This report will look at Android apps from the Google Play store. While Android was once the open and transparent rebel to Apple’s rigid and restrictive iPhone, it has of late taken on more the image of a questionable rogue. The App Store has been accused of being a bit of a police state, whereas the Play store has been accused of being too loose and lazy with its oversight. And when the cat is away…
Compounding concern and creating more privacy risk is the fact that Android operates in an all-or-nothing permission fashion, where users accept the entire laundry list of requested permissions or the app cannot be downloaded. This model likely has more users putting less scrutiny on permissions to achieve that instant app gratification.
For this analysis, Zscaler analyzed more than 75,000 apps from the Google Play store in order to determine the permissions that are commonly requested by the apps at the time of installation. As with Apple, many interesting and revealing findings, but in this effort, two of the most compelling findings were:
– 68% of apps that request SMS permissions ask for the ability to send SMS messages. With most Android malware currently targeting premium SMS fraud, this is concerning, especially as users tend to indiscriminately accept requested permissions without scrutinizing whether or not they’re truly needed.
– 28% of apps with SMS permissions also request read SMS access. This is somewhat unsettling as an increasing number of apps/services send codes via SMS for mobile banking or two factor authentication.
As with the iOS analysis, I’d also like to take a moment to discuss the approach. While Jailbreaking is necessary on an iOS device in order to do any kind of static analysis, this is not the case for Android apps. It is the primary reason our analysis numbers are much higher for Android as no manual intervention is involved.
Now on to the analysis. Android is based on a permission system, and each permission represents a given task. Applications can request required permissions and also define new permissions. For example, an application may declare that it requires access to the Internet. As discussed, Android permissions cannot be denied or granted after installation. An Android application declares the required permissions in its AndroidManifest.xml configuration file.
For this analysis, we focused on some of the more dangerous permissions, which allow apps to access a user’s personal information and grant access to functionality such as SMS, the address book etc.
Below is the list of the permissions which we consider to be higher risk permissions:
– SMS related permissions
– GPS related permissions
– Phone call related permissions
– Personal information related permissions
– Address book related permissions
– Device information related permissions
Overall permission analysis:
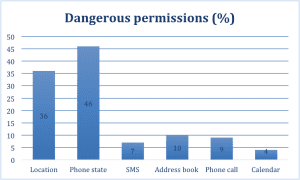
The following graph illustrates the prevalence of dangerous permissions for all Android apps analyzed to date.
From the graph, you can see that of the 75K+ Android apps analyzed, 36% of the apps request location permissions. 46% of apps are asking for the phone’s state permission, which allows apps to access your SIM card information, IMEI number etc. 7% of apps are requesting SMS permissions, 10% request access to a user’s address book and 4% request access to the calendar.
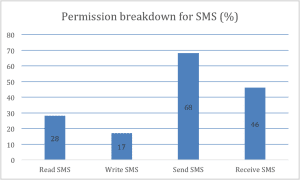
SMS Permissions breakdown:
SMS permissions can be further broken down into the following categories:
– READ_SMS permission: This permission allows the application to read all messages.
– WRITE_SMS permission: This permission allows the application to write SMS messages.
– RECEIVE_SMS permission: This permission allows the application to monitor incoming SMS messages to record or process them.
– SEND_SMS permission: This permission allows the application to send SMS messages.
Here we can see that, from all applications that have access to SMS, most ask for SEND_SMS permissions, which allow apps to send SMS messages from your phone. As the mobile malware market grows, most of the Android malware leverages SMS fraud. We have seen plenty of malware in the past, which abuses SMS by sending messages to premium phone numbers. Also, you can see that a quarter of applications are asking for READ_SMS permissions, which are more dangerous than WRITE_SMS permission as this can expose privacy concernssuch as intercepting two factor authentication schemes leveraging out of band SMS messages.
