Google recently created a new quiz to test user knowledge against email phishing attacks, showing how easy it is to be fooled by a scam you think is coming from a trusted source. From fake support emails with malicious links to folders of photos to download from unknown sources, corporate users are getting better and better at spotting fake emails, and security tools are primed to catch them with advanced technology.
But outside of the typical phishing and spear-phishing emails, attackers are using the browser more and more to fool users into clicking malicious links, entering login credentials, or downloading malware. From the examples below, would you be fooled by any of these phishing pages? When dealing with information on the fly, it’s easy to get tricked if you think your system is compromised or if you come across an amazing tech deal or contest. Take a look at some of the major types of non-email phishing scams and see how difficult it is to spot the real thing from the fake.
Malicious browser extensions
Browser extensions by design have full access to most of the browser’s resources and information being entered and rendered. It was just a matter of time before cybercriminals realized that injecting malicious code inside browsers disguised as benign looking browser extensions would not only give them unlimited access to all the data within a browser, but also provide them with much needed cover from security systems that are designed to catch only malware executables and software exploits.
Cybercriminals can easily infect hundreds of thousands of computers with malicious browser extensions that steal login credentials, mine cryptocurrencies, or engaged in click fraud – and scarily they can sometimes do it with an extension that is hosted in Google’s official Chrome Web Store.
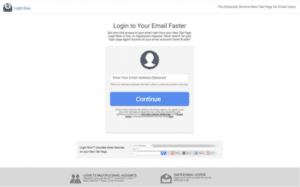
Credential stealing
Credential stealing is the oldest form of phishing attack. It’s designed to trick the user into giving up their login credentials by representing a clone of a legitimate website. These replica pages often leverage reputable brands such as Dropbox, Yahoo, and Microsoft and some come complete with functional “password reset” options and even security questions for peace of mind. The result is a realistic looking login page for an unsuspecting user that may stumble upon it from a search result.
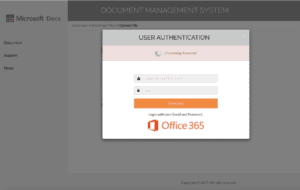
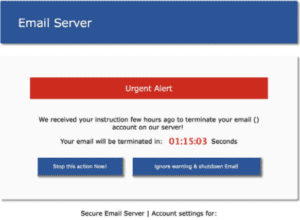
Technical support scams
Technical support scams use scare tactics to trick gullible victims into believing that their computer has either crashed or that a virus has been detected on their computer. These scams try to lure victims into calling a fake technical support hotline which, if successful, can lead to telephone fraud. The goal is usually to gain remote access to the system and to collect sensitive user information. These scammers may also ask their victims to pay for their fake support.
Once the hacker is connected, they may install malware for remote access or data exfiltration, or they can disable endpoint protection or re-configure them to whitelist, trust or ignore tools that the scammer may want to use.
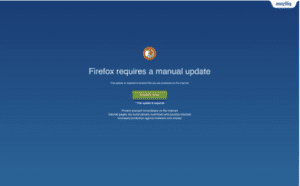
Rogue software
These type of phishing attacks usually trick users into downloading fake system cleaners and anti-virus tools by showing fake infections and malware activities on their computer or device. In some case, these types of phishing attacks lure their victims into installing fake videos players with an offer to watch a cool video.
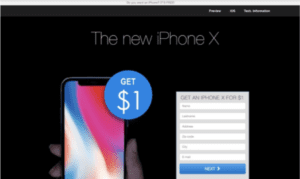
Gift and prize scams
Prizes are universally loved – who doesn’t love free stuff? These type of phishing attacks create a sense of excitement for their victims before asking them for sensitive information in order to claim a reward. In a recently observed attack, the victim is promised one of several possible prizes. After spinning the wheel to win, the user will be asked to log-in to Facebook to claim his prize. However, the Facebook login page is fake and under control of the attacker. The purpose of the scam is simply to capture the user’s Facebook login credentials.
Once they have your login credentials, they can try them at other sites – such as banking sites – since many people use the same login credentials across multiple websites.
What You Can Do to Avoid the Lures
The takeaway from Google’s quiz was not just if you could spot the bad emails, but also how to make sure not to get fooled in the future. With that goal in mind, here are a few simple steps you can take to help prevent getting phished by look-alike sites next time you are browsing the web.
- Check all URL links closely by hovering over them or using a long press. Look for misspellings, use of a number in place of a letter, short URLs, the addition of an extra word, anything other than a .com or .org extension, or anything that appears suspicious.
- Be wary of pop-ups that are immediately displayed on a website requesting a user name and password. Phishing scams can direct targets to a legitimate website and then use a pop-up to gain account information.
- When visiting support pages, search for them from the website home page with the original URL that you know is valid. Hackers can purchase similar-sounding domains or add addition words to the legitimate URL name to create fake sites.
Ultimately, phishing threats fundamentally try to exploit the user’s trust in global brands with the end goal of getting them to wittingly (or unwittingly) permit socially engineered malware to get onto his or her system. Even with user training as a critical step in avoiding company breaches via phishing, IT teams should have the tools in place to detect these zero-hour attacks in real time, before they even reach the users.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



