Much has been said about the threat posed by the Internet of Things (IoT). Considered the “barbaric horde” of under-protected connected devices, all of them are just waiting to be compromised by any half-competent hacker.
While we haven’t yet had the chance to intercept any refrigerator-mounted malware, over the years we‘ve seen our share of IoT botnets, with CCTV ones being among the most common. We first warned about them in March 2014, when we became aware of a steep 240 percent increase in botnet activity on our network, much of it traced back to compromised CCTV cameras.
Not surprising, given that CCTV cameras are among the most common IoT devices. Reports show that in 2014, there were 245 million surveillance cameras operating around the world. And this only accounts for the professionally installed ones. There are likely millions more that were installed by unqualified professionals, with even fewer security precautions.
These numbers, and the lack of cybersecurity awareness on the part of many camera owners, are the reasons why CCTV botnets are some of our oldest foes.
Still, old foes have the capacity to surprise, as we were recently reminded, when one of our clients was targeted by repeated HTTP flood attacks.
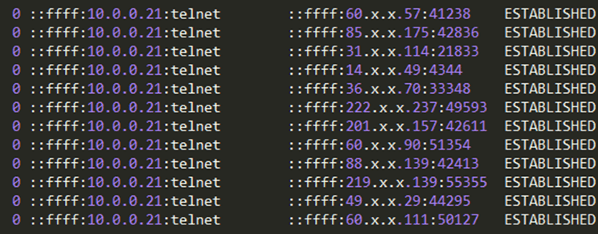
The attack was run of the mill, peaking at 20,000 requests per second (RPS). The surprise came later when, upon combing through the list of attacking IPs, we discovered that some of the botnet devices were located right in our own back yard.
Further investigation of the offending IPs showed that they belonged to CCTV cameras, all accessible via their default login credentials. And that’s not all. Looking through the camera lens we also spotted a familiar sight—a storefront in a mall located not five minutes away from our offices!
The opportunity for some community service was too good to pass up, so we hopped in our cars and took a trip to the mall.
We were able to meet with the store owners, show them how their CCTV cameras were abused to attack our clients and help them clean the malware from the infected camera’s hard drive.
As we did, we witnessed it coughing out attacking requests up to the very last moment.
Attack Details
As noted, this assault consisted of HTTP GET floods that peaked at around 20,000 RPS, with its traffic originating from roughly 900 CCTV cameras spread around the globe. Their target was a rarely-used asset of a large cloud service, catering to millions of users worldwide.

The malware we found inside them was an ELF binary for ARM named (.btce) a variant of the ELF_BASHLITE (a.k.a. Lightaidra and GayFgt) malware that scans for network devices running on BusyBox, looking for open Telnet/SSH services that are susceptible to brute force dictionary attacks.
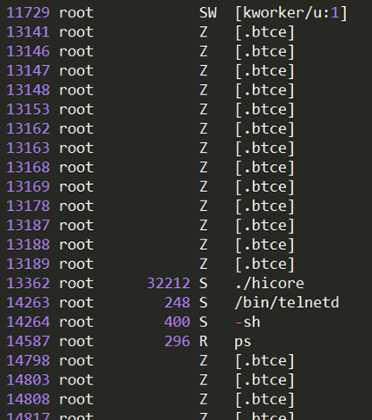

