A highlight of CERT UK’s first quarterly report was the success of efforts to ‘sinkhole,’ or seize control of command and control (‘2c’) domains used by GameOver Zeus and Cryptolocker to ‘phone home.’
David Dagon, co-founder of Damballa and postdoctoral Fellow at Georgia Tech, worked with UK agencies to register all co.uk domains used by CryptoLocker and sinkhole them in perpetuity. Sinkholing prevents infected devices from making contact with botmasters to receive malicious instructions.
“Georgia Tech’s contribution involved operating the co.uk Cryptolocker sinkhole for epidemiological measurement and the notification of victims.” Meanwhile, security company Damballa provided the resources and intelligence for the sinkhole.
Dagon is cautiously optimistic about the results of Operation Tovar, explaining that the security community has bought some time.
He continues, “Eliminating every last viral installation on the Internet may prove elusive. There may be some infections because of their size or impact that require effectively perpetual blocking and sinkholing. Others will require less resources. We are collectively determining the appropriate amount of public resource and private action required of Cryptolocker and GOZ.”
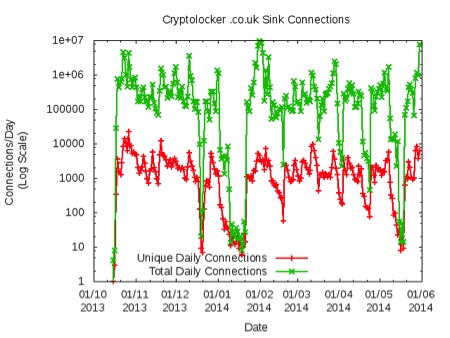 The Cryptolocker sinkhole would record as many as 50K unique IPs per day, to as few as a hundred. The variability is due to the fact that Cryptolocker is dropped by other infections (GameOverZeus), and is a means of harvesting victims rather than self-propagating to create an exploitation framework. (Source: David Dagon/Damballa)
The Cryptolocker sinkhole would record as many as 50K unique IPs per day, to as few as a hundred. The variability is due to the fact that Cryptolocker is dropped by other infections (GameOverZeus), and is a means of harvesting victims rather than self-propagating to create an exploitation framework. (Source: David Dagon/Damballa)
In a blog, Dagon describes Operation Tovar as the first intergovernmental exercise in epidemiology and public health. He explains that the operation is the “start of a new era in cyber public health.”
“Botnets must be managed as mass infections. The individuals behind them must be held accountable. Cleanup is largely an opt-in experience. This is what cyber public health looks like today. Instead of treating Operation Tovar a successful takedown or failed attempt, I suggest that we recognize the larger process at work. We are collectively figuring out how cyber epidemiology and botnet remediation work together on a global scale.”
Brian Foster, CTO of Damballa, led the company’s research and development team responsible for developing detection engines capable of discovering advanced threats like CryptoLocker without ever having to see the malware file. CryptoLocker activity was first detected by the team in the summer of 2013. They ultimately wrote the code needed to sinkhole the co.uk domains.
Since Operation Tovar, Foster said his team has seen a limited resurgence of reengineered versions of GameOver Zeus malware. So far, however, the effectiveness of Cryptolocker and Zeus sinkholes has been encouraging, Foster says.
Dagon concurs and adds that “unlike biological infections, cyber defenders face one key challenge: well-funded, agile, adaptive human adversaries, who can constantly generate new threats. Experience tells us that we can expect new botnets. It may even be that after a period of time, the GameOver Zeus and Cryptolocker botnets will return under new ownership. We can still apply the lessons learned from Operation Tovar to continue to improve the management of mass infections.”
By David Dagon, co-founder of Damballa
 Damballa helps enterprises prevent loss of their data, intellectual property, finances and reputation due to a cyber-security breach. We are innovators in advanced threat protection and containment. That means our systems help stop malicious behavior from damaging your business.
Damballa helps enterprises prevent loss of their data, intellectual property, finances and reputation due to a cyber-security breach. We are innovators in advanced threat protection and containment. That means our systems help stop malicious behavior from damaging your business.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



