Patient Symptoms
You can’t open a newspaper or visit any type of IT website lately without reading of another data breach at either a healthcare provider or health insurer.
According to a recent Ponemon Institute study, a staggering 91% of healthcare organizations had at least one data breach over the past two years, whilst 39% had two to five data breaches, and 40% had more than five data breaches over the same period.
Not surprisingly, after all the press they have generated over the past twelve months, the Ponemon study found that healthcare organizations accounted for 45% of major data breaches reported in 2014. This is an increase of 125% over the past five years and has cost the industry $6 billion, at an average cost of $2 million per breach.
This increase in security incidents is the largest percentage increase when compared to any other industry. Healthcare organizations also have the longest average security event duration, highlighting a lack of data breach detection and inadequate security once attackers were inside their systems.
After years of financial services, banking and retail data breaches being splashed across the headlines, why are healthcare providers and insurers now the preferred targets of cybercriminals?
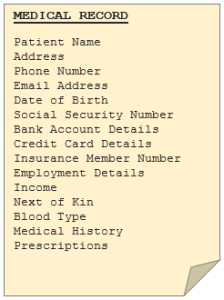 Simply put, healthcare records are a treasure trove of valuable information for hackers, and healthcare organizations have left Ali Baba’s cave door ajar.
Simply put, healthcare records are a treasure trove of valuable information for hackers, and healthcare organizations have left Ali Baba’s cave door ajar.
Consider the type of information your local doctor, physiotherapist, hospital or health insurer holds about you. All your records are digitized and stored in one central location by a company whose main priority is healthcare, not data protection. With the potential misuses of this data, it’s no wonder personal medical files are so valuable on the black market.
The bulk of a healthcare firm’s business and budget is focussed on providing care (or insurance services) to their patients and clients, and therefore lack the resources, processes, and technologies to protect their records – making them a prime target for hackers.
No healthcare organization is immune to these types of cyberattacks – whether you’re a local doctor’s office, a small 20-bed regional hospital or a giant insurance firm – you are squarely in the cross-hairs for these cyber criminals. The FBI has stated that because this valuable information is accessible from one relatively easy to access location, it translates into a high return when monetized and sold – less effort to access the data, and, once inside, there are thousands of records to obtain.
According to Jim Trainor of the FBI’s Cyber Security Division, health records are highly sought after on the black market for the purposes of identity theft, fraudulent tax returns, obtaining restricted medications and more. Whilst credit card details sell for around $5, protected health information records can go from anywhere between $20 and $70.
High-profile data breaches against Anthem (almost 80 million customer records stolen in one of the largest data breaches in corporate history), Premera (11m records) and CareFirst (1.1m) have brought the issue into the national spotlight.
But it’s not as if the industry was caught unaware.
Health insurance giant Anthem was one of thousands of healthcare companies warned not once, but twice last year by the FBI that their industry was particularly vulnerable to hackers. Additionally, in 2013 it was predicted that the healthcare industry would be the most susceptible to data breaches in 2014. It showed serious signs of security ineffectiveness, with a worse average rating than the retail industry. This is evidenced by the Premera breach, which is believed to have begun in May 2014, although wasn’t announced until almost a full year later.
Can We Stop The Bleeding?
Despite the ever-increasing number of threats facing the industry, half of all healthcare organizations have little or no confidence in their ability to detect all patient data loss or theft, but perhaps even worse is that only 40 percent are concerned about cyber attackers.
Recent studies show that the healthcare industry shares a number of similarities with the retail sector, which has also been a big target for cyber criminals in recent years. Both sectors attract a high number of security incidents and slow response times. Both sectors also trail well behind the finance sector in terms of security performance. The same study found a direct correlation between business performance and approach to cyber security, with companies who view it as a tactical issue being outperformed by those who view it as a strategic one. Cybersecurity within healthcare organizations has become a board issue, not just an IT issue. Both CIO’s and CEO’s are being fired over not only the lack of technical resources in place to detect and thwart a breach, but also over the lack of resources provided to IT to procure, implement and monitor such technologies.
For healthcare organizations, perhaps it is because they are focussed more on providing health services than data protection, that cyber security does not receive adequate executive and board level attention. This is also reflected in the resources allocated to information security within the healthcare industry. A Ponemon survey found that the sector generally only invests in resources that ensure compliance with the relevant industry standards, e.g. the Health Insurance Portability and Accountability Act (HIPPA); as opposed to protecting against the advanced threats of today. A different study also found that half of all healthcare organizations spent approximately 3% of their technology budgets on cybersecurity, compared to 10% of an IT budget typically invested by most other industries.
