Almost every website and app relies on a username and password combination to authenticate users. And that system, which the Internet is built on, is crumbling. There are several factors that together are diminishing the effectiveness of passwords. First, computing power is increasing exponentially; the computing power needed to compromise a password through a brute-force attack is increasingly available to cyber criminals. As a result, users are recommended to use long, complex passwords that take longer to crack. But with passwords routinely stolen in large cyber attacks, like the Adobe breach that compromised 38 million passwords, experts recommend that you change your passwords frequently.
But most people find long, complex passwords difficult to remember and annoying to type in each time they sign in to a website or app. So they fall back on using shorter, easier to remember (i.e. easier to compromise passwords). Even security experts are not immune to the siren call of using simple, unsecure passwords. Hacking Team, a company based in Italy that specializes in creating surveillance software used by governments, was recently the victim of an attack that resulted in 400 GB of valuable data stolen. Included in that data was the Firefox password vault of Christian Pozzi, a Senior System and Security Engineer for the company.
One of the major headlines following the attack was that Pozzi, like many users, employed passwords so devastatingly simple that they could easily be guessed. He used the password “P4ssword” for many important accounts, including not just social media sites but also banking websites. Of course, most hackers know that people often substitute numbers for letters (like 4 for “A”) and incorporate this knowledge when they attempt to compromise accounts, making these types of passwords very unsecure.
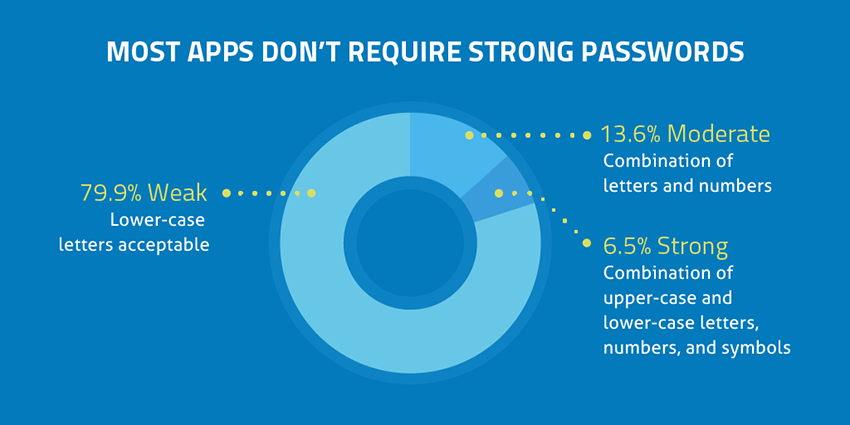
The other reason users haven’t adopted complex passwords is that they simply aren’t required to do so. A recent analysis of over 12,000 different cloud services found that 79.9% of cloud services allow for the use of weak passwords. This leaves only 20.1% requiring strong or moderate passwords with a combination of upper-case letters, lower-case letters, numbers, and symbols.
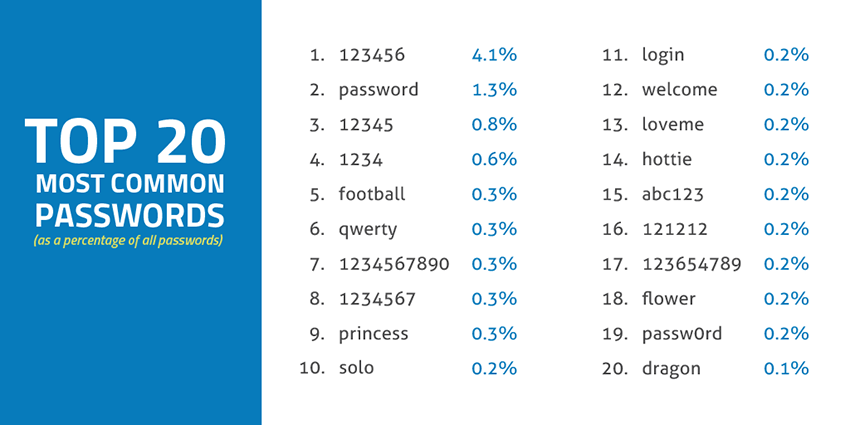
 Many people erroneously assume that memorizing one strong password that they use across websites and apps will help. In fact, Joseph Bonneau from the University of Cambridge, determined that an astonishing 31% of users reuse the same password for different accounts putting personal information at risk. Skyhigh Networks analyzed over 11 million compromised passwords for sale on the Darknet and identified the 20 most common passwords used today. These 20 passwords are so common that they’re employed by 10.3% of users! Using any of these passwords is akin to leaving the keys to your house under the welcome mat.
Many people erroneously assume that memorizing one strong password that they use across websites and apps will help. In fact, Joseph Bonneau from the University of Cambridge, determined that an astonishing 31% of users reuse the same password for different accounts putting personal information at risk. Skyhigh Networks analyzed over 11 million compromised passwords for sale on the Darknet and identified the 20 most common passwords used today. These 20 passwords are so common that they’re employed by 10.3% of users! Using any of these passwords is akin to leaving the keys to your house under the welcome mat.
