Despite priority placed on cybersecurity, companies still have significant room to improve existing practices
At a time when cybersecurity breaches are becoming more frequent and significant, organisations are continuing to place a high priority on improving their cybersecurity frameworks. However, despite improvement in many areas, one in three companies still lacks policies for its information security, data encryption and data classification, according to The Battle Continues – Working to Bridge the Data Security Chasm: Assessing the Results of Protiviti 2015 IT Security and Privacy Survey from global consulting firm Protiviti.
“Cyber security is not solely a technology problem. The survey highlights that simple steps towards better risk management such as policy and process, still require attention for many,” said Ryan Rubin, a Protiviti managing director with the firm’s global cybersecurity practice. “The survey highlighted that Cyber Security, for many, is still reporting directly into IT which may explain the lack of priority associated in addressing the softer side of security. It’s increasingly important to “set the tone from the top” and define organisational rules and management expectations that will create sufficient awareness to all in the organisation and ensure risk appetite is adequately communicated to protect data, mitigate Cyber risks and manage potential breaches.”
The IT security and privacy survey, which gathered insights from 708 Chief Information Officers, Chief Information Security Officers, Chief Technology Officers, IT vice presidents and directors and other IT management professionals, assesses security and privacy policies, data governance, data retention and storage, data destruction policies, and third-party vendors and access, among other topics that organisations need to manage and improve. Protiviti’s report also includes recommended actions for IT leaders as well as trends to watch.
Key findings from the 2015 survey include :
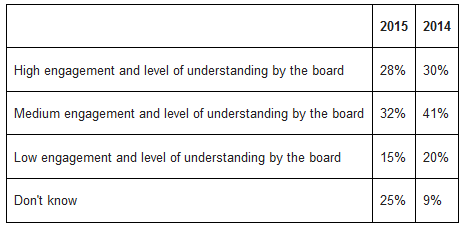
“Tone from the top” is a critical differentiator – From strong board engagement in information security to management establishing “best practice” policies, effective security starts with the right tone from the top, which is as important as any policy.
Only 28 percent of organisations indicated that there is currently a high level of engagement by the board (compared to 30 percent in the 2014 survey) : How engaged is your board of directors with information security risks relating to your business?

Many companies lack critical policies and an understanding of their “crown jewels” – Most have a less-than-excellent understanding of their most sensitive data and information (71 percent) and do not have strong awareness levels concerning potential exposures. Such gaps open up the organization to cyberattacks and significant security issues. Despite these findings, the survey suggests that organisations are now beginning to better understand how to manage and protect sensitive data such as private customer data (80 percent); intellectual property (63 percent); healthcare data (51 percent); and payment card industry information (47 percent).
There aren’t high levels of confidence in the ability to prevent an internal or external cyberattack – While two out of three organisations report being more focused on cybersecurity as a result of recent press coverage, most lack a high level of confidence that they can prevent a targeted cyberattack, either from external parties or insiders. However, this mindset is not necessarily a bad thing – in fact, it may be a healthy one if the perspective drives a focus on improvement.
About the Survey
The fourth edition of Protiviti’s IT Security and Privacy Survey was conducted in the third quarter of 2015. Forty-eight percent of respondents work for organisations with $1 billion or more in revenue and 40 percent of respondents’ companies are public. The majority of respondents’ companies are located in North America.[su_box title=”About Protiviti” style=”noise” box_color=”#0e0d0d”]




