Anyone with any involvement in the world of, what we call Cyber Security, will attest that the world may be moving backwards when we consider the number of successful, high-profile attacks which take place on almost a daily basis, impacting the lives of the ordinary users who are dependent on the sustainability of the digital infrastructures. Examples such as the Russian Cyber Attack against one of the world’s biggest meat processors JBS Foods, which shut down the companies’ global operations for five days. Or maybe look toward the power and utilities industry where we will see the historic encounters of Cyber Adversity which in February 2022 implicated Amsterdam-Rotterdam-Antwerp (ARA) suffering disruption of fuel supplies affecting Northern Ports in Germany, or maybe the well documented attack against Colonial Pipeline who fell victim to a $4.4 million Ransomware hit. Then look over the sector of Health Care and Hospitals which have the worrying impact on human life, which in 2021 affected 45 million individuals. And it is most certainly worth mentioning smaller Local Authorises who service their communities with services (AKA the Public) – here take the example of Lincolnshire County Council (LCC) in the UK who had outsourced their cyber security support to Serco. In period 2016 the LCC were hit with a successful Ransomware attack, and whilst their CIO, Judith Hetherington-Smith commented that only a small number of files were affected, this did not address the fact that, services were grossly disrupted, procurements could not be completed so areas like the procurement of schoolbooks and other recourses ran short – with the staff on occasions buying urgent supplies out of their own pockets.
These cross-industry examples, are just a selection from a cast of many, tending to confirm that there are three types of cyber-security postures:
Those which have been hacked
Those who will be hacked
Those who have been hacked, but are unaware
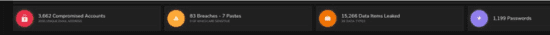
So, having conducted a research project over a 12-month period, the acquired facts and discoveries have been conclusive that no matter the sector being scrutinised, the posture of cyber-insecurity is a common find. Here we may further conclude that, it is not so much the cyber-criminal fraternity who are at fault, but more a case of the supposed secure organisations hosting what resembles multiple-sheets of fusty metal panels, which on occasions find the holes therein lining up, offering a point of ingress for an insecurity to find its target-opportunity. One of the discoveries made during the research project was, alarmingly a regular fine insofar as those involved in the business technology, do tend to be the more insecure organisation. Even more worrying was the discovery of selection companies who actually provision onward cyber-security support for multiples of clients, are actually themselves hosting high levels of an insecure posture – see Fig 1 which represents known known insecurities, ranging from 3,662 compromised accounts, thorough to 1,199 password security issues, and everything else in between, including a massive leakage of 15,266 data objects finding their way out into the hands of potentially malicious actors. Here, we may be looking at a micro level model of insecurity in the image of that which implicated the SolarWinds debacle.
Fig 1 – Insecurity in the Cyber-Security Supplier Chain of Delivery
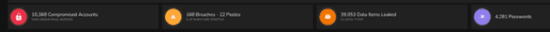
And on the topic of data leakage, and credential exposures, consider those who are the custodians of on-mass sensitive data such as the credit-reference agencies in the guise of Experian, Equifax, and many others, with one breach of Experian manifesting in the exposure of 24 million users! But these matters have been long in the making when you consider their companies footprint as of June 2022, which are shown at Fig 2 and 3. And another cyber debacle out of the Equifax camp exposure no less than 143 million, sensitive consumer records in 2017! As we observe below, again another good (bad) example of what may be discovered through the world of OSINT channels. Fig 2 shows the footprint of Experian, showing a number of compromised accounts, and the significant level of data leakages.
Fig 2 – The Experian Footprint

Fig 3 – Equifax – a Close Second
In the case of Experian, what I do find to be slightly amusing is they is they offer a Consumer Response Team, which is commented to have had over a decade of experience supporting businesses to resource and manage small to large scale consumer crisis or breach response programmes (yes, total agreement here- they have a lot of dog-food related experience).
Thus, we could go on all day looking through a negative lens of the world of insecurity – and granted, we need to be demanding more here, as the situation is utterly dire – when those who are purporting to be supplying cyber resilience services, are themselves a little off the mark of cyber-security expectations, we must be concerned – we need to start building in a robust profile – but how?
Those Standards, Ticked Boxes and Technical Solutions
ISO/IEC 27001: As the last Chair of the UK Government DTI ISO/IEC 27001 Committee, I have had long experience and engagement with the said standard and have also taken a number of Commercial and Government Agencies through to successful Certification – but what’s its worth in real cyber terms. Done well, it can go a long way to underpinning the anticipated robustness of the expectant profile. However, sadly in my experience, what may be practices and demonstrated on the day of the on-site evaluation, post the certification being granted, the wheels can come off – and as such, this in my opinion does not meet the wider expectations of robust cyber security in the 2022 world of insecurity.
