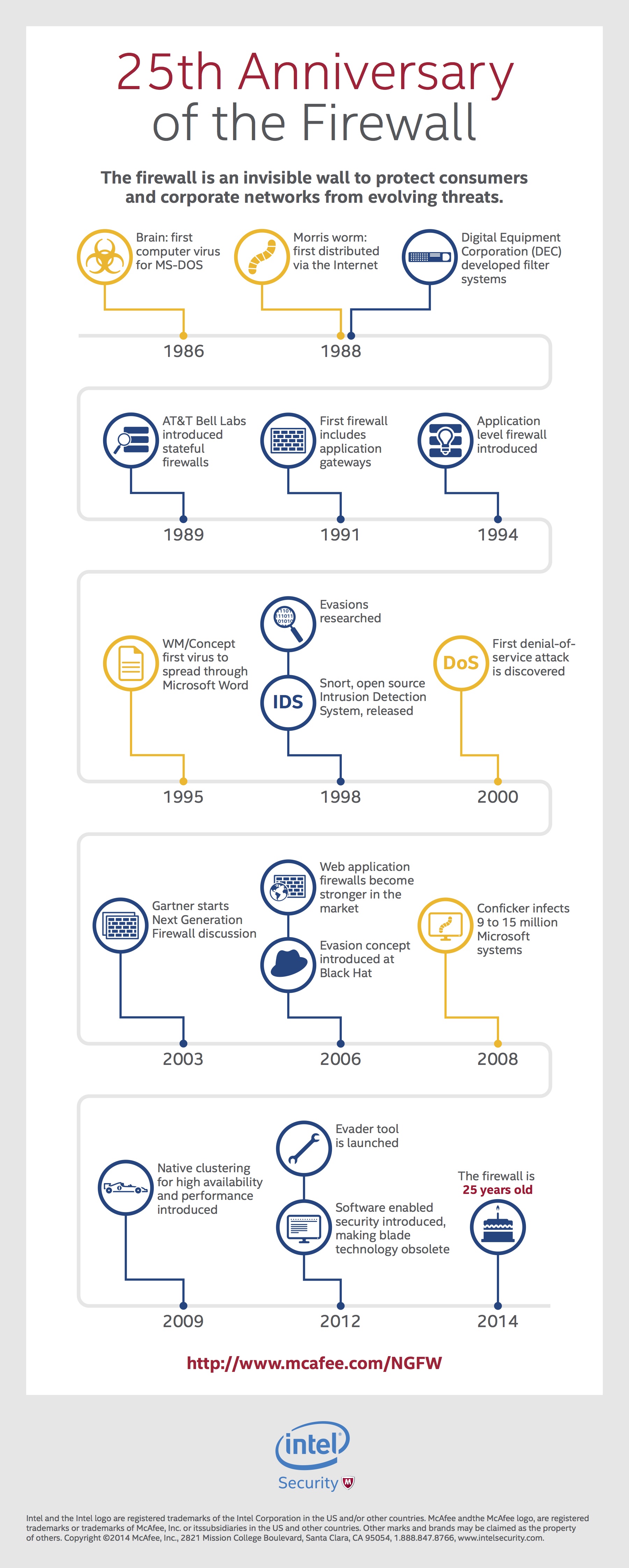
I think about my own progress as I click open the 25th Anniversary of the Firewall Infographic that creatively depicts the ‘lifetime’ of the firewall. It’s a very interesting look at the evolution of a technology that we probably all thought, at one point, could never be outdone. With each new development, we were sure we’d nailed it. But, similar to the way I feel looking back on my mid-twenties, I’m not convinced the firewall is all grown up just because it’s been around for 25 years.
If you take a moment to scan the infographic and become reacquainted with the history of the firewall, you’ll notice its introduction and evolution coincide with certain security events like these:
– 1995: WM/Concept first virus to spread through Microsoft Word
– 2000: First denial-of-service attack discovered
– 2008: Conficker infects 9-15 million Microsoft systems
The firewall has had a great evolution, but its development and growth really occurred with each security breach discovered. These events triggered security developers to react with more and more advanced firewall technology. Here’s a snapshot:
– 1998: Evasions researched
– 2009: Native clustering for high availability and performance introduced
– 2012: Software enabled security introduced, making blade technology obsolete
Just because I don’t think the firewall is all grown up, however, doesn’t mean I think it’s immature. It just happens to be part of a new generation that’s embarking on a journey of self-discovery. For those of you seeped in the technology world, I’m sure you know where I’m going with this analogy. Starting around 2003, Gartner began discussions around the so-called Next Generation Firewall – a firewall with the ability to ward off more sophisticated threats through deep inspection capabilities that went beyond traditional firewall and packet filtering and added a potent new security element: contextual awareness.
More than a year before the firewall was ready to celebrate its big milestone, McAfee was full-steam ahead with its Next Generation Firewall development efforts which integrate application control, intrusion prevention system (IPS), and evasion prevention into a single, purpose-built solution. In fact, ours is the only next-generation firewall solution to combine anti-evasion security with enterprise-scale availability and manageability. In addition, it’s flexible – with the ability to change from a next-generation firewall to a L2 firewall, IPS, and firewall/VPN.
Plus, from a holistic security standpoint, McAfee is leading the way. We are connecting an advanced McAfee Next Generation Firewall with SIEM functionality and ePolicy Orchestrator, Endpoint Security, Advanced Threat Defense, Global Threat Intelligence (GTI) and Enterprise Authentication. The future of network security requires a holistic system that can combat the threats we continue to see growing and morphing and sneaking past traditional defenses and point solutions.
So, yes, the firewall is pretty mature and I’m excited to say, “Cheers and Happy 25th Birthday Firewall.” But frankly, I’m more excited about the next 25 years and the part McAfee will play in its growth and development.
By Pat Calhoun, General Manager of Network Security, McAfee
About McAfee
 McAfee, a wholly owned subsidiary of Intel Corporation (NASDAQ: INTC), empowers businesses, the public sector, and home users to safely experience the benefits of the Internet.The company delivers proactive and proven security solutions and services for systems, networks, and mobile devices around the world. With its visionary Security Connected strategy, innovative approach to hardware-enhanced security, and unique global threat intelligence network, McAfee is relentlessly focused on keeping its customers safe.
McAfee, a wholly owned subsidiary of Intel Corporation (NASDAQ: INTC), empowers businesses, the public sector, and home users to safely experience the benefits of the Internet.The company delivers proactive and proven security solutions and services for systems, networks, and mobile devices around the world. With its visionary Security Connected strategy, innovative approach to hardware-enhanced security, and unique global threat intelligence network, McAfee is relentlessly focused on keeping its customers safe.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.