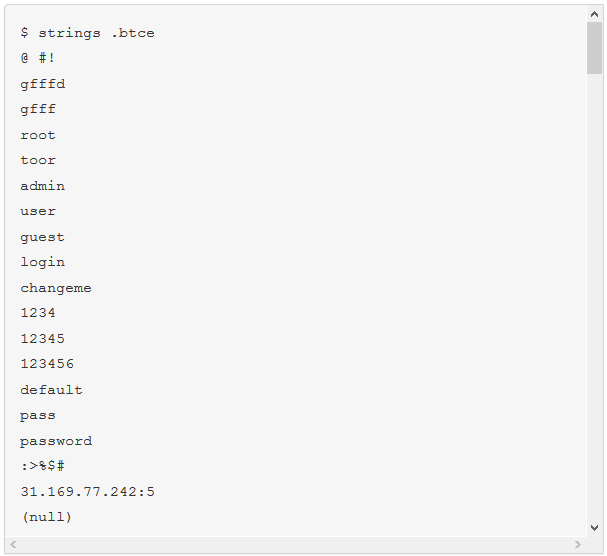

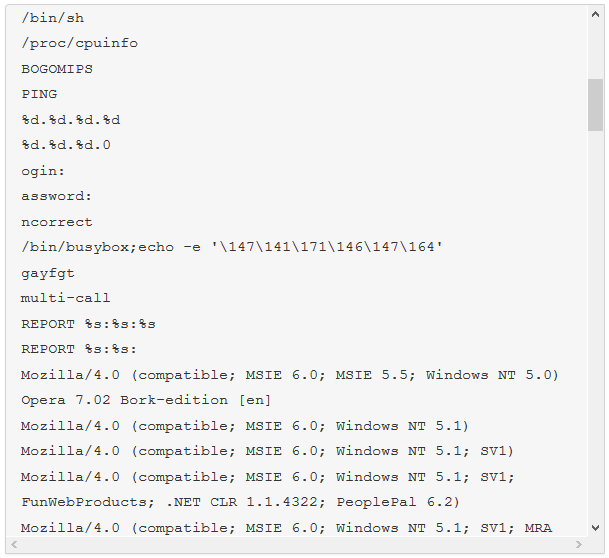

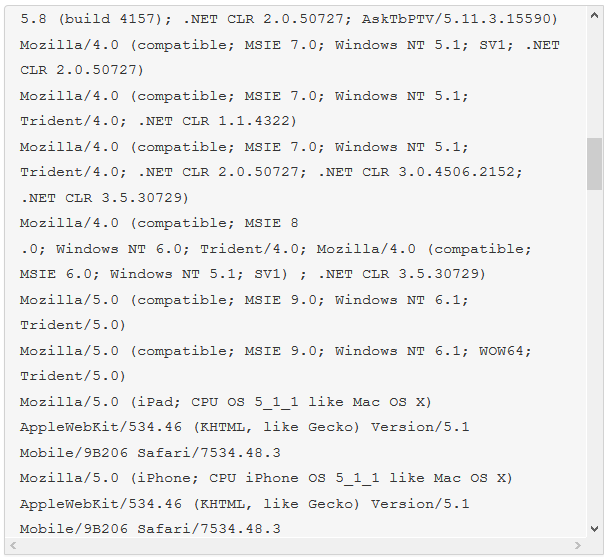

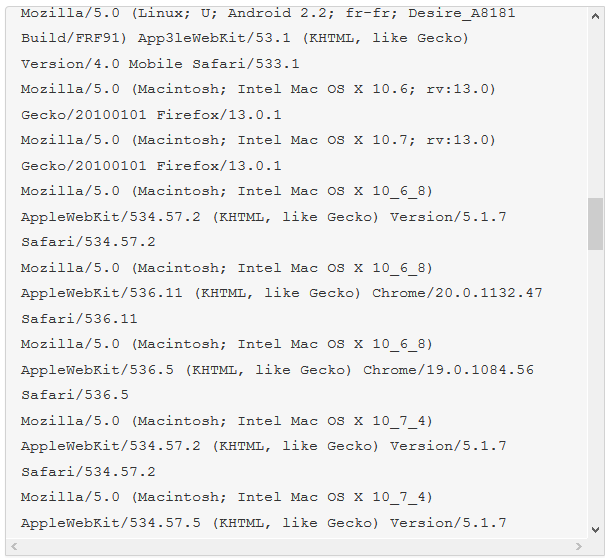

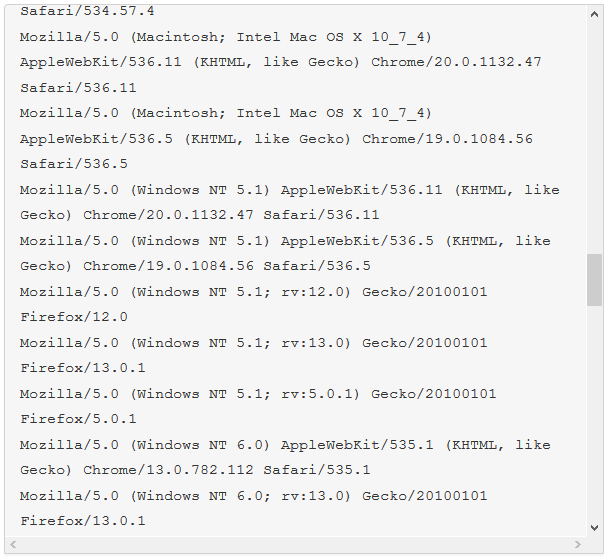

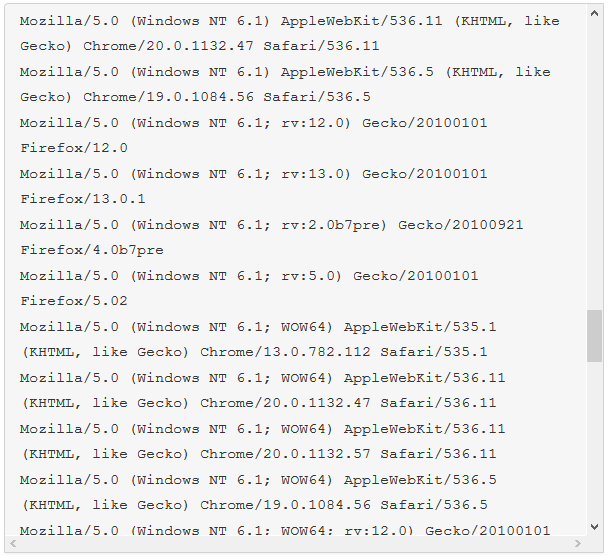

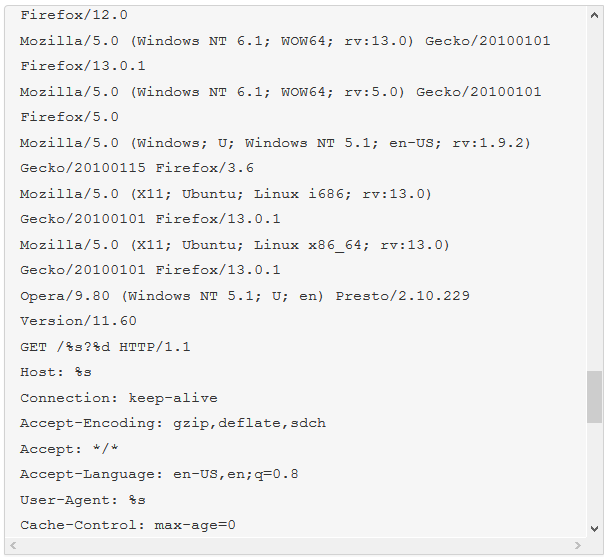

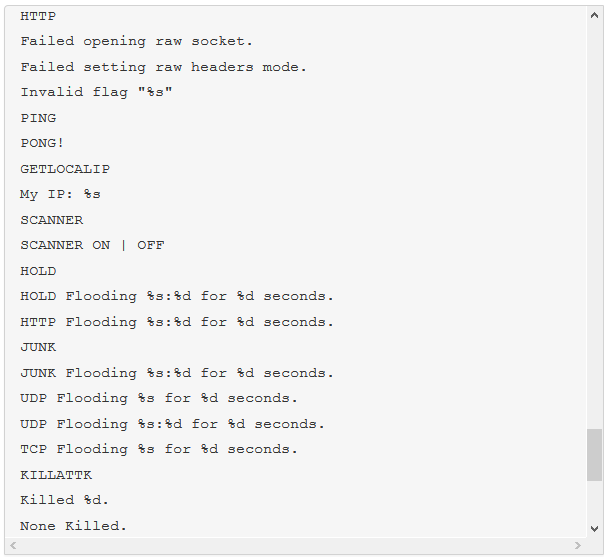

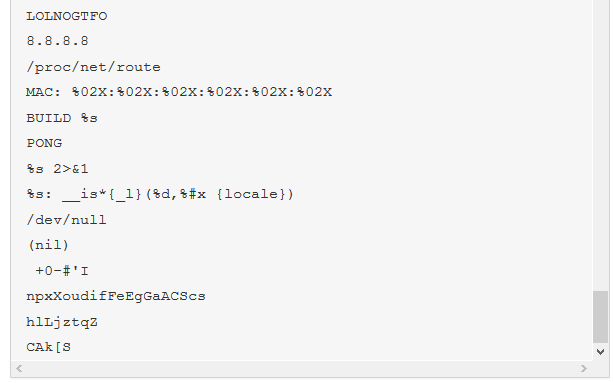

We hope our story will raise awareness about the importance of basic security practices—as well as the threat posed by unsecured connected devices. Even as we write this article, we are mitigating another IoT DDoS attack, this time from an NAS-based botnet. And yes, you guessed it, those were also compromised by brute-force dictionary attacks.
Whether it is a router, a Wi-Fi access point or a CCTV camera, default factory credentials are there only to be changed upon installation. Please do so—or else you too may get a visit from the Incapsula team.[su_box title=”About incapsula” style=”noise” box_color=”#336588″]