In the earlier article “Secrity, Democracy And Digital Identity” , we made clear that we should look for ‘something other than the text password’ in the domain of ‘Secret Credentials’ and referred to the proposition of Expanded Password System. We would like to talk more about what Expanded Password System specifically offers in this article.
What our Remembrance Brings for Digital Identity
In the matrix below, there are several known images. We can easily find all of them right away. Or, rather, these known images jump into our eye. And, only we are able to select all of them correctly. This is Expanded Password System.
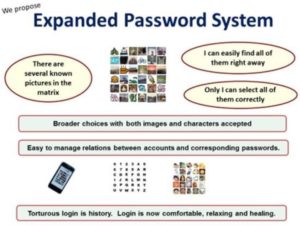
We can use both images and characters. It’s easy to manage the relation between accounts and the corresponding passwords – Comfortable and even fun!
The idea of using pictures for passwords is not new. It’s been around for more than two decades but the simple forms of pictorial passwords were not as useful as had been expected. Unknown pictures we manage to remember afresh are still easy to forget or get confused, if not as badly as random alphanumeric characters.
Expanded Password System is new in that it offers a choice to make use of known images that are associated with our autobiographic/episodic memories.
Since these images are the least subject to the memory interference, it enables us to manage dozens of unique strong passwords without reusing the same password across many accounts or carrying around a memo with passwords on it. And, handling memorable images makes us feel comfortable, relaxed and even healed. Torturous login is history.
Well, let’s talk about some major problems that use of our own episodic memory enables us to solve.
Relation of Accounts with Passwords
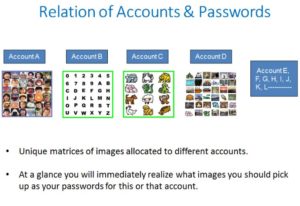
Being able to recall strong passwords is one thing. Being able to recall the relation between accounts and the corresponding passwords is another.
When unique matrices of images are allocated to different accounts, those unique image matrices will be telling you what images you should pick up as your password for this or that account.
When using images of our episodic memories, Expanded Password System will thus free us from the burden of managing the relation between accounts and the corresponding passwords.
Broad Choice
So far, only texts have been accepted. It was, as it were, we have no choice but to walk up a long steep staircase. With Expanded Password System, we could imagine a situation that escalators and elevators are provided along with the staircase. Or, some of us could think of all those ladders we have for climbing in Donkey Kong.
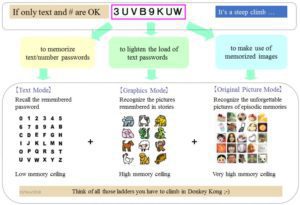
Where we want to continue to use text passwords, we could opt to recall the remembered passwords, although the memory ceiling is very low, Most of us can manage only up to several of them.
We could opt to recognize the pictures remembered in stories where we want to reduce a burden of textual passwords. The memory ceiling is high, that is, we would be able to manage more and more of them.
Where we choose to make use of episodic image memory, we would only need to recognize the unforgettable images, say, known images. There is virtually no memory ceiling, that is, we would be able to manage as many passwords as we like, without any extra efforts.
Enhanced Entropy
Hard-to-break text passwords are hard-to-remember. But it’s not the fate of all the secret credential. It would be easily possible to safely manage many of high-entropy passwords with Expanded Password System that handles characters as images.
Each image or character is presented by the image identifier data which can be of any length. Assume that your password is “CBA123” and that the image ‘C’ is identified as X4s& eI0w, and so on.
When you input CBA123, the authentication data that the server receives is not the easy-to-break“CBA123”, but something like X4s&eI0wdoex7RVb%9Ub3mJvk”, which could be automatically altered periodically or at each access where desired
Brain-Computer-Interface and Its Security
A simple brain-monitoring has a problem in security. The authentication data, if wiretapped by criminals, can be replayed for impersonation straight away. Therefore the data should desirably be randomized as the onetime disposable ones.
An idea is that the authentication system allocates random numbers or characters to the images shown to the users. The users focus their attention on the numbers or characters given to the images they had registered.
The monitoring system will collect the brain-generated onetime signals corresponding to the registered images. Incidentally, the channel for showing the pictures is supposed to be separate from the channel for brain-monitoring.
If intercepting successfully, criminals would be unable to impersonate the users because the intercepted data has been disposed of.
No-Cost 2-Factor Authentication
A very strong password supposed to not be remembered and written down on a memo should be viewed as ‘what we have’, definitely not ‘what we remember’, so it could be used as one of the two factors along with a remembered password.
We could then turn a boring legacy password system into a two factor authentication system at no cost, just by verifying two passwords at a time, one volitionally recalled and the other one physically possessed.
When those two different passwords are used as two factors, we could rely on the strength of a remembered password against physical theft and the strength of a physically possessed long password against brute force attack, although it is not as strong against wiretapping as token-based solutions armed with PKI or Onetime Password.
This configuration could be viewed just as a thought experiment or could actually be considered for practical application in between a single factor authentication and a costly heavily-armored 2-factor scheme, or, as a transition from the former to the latter.
It goes without saying that Expanded Password System could be brought in for generating a remembered high-entropy password.
Hitoshi Kokumai
President, Mnemonic Security, Inc.
Profile: Advocate of ‘Identity Assurance by Our Own Volition and Memory’, Hitoshi Kokumai is the inventor of Expanded Password System that enables people to make use of episodic image memories for intuitive and secure identity authentication. He has kept raising the issue of wrong usage of biometrics and the false sense of security it brings for 17 years. Mnemonic Security Inc. was founded in 2001 by Hitoshi Kokumai for promoting Expanded Password System. Following the pilotscale operations in Japan, it is seeking to set up the global headquarters.
Appendix – Fighting Threats to Security and Democracy from Within
Where the digital identity platform was built without the secret credentials made from our memory, we would have to see the necessary level of security lost.
Where the secret credentials, for which our will/volition is indispensable, are removed from the digital identity platform, we would have to see erosion of democracy that our ancestors have won through heavy sacrifices.
On this front we are not optimistic; too few people are taking the correct course towards the correct objectives. Too many people, with professionals, researchers, politicians and journalists included, are badly distracted and straying off the course.
More and more people are expected to join our efforts.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


