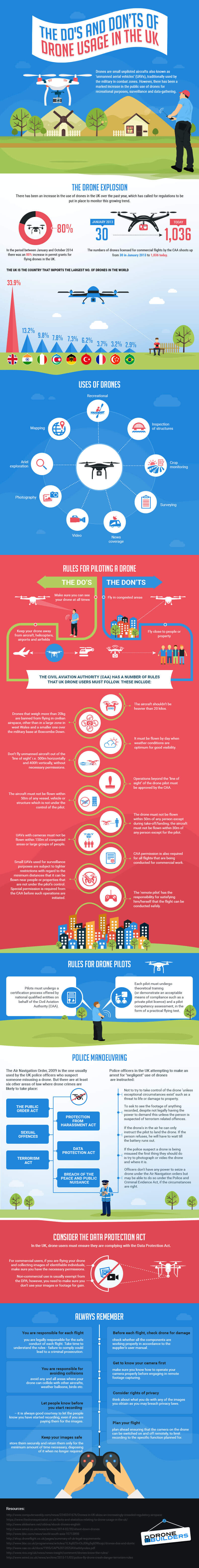
“Drone usage has boomed in the past few years and the number of people applying for licenses and registering drones has increased. This is mostly down to the versatility of drones and the wide range of uses they have.
Drones can be used to give fantastic aerial shots when shooting films and taking pictures but can also be used for more nefarious activities such as spying and carrying out surveillance on a target.
However, some countries have not seen drones in a positive light. Recently, South Africa and several ski resorts across the world, have actually completely banned the use of UAVs (unmanned aerial vehicles). The reason stated for this is that they can cause serious harm to anyone out on the slopes and are a hazard.
The infographic below, created by Drone Builders, aims to highlight the rules and regulations that are applicable when flying your drone in the UK as well as some of the uses a drone could have.”
 [su_box title=”About Drone Builders” style=”noise” box_color=”#336588″]
[su_box title=”About Drone Builders” style=”noise” box_color=”#336588″] Drone Builders is a division of Spider UAS Operations Ltd who are best known for their aerial filming division, Spider Aerial Filming. Their credits include; The Queens Garden (Buckingham Palace), Downton Abbey, 24 Hours in A&E and Homes by the Sea to name a few and they are the leaders in the UK drone filming market. We work closely with the CAA and form part of a technical panel advising on drone safety and regulation for future UK drone operations.
Drone Builders is a division of Spider UAS Operations Ltd who are best known for their aerial filming division, Spider Aerial Filming. Their credits include; The Queens Garden (Buckingham Palace), Downton Abbey, 24 Hours in A&E and Homes by the Sea to name a few and they are the leaders in the UK drone filming market. We work closely with the CAA and form part of a technical panel advising on drone safety and regulation for future UK drone operations.
Our experience has shown that to be successful in Drone operations, you cannot afford technical failures of any kind. Obviously a failure that results in a crash is the worst scenario, but even an intermittent signal from a faulty video wiring harness may be enough to spoil your clients experience with you. With fast growing competition in the Drone operations arena, you cannot afford to lose clients over poorly performing equipment.
Drone Builders is dedicated to producing a professional level product for the elite drone operators of the UK. We offer new build, repair and maintenance services for drone operators who want their equipment to be the best in the business. We also offer a building tuition course for those operators that would like to learn more about their equipment.
The building course provides you with technical knowledge about the workings of your aircraft which will enhance the safety and efficiency of your operations, as well as giving you the confidence to make small repairs yourself. We will also show you what to look out for as your aircraft ages.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



