The last few years have shown that the most underrated and unaddressed cyber breach potential in any enterprise is from the ‘trusted insider.’ Despite this, many companies seem to have their security investment strategy stuck in a legacy, network-centric mindset. This passé attempt to ‘hard-shell the network’ ignores what leading cyber warriors understand to be the real threat – sensitive yet unprotected information that exists throughout the organization. This is the ‘soft and gooey center’ of an organization is where trusted insiders live, and where they have unfettered access. By their nature, insiders hold positions that allow them to send email, save information to cloud-based depositories such as Dropbox, or even to share sensitive communications and information on BYOD devices such as a personal smartphone.
In the last few years, data breach incidents have risen to an average of two per day, most often at the hands of a trusted user. This has shown us that the insider threat is the clearest and most present danger. Data loss, leak, or theft has emerged as the premier high-impact event that can hit any enterprise. Consider the NSA, arguably one of the most secure organizations on the planet. It wasn’t a hack, an inserted ‘bot’, or malware tunneling through their defenses. It was an insider performing the actions that all insiders take on a daily basis – copy information to a USB key, access file servers, send information via email, that brought the NSA to its knees. Every industry faces the same threat; energy, finance, healthcare, telecom, manufacturer, and government can all be taken down due to an insider’s access and actions.
It’s for this reason that we have been forced to pay attention to this type of threat, and to and apply analytics to see what it really means to the average company. These numbers are worthy of our attention, if not downright frightening.
According to the recently published Insider Threat Spotlight Report:
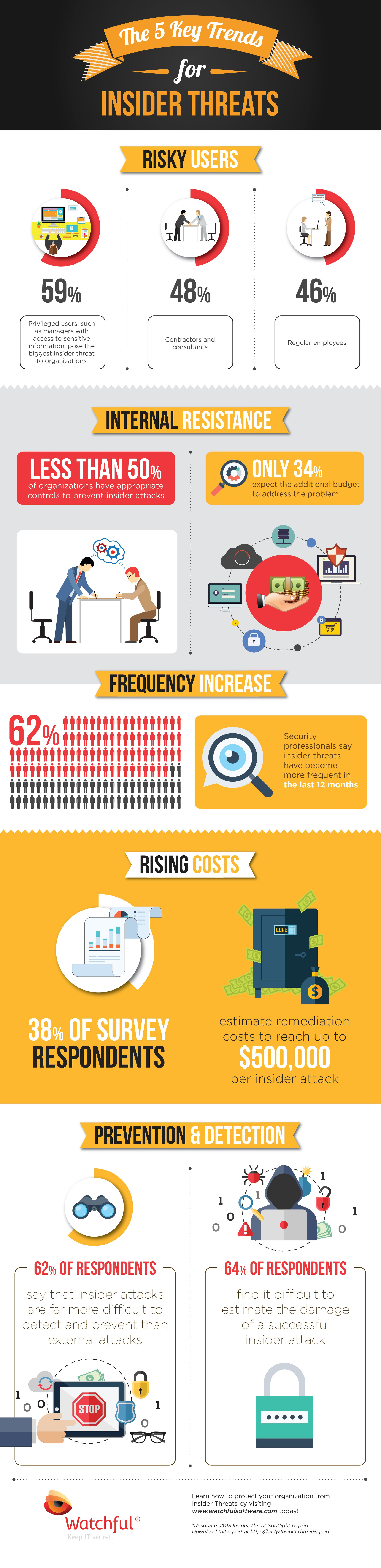
- Privileged users, such as managers with access to sensitive information, pose the biggest insider threat to organizations, followed by contractors and consultants.
- Less than 50 percent of respondents believed their organizations have appropriate controls to prevent insider attacks, and 62 percent of respondents said that insider attacks are far more difficult to detect and prevent than external attacks.
- 38 percent of survey respondents estimated data breach remediation costs to reach up to $500,000 per insider attack. 64 percent of respondents said they “found it difficult to estimate the damage of a successful insider attack.”
The continued attempts to protect against marauding intruders crashing through firewalls is outdated thinking. In today’s world, it’s the insiders that require urgent attention from organizations big and small. The new thought paradigm is built on a spectrum of identifying, classifying, and protecting sensitive information at the level of the data itself. Any information that might be ‘toxic’ if leaked, pirated, or disclosed by insiders (either maliciously or erroneously) must be protected in a way that renders that information useless to anyone without valid rights and credentials. This data-centric approach is the today’s thought process for cybersecurity and cyber-stability.[su_box title=”About Watchful Software” style=”noise” box_color=”#336588″] Watchful Software was formed in 2012 to address the requirement to protect an organization’s most critical asset after its people – its information. The company is staffed by industry executives with decades of systems, software, networking, security, and compliance experience to address the growing need for protecting sensitive and proprietary information against accidental or malicious theft, leakage, or loss. Leveraging key technologies including advanced encryption algorithms, digital rights management, and e-Biometrics, Watchful Software has developed a suite of solutions that ensure only authorized personnel have access to enterprise systems or can handle sensitive information, thereby protecting against the massive economic and competitive damage often done by cyberterrorists and information thieves.[/su_box]
Watchful Software was formed in 2012 to address the requirement to protect an organization’s most critical asset after its people – its information. The company is staffed by industry executives with decades of systems, software, networking, security, and compliance experience to address the growing need for protecting sensitive and proprietary information against accidental or malicious theft, leakage, or loss. Leveraging key technologies including advanced encryption algorithms, digital rights management, and e-Biometrics, Watchful Software has developed a suite of solutions that ensure only authorized personnel have access to enterprise systems or can handle sensitive information, thereby protecting against the massive economic and competitive damage often done by cyberterrorists and information thieves.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.