Every organization has data flowing into and out of the organization. Along with any data comes the risk of malware. To protect against threats, most organizations implement anti-malware solutions at different entry points, such as email, web, and portable media. However instead of tackling each entry point as a separate anti-malware project, organizations should treat secure data workflow as a complete process that addresses data cyber security in the company as a whole. By combining the different elements into one process, organizations obtain a complete overview, decreasing the chance of overlooking things and allowing them to benefit from synergies and increase efficiency.
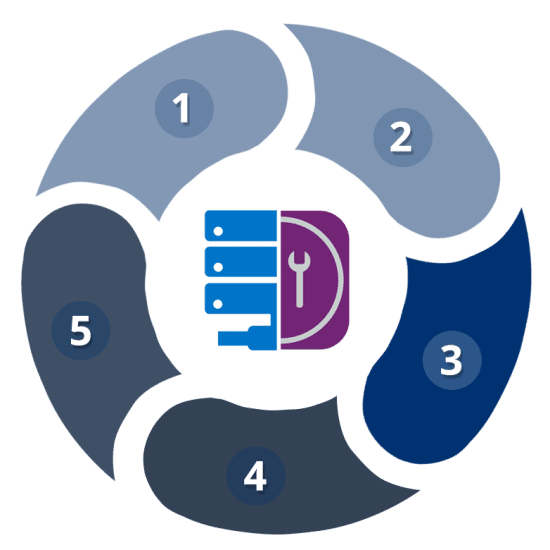
So, how can you implement a secure data workflow in your organization? The secure data flow planning process consists of five steps:
- Identify the Different Data Workflows
Organizations need to determine where data is coming from and what the destinations are. For example, data that comes in through email is destined for employees or contractors. Data that comes in through the web is destined for desktops, mobile devices, USB devices, and so on. Each data flow in the company needs to be defined in this way.
- What File Types Are Needed by Users?
Secondly, organizations need to determine which users need which types of files. For instance does the accounting department need to receive executable or media files? Probably not. Do they need to receive PDF and Word documents? Yes. However, the IT department should have access to exe files. Similarly, the marketing department might need access to media files to complete their daily tasks.
- What Threats Are Possible?
Some file types are more dangerous than others. Executable files can contain viruses. PDF and Word documents can include embedded threats, whereas txt and bmp files have close to zero chance of containing a threat. For those file types that can include threats, it is important to limit their usage where possible.
- Define Data Scanning and Sanitization Policies
Based on the inherent file threats, more security measures should be applied for file types that are more dangerous. For instance dangerous files such as executables should be scanned with multiple anti-malware engines and should be rescanned for three days in order to decrease the chance of a zero-day attack. Any possible embedded threats in Word or PDF files should be removed with data sanitization by converting their file format. For some users, however, it may be important to use embedded objects in documents. For instance, perhaps the accounting department uses Excel spreadsheets with macros. In that case, Excel spreadsheets to or from these users should be excluded from data sanitization.
- Test Security of Data Flow
The final step in the process is to test your data flow protection. Send embedded objects to users that are not supposed to receive them. Ask accounting to send or receive an executable. Make sure that the correct policies are applied and that threats are removed or blocked. Retest periodically to make sure all bases are covered.
Just as you need a central policy for securing data workflows, you also need a central application from which you can control the protection for different data sources. Being able to consolidate threat protection from one application, allows you to scale more easily, audit the data flows centrally, increase efficiency, and benefit from synergies. An important part of a secure workflow strategy should be the use of multiple anti-malware engines. By combining multiple anti-malware engines, you can leverage the power of the different detection algorithms and heuristics of each engine and detect significantly more threats. These anti-malware engines can be leveraged across the different data entry points and create important synergies to enhance your organization’s protection against threats.
[su_box title=”About Benny Czarny” style=”noise” box_color=”#336588″] As CEO, Benny oversees OPSWAT’s day-to-day-operations and leads the company’s overall business strategy. His 20 years of expertise and deep interest in the Computer and Network Security industry is evidenced by his extensive participation in creating solutions within encryption, network operations, and security vulnerabilities detection fields. His understanding of the industry can be attributed to his breadth of experience spanning roles as a programmer, team leader, and engineering manager in several companies before founding OPSWAT in 2002. Benny earned a Bachelor’s degree in Computer Science from Technion – Israel Institute of Technology.[/su_box]
As CEO, Benny oversees OPSWAT’s day-to-day-operations and leads the company’s overall business strategy. His 20 years of expertise and deep interest in the Computer and Network Security industry is evidenced by his extensive participation in creating solutions within encryption, network operations, and security vulnerabilities detection fields. His understanding of the industry can be attributed to his breadth of experience spanning roles as a programmer, team leader, and engineering manager in several companies before founding OPSWAT in 2002. Benny earned a Bachelor’s degree in Computer Science from Technion – Israel Institute of Technology.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.