Intended Audience:
- CISO / CIO / Security Directors
- Threat Intelligence Analysts
Technical Content: Low
Summary
On March 4, 2017, a member of the underground forum Exploit with the username “Dereck1” mentioned a new ransomware variant called “Karmen.” Further investigation revealed that “DevBitox,” a Russian-speaking cyber criminal, was the seller behind the Karmen malware on underground forums in March 2017. However, the first cases of infections with Karmen were reported as early as December of 2016 by victims in Germany and the United States.
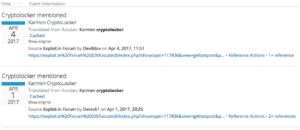
Source: https://app.recordedfuture.com/live/sc/2lbNf7AT41J4
Above are results from a query for mentions of “Karmen” by DevBitox or Dereck1 on Dark Web / Special Access sources in Recorded Future.
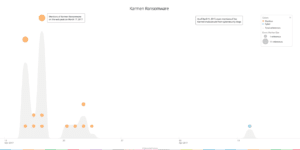
Source: https://app.recordedfuture.com/live/sc/49iWV693EbDg
Above are mentions of the Karmen malware on the web over time.
Background
Karmen malware is “ransomware as a service” (RaaS) derived from “Hidden Tear,” an open source ransomware project, available for purchase by anyone. As is typical for ransomware infections, Karmen encrypts files on the infected machine using the strong AES-256 encryption protocol, making them inaccessible to the user and may trigger a ransom note or instructions demanding that the user pay a large sum of money to obtain the decryption key from the attacker. A notable feature of Karmen is that it automatically deletes the decryptor if a sandbox environment or analysis software is detected on the victim’s computer.
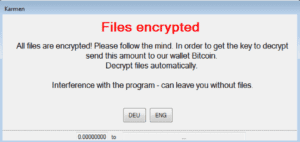
When a user’s computer is infected with Karmen, they’ll see the above message, warning them not to interfere with the malware. Below are screenshots of the affiliate’s page seen by purchasers of the Karmen RaaS.
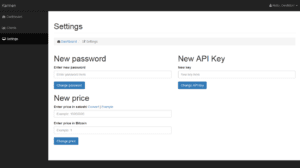
The Karmen interface allows users to change the malware’s settings using a control panel that requires minimal technical knowledge.

The “Clients” page tracks computers infected with the virus.
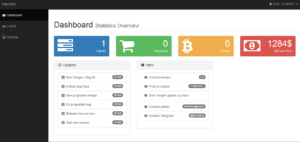
The dashboard gives the user an overview of relevant information including the number of clients they have, how much money they’ve earned, and updates to the Karmen software.
Description of Karmen Malware provided by DevBitox
– Multi-threaded
– Multi-language
– Supports .NET 4.0 and newer versions
– Encryption algorithm: AES-256
– Adaptive admin panel
– Encrypts all discs and files
– Separate BTC wallet for each victim
– Small size
– Automatic deletion of loader
– Automatic deletion of malware (after payment was received)
– Minimal connection with control server
– Robust control panel
– Almost FUD (1/35)
– Automatic file decryption after received payment
– T2W compatible
– File extensions remain the same
– Detection of Anti-debugger/analyzers/VM/SandBox
– Automatic deletion of decryptor if sandbox environment or an analyzing software is detected on victim’s computer
– Light version – Obfuscation and autoloader only
– Full version – Detection of analyzing software
Notes:
– Application .NET dependent
– Support Infrastructure: PHP 5.6, MySQL, “file()” function must be activated on the server
– Rebuild – Free (up to three copies)
– Updates – Free
Price $175
Known Indicators:
File name: joise.exe
File name: n_karmen.exe
File name: build.exe
File MD5: 9c8fc334a1dc660609f30c077431b547
File MD5: 56b66af869248749b2f445be8f9f4a9d
File MD5: 521983cb92cc0b424e58aff11ae9380b
SHA1: dc875c083c5f70e74dc47373a4ce0df6ccd8ae88
SHA1: f79f6d4dd6058f58b384390f0932f1e4f4d0fecf
SHA1: 2a3477ea2d09c855591b3d16cfff8733935db50b
Video presentation of Karmen Ransomware operation, provided by DevBitox.
The seller has admitted he was only involved with web development and control panel design; the malware is utilizing the open source encryption project “Hidden Tear” and was created by an unknown associate operating out of Germany.
As of this writing, twenty copies of Karmen malware were sold by DevBitox, while only five copies remain available to potential buyers.
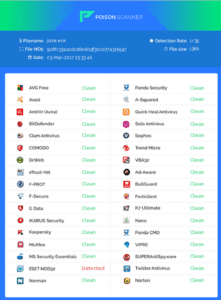
Antivirus scanning results provided by DevBitox.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



