We all know that Confidentiality, Integrity and Availability, also known as the CIA triad, is simple and widely applicable security model. But is this simple security model is sufficient to address security challenges pose by new technologies such as Big Data and Internet of Things? Big Data poses extra challenges to this triad because of (1) enormous amount of data to be secured, (2) number of sources sending data and (3) variety of data formats. Similarly, Internet of Things (IoT) allows physical objects or “things” to collect and exchange data and thus will present different type of security risk such as privacy or safety issues.
For month of September, we ask our expert panel members if there is need to modify this CIA triad given these new emerging technologies and responses are below:
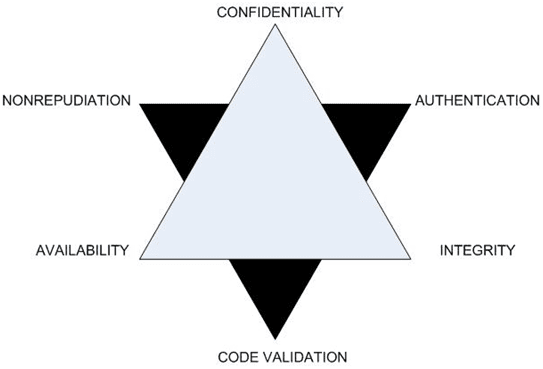
[su_box title=”Allan Pratt, Adjunct Faculty & InfoSecurity Strategist, Los Angeles City College & Consultant” style=”glass” box_color=”#a45bb4″ title_color=”#060706″] The CIA triad is now outdated. There are a few other practices that should be added to the model. Within the last few years, thanks to e-commerce, authentication and nonrepudiation have slowly been added on at the periphery of CIA. But now it is time to add them officially to the security model. One more practice that should be added is Code Validation.
The CIA triad is now outdated. There are a few other practices that should be added to the model. Within the last few years, thanks to e-commerce, authentication and nonrepudiation have slowly been added on at the periphery of CIA. But now it is time to add them officially to the security model. One more practice that should be added is Code Validation.
The 6 Points of Security
The reason for this is quite clear. Except for internal bad actors, threats today come from a myriad of directions to find a company’s vulnerabilities in their software/firmware.
With Big Data, code validation (checking for and then plugging software vulnerabilities) is extremely important. Hundreds or even thousands of terabytes of data are being used to extrapolate information. And while there are many commercial database software programs out there, companies tend to write their own code or modify off the shelf software to get the functionality they need. Without code validation being a central tenant and a constant reminder of CIA, the idea of code validation may not be at the top of people’s minds. Bad code equals vulnerabilities which equals becoming a target. All of that data on those servers can be stolen, sold, used for blackmail or given away. Data has become a commodity. It is bought, sold, stolen, and sometimes give away. It might as well be gold on the commodities market. Keeping code validation a part of any software operation should be as important to the “C-Suite” level as it is to those working on the software lifecycle.
IoT – Internet of Things brings with it so many opportunities for device corruption that I will NEVER buy an IoT device until there is an official governing body and official rules that every manufacturer must follow. Devices going online today have very weak security and software that is easy to hack. There is a whole group of devices (baby monitors) that fail every security test thrown at them. There are no penalties companies that make them have to pay — neither monetary nor in sanctions if they consistently get hacked.
There are hundreds of manufacturers out there that are getting ready to unleash a broad spectrum of devices, from refrigerators to coffee pots, and they have no idea what they’re doing. If they are made to follow the security tenets and are required to check that the software in their devices pass strict guidelines, including verifying their code is sound, I would certainly feel better about those devices being in everybody’s homes and cars.
Let’s look at what happened to Fiat-Chrysler for a moment. Do you think they thought about firewalls, VLANS, airgapping and the code that runs the computers that their cars have become? In my personal opinion, no. Technology is advancing faster than our ability to govern it. But I think following some simple guidelines may go a long way to at least mitigating some of the damage an unpatched, unnoticed, unprepared for vulnerability may cause.[/su_box]
[su_box title=”Charles Sweeney, CEO, Bloxx” style=”glass” box_color=”#a45bb4″ title_color=”#060706″] Alongside the universally regarded pillars of confidentiality, integrity and availability, it could be argued that a fourth idea of flexibility should be added onto the security model. No matter how secure the environment is, data is no longer just collected, stored and retained, but needs to be used by businesses in order to provide the best service possible.
Alongside the universally regarded pillars of confidentiality, integrity and availability, it could be argued that a fourth idea of flexibility should be added onto the security model. No matter how secure the environment is, data is no longer just collected, stored and retained, but needs to be used by businesses in order to provide the best service possible.
To utilise data securely, companies must be flexible in their methodologies in order to take full advantage of the latest technologies. Moving the data to the cloud, assigning ID keys in place of personally identifiable information and being able to replace, remove and update data are just a few techniques that can ensure it is as secure as possible, whilst also remaining insightful for your business.
If companies are to take full advantage of the accelerating IoT and big data revolution, then a large, static data silo will undoubtedly hold them back. Online information is no longer simply kept ‘on record’ but is actively engaged with by forward-thinking businesses. However, data that is being utilised and adding value to business service is without doubt more of a lucrative target to hackers and scammers, so it is vital that it can be manipulated, moved and encrypted with ease, ensuring it remains protected.[/su_box]To find out more about our panel members, please visit the biographies page.