WordPress, a popular platform for developers, has once again become the talk of the IT town due to its unencrypted cookies. Though one may have two-factor authentication enabled on one’s WordPress account, attackers can easily hijack the website using a common or public Wi-Fi connection.
Yan Zhu, a staff technologist at the Electronic Frontier Foundation, was the first to discover this vulnerability. She found that the WordPress server does not secure browser cookies: it transfers them only in plain text. Yan Zhu was therefore able to steal browser cookies after logging in to a particular WordPress account, after which she was able to log in to the same WordPress account from a new browser window, all while avoiding two-factor authentication.
When a user logs in to WordPress, cookies record that particular instance of access using a “wordpress_logged_in” tag. The cookies then remain valid for the next three years, even if the user has signed out of the account.
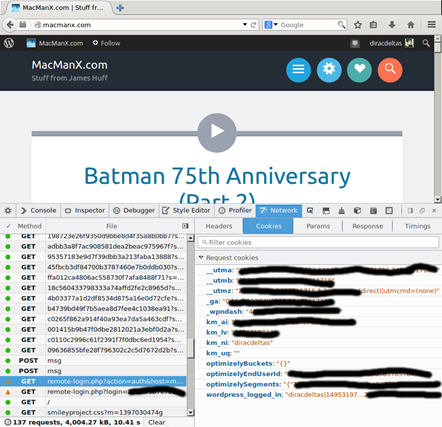
Once authenticated, users gain access to an account’s WordPress Dashboard, where attackers can change the account’s email address and/or set up a new two-variable authentication process.
YanZhu said in a statement, “…[potentially] the insecure cookie could be used to set someone’s 2fac auth device if they hadn’t set it, thereby locking them out of their account. If someone has set up 2fac already, the attacker can still bypass login auth by cookie stealing – the 2fac auth cookie is also sent over plaintext. ”
Andrew Nacin of WordPress said that the next WordPress update will invalidate the cookies at the end of each session and will support SSL encryption.
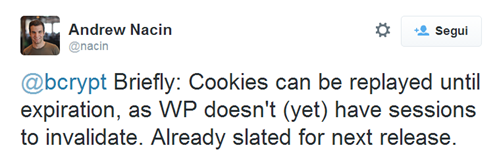
He also stated that this vulnerability does not allow attackers to modify a password.
Users are asked to wait for the upcoming fix and avoid accessing their WordPress accounts across unsecured networks.
Author Bio:
Jason Parms is a Marketing Manager at SSL2BUY Inc. He loves to raise awareness of cyber crime and online security via writing and sharing different articles, press releases and blogs.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