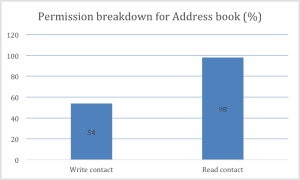
Address book permission breakdown:
Considered permissions:
– WRITE_CONTACTS: This permission allows the application to write to the user’s contact data
– READ_CONTACTS: This permission allows the application to read from the user’s contact data
Here, you can see most of the apps are asking for READ_CONTACT permissions. It is always important to watch this permission as some apps, especially social networking apps, leverage your contact information in order to grow their install base. They want to check your address book to reach out to your friends and encourage them to install the same app.
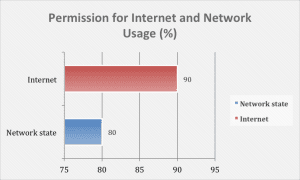
Internet and network related permission analysis:
Permission considered:
– ACCESS_NETWORK_STATE: This permission allows the application to access information about the networks in use.
– INTERNET: This permission allows the app to open and close the network socket in order to connect to the Internet.
Form our data, we have seen that 90% of apps are requesting Internet access and 80% of apps are requesting network discovery permissions, which allow the app to determine the user’s cellular network connectivity, such as whether the user is using 3G or 2G etc.
Conclusion:
From our analysis, outside of Internet permissions, a significant number of apps request access to the phone’s state permissions, which provide apps with the ability to harvest SIM card information and IMEI number information.
Why is this important? Apps, and especially the advertising libraries they utilize, want to be able to track user behavior across apps. By having access to unique identifiers, such as the IMEI, the same user (or at least the same device) can be identified when accessing various content or apps. This allows advertisers to better customize the advertisements that are delivered. Some people are fine with this, but others consider it a breach of privacy. The second most common permissions sought by Android apps involve GPS and user location. GPS data can also be used by advertisers to better target ads; apps are also increasingly becoming location aware, with apps such as Uber leveraging geolocation information to deliver a given service.
SMS permissions provide apps with the ability to communicate, but can also be abused for monetary gain as we have seen with many premium SMS scams. Address book permissions tend to be leveraged to allow apps to grow their install base by encouraging users to promote their apps to friends. While Google does a reasonable job of weeding out malicious apps from the Google Play store, they aren’t perfect, so users should be selective when granting app permissions. This is especially true outside of official app stores such as Google Play, where app scrutiny may be limited – if it exists at all.
Recommendations:
Users should be aware of the permissions they grant and the impact they could have on their device and their privacy. This knowledge will allow users to make better decisions when installing applications. For example, why would a wallpaper app require device SMS permissions? This should raise a big red flag.
Always install apps from trusted sources such as the Google Play or Amazon app stores. The vast majority of malicious apps come from third party app stores and if you want to limit exposure to malicious apps, it’s best to avoid third party Android app stores altogether.
Do not use jail broken phones as they override some of the built in security controls that the o/s provides and make it easier for malicious apps to steal data or provide access to SMS messages, the camera, etc.
Establish a screen lock. Use PINs and enable remote wipe on the device to protect the data in case if it get stolen.
References:
http://developer.android.com/reference/android/Manifest.permission.html
About Zscaler
 Zscaler is transforming enterprise security with the world’s largest Security Cloud built from the ground up to safely enable users doing business beyond the corporate network. Zscaler’s Security Cloud processes over 12 billion transactions a day with near-zero latency to instantly secure over 12 million users in 180 countries, with no hardware or software required. More than 5,000 global enterprises are using Zscaler today to simplify their IT operations, consolidate point security products, and securely enable their business for mobility, cloud and social media.
Zscaler is transforming enterprise security with the world’s largest Security Cloud built from the ground up to safely enable users doing business beyond the corporate network. Zscaler’s Security Cloud processes over 12 billion transactions a day with near-zero latency to instantly secure over 12 million users in 180 countries, with no hardware or software required. More than 5,000 global enterprises are using Zscaler today to simplify their IT operations, consolidate point security products, and securely enable their business for mobility, cloud and social media.