New ransomware infecting Apple OS X surfaced on March 4 2016, with the emergence of KeRanger.
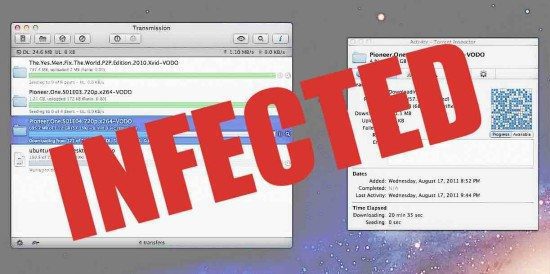
The first inkling of trouble came at the weekend. Users of Transmission – a BitTorrent client widely used on OS X – might have noticed the following warning:
According to the warning, which was displayed within the Transmission application and on its website, version 2.90 of the application was infected. All users were recommended to upgrade immediately to 2.91, as they might have fallen victim to new file-encrypting ransomware to target OS X – dubbed KeRanger.
Analysis of this threat was first published by Palo Alto Networks. ESET Researcher Anton Cherepanov also spotted it and has completed his own analysis. Here is what you need to know, followed by his technical analysis.
[su_note note_color=”#ffffcc” text_color=”#00000″]Anton Cherepanov, Researcher at ESET :
- Is KeRanger just a proof-of-concept or fully functional in-the-wild malware?
Unfortunately, the latter.
- How does KeRanger spread?
It’s spread via an infected version of an otherwise legitimate open source BitTorrent application – Transmission. Its malicious version (2.90) was available for download between March 4 and March 5, 2016 and was signed with a legitimate developer certificate.
- Is it still spreading?
As of March 5, the malicious version was removed from Transmission’s website. Also, Apple has revoked the misused certificate to prevent users from opening the infected installer even if it is downloaded from a third-party location.
- I haven’t seen any demand for ransom. Does that mean my Mac has dodged KeRanger?
Not necessarily. The version of KeRanger we have analyzed stays idle for three days after initial infection. To determine if KeRanger is present on your Mac, do the following:
If any of these files exist, delete them and uninstall the Transmission app:
- /Applications/Transmission.
app/Contents/Resources/ General.rtf - /Volumes/Transmission/
Transmission.app/Contents/ Resources/ General.rtf - %HOME_DIR%/Library/kernel_
service/kernel_service - %HOME_DIR%/Library/kernel_
service/.kernel_pid - %HOME_DIR%/Library/kernel_
service/.kernel_time
- Is there any way to decrypt the files?
Unfortunately, there is not. The malware uses cryptographic algorithms (RSA-2048 and AES-256) that are effectively unbreakable.
- How can I protect my data?
Use reliable security solution. ESET’s users are protected – our software detects KeRanger under OSX/Filecoder.KeRanger.A. We strongly recommend that users back up all of their valuable data on a regular basis.
TECHNICAL ANALYSIS
It is important to note that the malicious Transmission binary has a valid digital signature and, according to its signing date, was signed on March 4, 2016.
The signature belongs to an entity named POLISAN BOYA SANAYI VE TICARET ANONIM SIRKETI, while the legitimate application is signed with a Digital Ignition LLC certificate.
Once launched, the malicious Transmission application checks whether the malicious module kernel_service exists and is running. If it is not, it copies an executable masqueraded as General.rtf file to %HOME_DIR%/Library/kernel_
The kernel_service is typical ransomware, which encrypts user’s files using effectively unbreakable AES and RSA algorithms and asks for payment.
Once executed, it stays hidden for three days before it activates its file encryption capabilities. The time counter is stored in the .kernel_time file.
Once the day comes, it connects to one of 6 sites hosted in the TOR network in order to download a ransom-text message and RSA public key. The connection to the TOR network is made through public TOR2WEB gates.
The OSX/Filecoder.KeRanger.A Trojan enumerates all the files in the /Users and /Volumes folders and makes an attempt to encrypt them. It uses strong cryptography for the encryption – the malware randomly selects a 256-bit key for the AES algorithm, encrypts the file, then encrypts the AES key with the RSA algorithm and saves the encrypted blob to the file. Thus, different files have different encryption keys.
The ransomware might encrypt more than 300 file extensions, including documents, photos, videos, archives, etc. When a file is encrypted its file extension changes to .encrypted.
The malware creates a text file demanding a ransom in all folders with encrypted files. Note that the wording of the message is downloaded from the C&C server. That means it can be modified by the attacker at any time, allowing the attackers to change the amount they demand in ransom, among other things.
The message isn’t displayed pro-actively to the victim.
Indicators of Compromise (IoC)
SHA-1:
- 5F8AE46AE82E346000F366C3EABDAF
BEC76E99E9 - FD1F246EE9EFFAFBA0811FD692E2E7
6947E82687
C&C-servers:
- lclebb6kvohlkcml.onion[.]link
- lclebb6kvohlkcml.onion[.]nu
- bmacyzmea723xyaz.onion[.]link
- bmacyzmea723xyaz.onion[.]nu
- nejdtkok7oz5kjoc.onion[.]link
- nejdtkok7oz5kjoc.onion[/su_note]
[su_box title=”About ESET” style=”noise” box_color=”#336588″]