Earlier in 2021, Andrew Jenkinson the CEO of CIP issued an alert and notified the CWE Team that they were running with some security exposures, leaving their domain open to a higher potential of compromise and security exposure – something the staff at CWE were unaware of at that time – Andy Jenkinson has since published his assessment report on Linkedin today (26/07/21) as a matter of Public Awareness and Interest – See below at Fig 1.
As most readers will be aware, CWE, the ‘Common Weakness Enumeration’ is a category system for ‘software’ weaknesses and vulnerabilities which is supported out of a Community Project with the goals of understanding flaws in ‘software’ and creating automated tools which may be leveraged to identify, fix, and prevent such laws.
The upshot of the CIP conversation with the CWE Team alerted them of a major error associated with their homepage rendering the site, embarrassingly, exposed, vulnerable and exploitable to being compromised and infiltrated. Of course, the real issue here is, given the nature of the work CWE perform, would we, or should we not expect more from such organisations when it comes to knowing their onions, in the schema of Cyber Security? – I will come back to that rhetorical question later.
Fig 1 – Example of the CIP Report

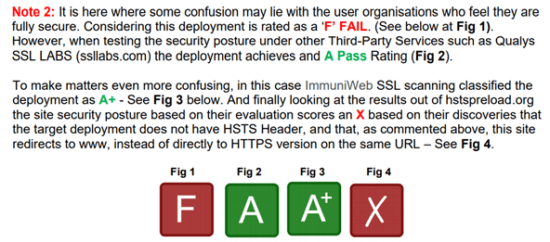
But Onion factor does not stop there and continues into other areas and disciplines. For example, consider those service providers who report on Website SSL Certificates being A+ Graded, when in fact they are actually insecure and vulnerable – and feeding into the pot of confusion which leaves our CISO’s and Security Staff with a potentially false, dangerous vision of a suggested robust secure posture, when in fact it is anything but!
Take the confusing issue related to how Lloyds of London see their own security posture of a very bright Green Tick in the box, when in fact a Red Cross is more appropriate – possibly a case of don’t tell me bad news, when I can look to the corner of the much more convenient, and less troublesome green light – see below as to one other example extract taken from the CIP ITR published in June 2021 at Fig 2.
Fig 2 – Extract from CIP ITR
The Generic World
To return to the question as to if CWE know their onions, when if come to Cyber Security, the conclusion must be yes, they most certainly do! The real problematic root cause here is born out of the word Cyber. Going back pre this term entering the contextual language of the Cyber Expert, we had acknowledged Network Specialist, Firewall Administrators, Web Developers and so on, all highly focused and skilled in their own areas of wide and deep subject matter expertise. However, when the words ‘Cyber’ ‘Security’ ‘Expert’ (Cyber Security Expert) is linked in association – here the problem starts, out of what is being suggested an expert who knowns everything about everything! – and this imposition bleeds over into the operational world of truly understanding the contextual surfaces of weaknesses of the multi-disciplined world of technological complexity. For example, the CWE Team do understand their own software onions when it comes to their disciplined cyber focus – as do others who provide an in-depth assessment as to the level of security associated with say a Certificate (X509), as opposed to a lite touch. Thus, the security hole open’s up by the very generic nature of the all-in-one, all-encompassing approach to understanding the real nature of security exposures and vulnerabilities in a focused, robust and specialised way.
Thus, CWE are reputable, and they most certainly do know their own security software onions – but as can be seen in the article Andy wrote, they do not, in this case recognise everything about everything in the basket filled full of complex Cyber Onion Challenges. It is thus in these instances where, for example, CIP listen to what CWE have to tell them when it comes to Applications and Software security– and in that same conversation, CWE and others should listen to the likes of CIP (and other such areas of security disciplined experts) to provide services which go well beyond the generic lite touch, and dig deeper to underpin very real opportunities to deliver informed security in a very dangerous world of recognised cyber exposures. In this case, CIP boast a specialisation in the arena of PKI and Encryption, and they most certainly do not claim to know everything about everything about every onion on the string – you may say, here we have a case of Horses for Courses.
John is the Principle at Shadow-Intelligence (Si), partnering with PALISCOPE, BreachAware and iStorage. He is a Visiting Professor at the School of Science and Technology, Nottingham, Trent University (NTU) and holds the appointment of Editor in Chief for the International Journal of Cyber Forensics and Advanced Threat Investigations (CFATI). For the last decade he has delivered training courses in the Middle, and Far East to Commercial, Industrial, the Financial Services Sector, and Military Agencies, including the UAE, US, Pakistan, Saudi Arabia, Malaysia (KL), Singapore, Argentina, and Sao Paulo
He served in the Royal Air Force 22 years’, specialising in Counterintelligence, working with UK Agencies such as GCHQ/CESG, and others in the fields of SIGINT, COMINT and Satellite Communications, holding appointments such as System ITSO for a CIA SCIF.
In the commercials sectors of IT/Cyber he has worked for/with Logica, Bae, T5, GM, Experian, Betfair, Palace of Westminster, House of Lords/Commons, TSol (Treasury Solicitors) and provided Consultancy to the Saudi Arabian MOD, TRA (Telecommunications Authority (Dubai) and the Military Academy of Malaysia (KL) on SOC, CSIRT, Digital Forensics and OSINT. Within the last 5 years he has focused on Geopolitics, with global expertise around the UAE and Russia, Anti-Terrorist Operations (ATO), Cyber-Warfare, Dezinformatsiya (Disinformation) and Maskirovka (Military Deception).
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



