The ransomware is definitely spreading via EternalBlue exploit just like WannaCry. People have found the code in the malware and have seen the EternalBlue exploit traffic on the network. There are additional spreading vectors that use harvested credentials from machines compromised with EternalBlue. These are used to connect to and run the malware on fully patched machines.
The easiest and best way to prevent the EternalBlue exploit from working is to run Windows Update. Because WannaCry kill switch worked, the pain stopped, and many orgs did not complete patching their Windows. This shows the day to day fire drill that many IT teams work under and the reality that patching in many organisations is hard. Once they heard that WannaCry was stopped they moved on to other more pressing work.
This attack seems to be hitting large industrial companies like Maersk shipping company and Rosneft oil company. These organisations typically have a challenge patching all of their machines because so many systems cannot afford to have any down time. Airports and hospitals also have this challenge.
This attack has similar characteristics of Petya, but I believe Kaspersky is right that it is not in fact Petya and is completely new. Upon initial submission of this ransomware to VirusTotal only two anti-virus vendors were able to detect it– and so it is likely that many systems are defenceless. This shows how easy it is for malware writers to bypass endpoint security by modifying any code they are reusing.
After many organisations updated their products to detect WannaCry, many organisations may have had a false sense of security, thinking that those updates would prevent all related attacks in the future– this is obviously an assumption that businesses cannot afford to make.
There are reports that there is an additional spreading mechanism that uses the stolen credentials from compromised machines to spread to even patched machines. If this is true it will mean that organisations with just a few unmatched machines could still have a massive ransomware issue across their whole windows infrastructure.
It is emerging that one of the initial vectors of attack was a Ukrainian software company. They posted a notice: http://www.me-doc.com.ua/vnimaniyu-polzovateley
It translates to:
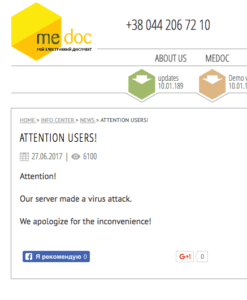
It is likely the attackers compromised their infrastructure and sent the malware through them somehow. Perhaps as a software update!
The non-EternalBlue vector is to use stored windows sessions harvested from compromised machines to connect to patched machines as a valid windows users. This is a common technique used for lateral movement within organisations using Windows Active Directory. In a worst case scenario if a Domain Admin had logged into an infected machine previously then the Domain Admins credentials can be used to infect all machines on the network. This uses the remote command interfaces of WMI or PsExec which are standard windows mechanisms for executing commands remotely.
The malware is spreading with worm behaviour and doesn’t require any human interaction.
[su_box title=”About Chris Wysopal” style=”noise” box_color=”#336588″][short_info id=’102703′ desc=”true” all=”false”][/su_box]






