Without doubt the BBC TV Drama Line of Duty kept us all on the edge of our seats as we tuned into every episode, seeking to unmask the corrupt officer known as ‘H’ – with the ultimate episode revealing the gory conclusions of AC12 as they uncovered the murky world of collusion between OCG (Organised Crime Gangs) and the world of corrupt bent Law Enforcement.
In the modern age of dependency on technology, the OCG may leverage the opportunities of the interconnected on-line world to conduct their criminal operations across the planet – as we observed in Line of Duty, with the corrupt officers communicating with their targets from behind the anonymity of a screen. However, it is here where the world of drama in this popular show, and the reality of real-world security procedures parted company.
As with all modern crimes and subsequent investigations, as was shown in the TV drama, where technology is involved, there are areas in which essential elements need to be technically investigated, leading to the discovery and acquisition of the desired artifacts to locate the smoking gun of the culpable parties.
The first area of error of the TV programme was the exposure of data which was easily acquired from the discovered laptops. For example, notwithstanding, say, a PC or Laptop may be protected by a User ID along with an associated Password, to gain access to the stored content is a simple matter of physically removing the drive from the machine, and interfacing it with a unit such as USB3.0 TO IDE/SATA device, as shown at Fig 1 with a selection of drives ready to be processed. From here the data may now be easily acquired, copied and if the operation is to remain covert, the drive may be replaced back as was – the user here would be totally unaware. And even if that data was encrypted, there are methodologies which may be applied, such as surveillance or Social Engineering which may be leveraged to acquire the credentials to access the data – the point is, either way the data objects have been physically acquired. Another advantage of course of using an off-device drive to secure data is, if the mother-ship main computer of our criminal should be unfortunate enough to suffer infection from a Ransomware attack, the data objects are far removed, and are thus secure from compromise of being locked down.
Fig 1 – Accessible Drives

Thus, here was the first error in the programme, as data was easy to access. Fact of the matter is, any Criminal, or OCG member will be employing solutions to secure their data which encompass:
- Keeping the data segregated from the main PC/Laptop
- Ensuring that such data assets are secure with strong levels of encryption.
- Protected by some form of Physical of Logical Tamper Resistant Protection
It is in this capacity in which our on-screen criminals need a little education – they would be well advised to be employing the capabilities of a trusted removable secure drive upon which the sensitive data assets should be located, and here two of my own favoured solutions springs to mind.
The first of which is a FIPS-140/2 iStorage datAshur BT. For our Line of Duty OCG or corrupt Officers, by utilising such a secure unit as this, all data would have been stored away from the main host PC or Laptop, the files would be encrypted, and secure from tampering (as they would self-destruct), However, with this device there is one extra security advantage which is accommodated with 2FA. The datAshur BT also has an associated app loaded onto a partnered Cell Phone with the required access credentials (or say Face Recognition), so you get the best of all worlds. Or maybe our OCG should have considered using a datAshur M2 to secure their trail of criminality. The point here being, no self-respecting OCG Member, or corrupt Police Officer operating at this level would be so slack as to leave their data exposed to such easy access – and of course, in a world suffering from the impacts of Cybercrime, it is asserted that anyone who cares about their data would be taking a note out of the books of the professional criminals, and securing their own assets from unfettered access, exposure and exploitation.
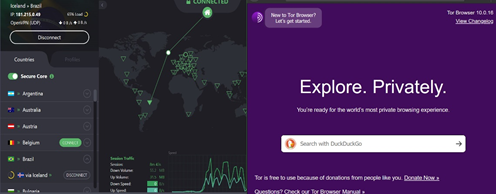
The second area of the drama which made life too easy for the investigations team to discover, and acquire intelligence was when tracing the IP addresses back to the source of the criminal on the other end of the line. Again, with a real-world member operating in the world the OCG, they would be employing multiple levels of VPN (Virtual Private Network) technologies to cloak their actual IP address. For example, Proton VPN which may be routed via say Iceland though Argentina, the UAE to the UK, or as shown in the example at Fig 2 Iceland via Brazil making any such suggestion of an easy identification of the actual source IP very difficult indeed. And even then, those of us who may suffer from a little paranoia may even choose to push the VPN session through an Onion Router, making life even more difficult for the snooper or honest copper in AC12 who is attempting to track activities down to the connected user.
Fig 2 – VPN Tunnelling
Conclusion
For any member of OCG, bent copper, or other such sphere of criminality, it is essential they remember to practice depth and breadth of good security practices – and to secure their ill-gotten data off the main processing asset (PC or Laptop) keeping it out of the hands of AC12; and to conceal their communications inside the tunnelling of a VPN. This may afford such criminals actors as presented in Line of Duty more time to remain at large. But of course, on a serious note, in this time of cyber adversity where digital/cybercrime would seem to be rife, to practice good security is not just for the world of criminality but is for all those who may fall into the crosshairs of an attack. So, ensure you secure your data on a removable secure drive, and always secure your communications with the cloaking of a VPN tunnel – you know it makes sense, don’t be bent, get even!
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