 Like I mentioned above, security experts recommend that you use passwords that are complex and hard to crack (and remember). In order to keep track of all these complex, unique passwords for all of your different accounts, users are turning to password vaults like LastPass to store these passwords. Like any other site, people may wonder how secure their password vault is. In a recent breach, hackers stole encrypted master passwords from LastPass. Fortunately for LastPass users, it looks like hackers were not able to decrypt the master passwords that provide access to user accounts, and the passwords stored in their vaults were not compromised.
Like I mentioned above, security experts recommend that you use passwords that are complex and hard to crack (and remember). In order to keep track of all these complex, unique passwords for all of your different accounts, users are turning to password vaults like LastPass to store these passwords. Like any other site, people may wonder how secure their password vault is. In a recent breach, hackers stole encrypted master passwords from LastPass. Fortunately for LastPass users, it looks like hackers were not able to decrypt the master passwords that provide access to user accounts, and the passwords stored in their vaults were not compromised.
More people are recognizing the situation with passwords is a catch-22 and passwords alone are not enough. More protection is needed to keep valuable information secure, and a second security protocol may be the next step. To protect users and their information following the breach, LastPass enabled multi-factor authentication for all users. In one variation of multi-factor authentication, after signing in with a username and password the users receives a text message with a code they must enter before gaining access, proving their identity. This additional form of authentication significantly improves the security of accounts. However, only 15.4% of cloud services offer multi-factor authentication.
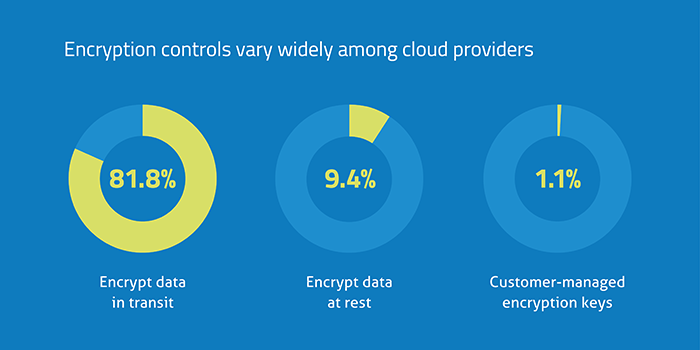
Changing the way data is encrypted could also make data in cloud services more secure, since it would require more than just a password to access the data. In a recent study of 12,000 cloud services it was discovered that 81.8% of cloud service providers encrypt data as it moves between end users to cloud. Which is a great way to protect data as it is in transit. However, only 9.4% of cloud services encrypt at rest. It may surprise you that some of the biggest names in the industry don’t encrypt data at rest. PayPal, for example, is a one of the largest cloud services with access to sensitive financial data that does not encrypt data at rest.
 The question that many ask is, “who should be encrypting the data as it is stored in cloud services?” One option is to rely on the cloud providers to encrypt data stored in their own cloud service, and push cloud providers that don’t encrypt data to add this capability. However, in this model you give the cloud provider access to your sensitive information. Don’t forget that under the USA PATRIOT Act, the government can request copies of you data stored by a cloud provider. The cloud provider is legally required to hand over your information and can be legally barred from telling you. And in the case of a compromised account, your data is vulnerable.
The question that many ask is, “who should be encrypting the data as it is stored in cloud services?” One option is to rely on the cloud providers to encrypt data stored in their own cloud service, and push cloud providers that don’t encrypt data to add this capability. However, in this model you give the cloud provider access to your sensitive information. Don’t forget that under the USA PATRIOT Act, the government can request copies of you data stored by a cloud provider. The cloud provider is legally required to hand over your information and can be legally barred from telling you. And in the case of a compromised account, your data is vulnerable.
A preferable approach would be to encrypt data using encryption that you control, before data is ever stored in the cloud. Only 1.1% of cloud providers offer this capability today as part of their service. But you can also use a third-party encryption solution in cases where the cloud provider doesn’t offer this type of encryption. This is an increasingly attractive option for many users. On the consumer side, there are many free offerings that allow you to encrypt data you upload to services like Dropbox, and detailed guides on how to do this.
Authentication that relies on passwords alone is quickly becoming extinct. We’re now living in a post-password era that requires the use of a multi-layered security to prevent unauthorized access to information online.[su_box title=”About Harold Byun” style=”noise” box_color=”#336588″] Harold Byun is VP of product management at Skyhigh Networks. Prior to Skyhigh, he worked at MobileIron, where he focused on mobile application delivery and security. Prior to MobileIron, he led the product management group at Zenprise (acquired by Citrix), where he launched their mobile DLP product and cloud offering to market. He also worked with the Vontu/Symantec DLP group and is the co-inventor on a patent filed for security risk visualization and scoring.[/su_box]
Harold Byun is VP of product management at Skyhigh Networks. Prior to Skyhigh, he worked at MobileIron, where he focused on mobile application delivery and security. Prior to MobileIron, he led the product management group at Zenprise (acquired by Citrix), where he launched their mobile DLP product and cloud offering to market. He also worked with the Vontu/Symantec DLP group and is the co-inventor on a patent filed for security risk visualization and scoring.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