Unfortunately, this seems to be common across the healthcare sector. Organizations appear unwilling (or unable) to invest in cyber security solutions to prevent the data breaches that we see splashed across the headlines each week, or at worst, only invest once they have been breached. Alarmingly, the breach that saw almost 80 million Anthem customer records compromised wasn’t the first time the company had been attacked. In 2012, the company was fined $1.7 million by the Department of Health & Human Services over lax cyber security protocols that didn’t meet HIPPA standards and led to 600,000 client files being exposed in a 2010 data breach. But Anthem was not alone; almost a quarter of all healthcare organizations failed a compliance audit last year.
Regardless, compliance is still a key focus of the healthcare industry, with a survey indicating 54% of organizations have their data protection policies driven by compliance requirements. As we have discovered time and time again, compliance doesn’t always lead to secure environments.
With the lack of resources, processes and technologies to prevent, detect and thwart attacks, compounded by the valuable data contained within health records, it comes as no surprise that healthcare organizations are a prime target of cyber criminals.
Understandably, 72% of healthcare organizations say they are not fully confident in the security and privacy of patient data, with 40% not confident at all.
Over the past year, the most common form of unauthorized access to healthcare records was the result of targeted spear phishing on particular staff members. These accounted for attacks in 88% of the healthcare organizations in the Ponemon survey. Hackers often used the victim’s social media profile to craft legitimate looking emails that would trick them into clicking links that installed malware onto their machine.
Another major concern within the industry surrounds the lack of security utilized for internet-connected medical devices and third-party service providers. These were found to use weak encryption, have little or no key management, insecure communications and poor authentication protocols. Suppliers, who tend to have less secure systems, are often compromised by hackers to gain access to a larger organization’s main network via an external web portal.
In a more recent trend that sounds like something from the next Terminator movie, hackers are now building backdoors into medical equipment to access hospitals’ main systems. This type of medical device hijack, or medjack for short, sees hackers manoeuvre their way through healthcare networks by exploiting a hospital’s weakest link – unpatched internet-connected medical devices such as blood gas analyzers, x-ray machines or MRI scanners. Whilst attackers at present are only interested in accessing valuable patient records, it is not unfeasible for a cybercriminal to alter medication dosages within drug infusion pumps to deliver a fatal dose.
In the wash up from all of this, patients and customers are feeling less than confident that their private information is secure. So much so, that up to 75% are likely to leave their healthcare provider or insurer if they suffered a data breach. Similarly, for those who are looking for a new provider, 63% would avoid those that have experienced an attack.
So what can the industry do to try and better protect customer and patient data, and avoid the fallout of a major data breach?
The Prognosis
Healthcare providers and insurers need to evolve from being just data collectors to data protectors in order to safeguard themselves and their customers from costly data breaches. The attitude that cyber security is an IT issue needs to change. Corporate boards need to become actively involved with data security policy and enforcement, otherwise it could be their jobs on the line in the event of a breach.
Unless the attitudes of healthcare organizations and their boards shift from cyber security compliance to making a strategic investment in client data protection, we can expect to see an explosion of data breaches within the industry. Expenses such as breach repair, data recovery, investment in new resources, legal fees, customer credit monitoring and compensation soon add up to millions of dollars. More and more insurance companies are refusing to pay out on data breach insurance claims due to the victim’s poor cyber security. A data breach can put sensitive patient details in jeopardy and it is paramount that healthcare organizations do their utmost to prevent, detect and minimize the damage caused by such an event.
Failure to increase their data breach preparedness and cyber security posture may see increased scrutiny from industry regulators and legal firms, along with a backlash from consumers. As noted above, three quarters of customers would consider leaving their healthcare provider or insurer if they suffered a data breach.
Cyber criminals are highly motivated, and with so much valuable customer data on file, this should be reason enough for healthcare organizations to start strengthening cyber security and protecting this highly desirable data more carefully.
The consequences of not investing in data protection technologies are great, but it seems some healthcare organizations need to learn the hard way. Here’s hoping, for your personal information’s sake and mine, that they are listening.
[su_box title=”About Andrew Roberts” style=”noise” box_color=”#336588″]Andrew Roberts is a marketing and business Development Manager at StratoKey with ten years experience working in dynamic world leading software houses in both Australia and the UK.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