Cyber Essentials: Another much touted offering is Cyber Essentials – as they say on their site:
‘Pass first time with unlimited, non-judgmental support. Assure Technical make Essentials certification simple’
As you can see from Fig 4, the certification process would seem to be both cost effective and easy. Making what is, the complex, simple – just like magic!
Fig 4 – Easy Cyber Security

The value of anything which resides at the higher level of the cyber-security food chain will of course deliver the anticipated level of robust security without lifting the bonnet to look at the deeper implications of robustness. Thus, whilst there may be some value in security programs such as Cyber Essentials and the standards like ISO/IEC Certification, they should not by any means be considered enough to facilitate the trusted levels of cyber resilience that are required in the current age of cyber hostility.
Personal Certifications
There is a place in the world of cyber-security for personal certifications, and they do of course provision a tested record of a level of understanding of the subject matter in focus – even if they have been driven via a boot-camp process of brute forced learning. However, on many occasions I have seen these credentials taken fully at their face value as a single point of proof for the attained skill – when in fact they are not. When the tick-box orientated approach is compared to a depth of technological understanding, the value of such personal certifications can pale in comparison.
XDR (Extended Detection Response)
We as an industry have more than our share of buzzwords and jargon than you can shake a digital-stick at. Examples such as Zero-Trust, and another new player on the block, XDR. Again, here we may encounter the rehashing-with-bolt-on elements, of what has gone before but failed to deliver to the anticipation that magical 100% level of security. If you read the hype, it may be that you could start to fall into the hole of believing this has now a real-life possibility. However, read-on, and look at the small print, and the associated outlines and give aways of how such a robust solution may be delivered – for example, take the following line from the implementation of XDR to fulfil the overall posture of security:
‘Zero-delay signatures to rapidly deliver protection and share threat intelligence’
OK, and here is the rub – you can only deploy a Zero-Day fix, as a Zero-Day signature when you know what the Zero-Day is!
On that note, the same goes for the hype of, what looks to be a re-modelled Jericho Forum security aspiration which never really got off the starting blocks, evolving into what we now call Zero-Trust. As a side, in my opinion this approach to cyber resilience is looking at the problem from the wrong side of the security-fence, as I feel this concept should be based on a model of Full-Trust in what we are connecting to, who we associate/partner with (physically or personally), or what we logically employ.
Maybe, not so much XDR of 100% security – but a case of WTF!
AI (HI)
Maybe the new world of delivering cyber-security will be based on AI (Artificial Intelligence) and Machine Learning, a component which is part relied on by XDR model. Consider Ridley Scott’s film, Alien – hand everything over to Al – or MU-TH-UR 6000 (MOTHER). But remember, every element of the initial codding and design of the input into AI is actually HI – AKA Human Intelligence – thus any flaws that man has created, will be shared and baked into the end product, and its future decision-making processes of the machine!
Back to Basics
With, what has become an overreliance on the style of talking-head, and tick-box security, manifesting in the considered, cyber-security professional delivering informed insecurity into their areas of responsibility – but how?
As an example, from an encountered experience with a banking client. In this instance, the bank was paying penetration testers year-on-year to assure their internal security was robust, a status which was fully qualified by the end project report, confirming all was well. Post what were some interesting high-worth illicit financial transaction, and other failed attempts to transfer £100,000, which only failed because of a transaction flag which was set at £99,000 which invoked an alert which required an eyes-on review*. Given the bank had already suffered PCI-DSS exposures when client data was mistakenly loaded onto an external ISP Jump-Server, this dictated some investigation was required – and the potential exposure was discovered. Notwithstanding the annual penetration tests which had been conducted, what had been totally missed was the centralized SAMBA Server, which was processing multiples of connections both internally, and to the Indian based Outsourcer. When this was flagged to their Senior Security Team member, they commented that, and I quote ‘The only Samba I know is the dance’ – a very worrying gap in, what should be essential and qualified knowledge to provide the company with the robust security posture they considered to be intact – with a little more concern, that individual went on to take up another senior role for a power utilities company.
Take another example of a UK company, with a global profile who were running with an Open Zone Transfer, along with exposed servers which had hard coded User ID, and Password within their code – In this case the security expert in question was not only unaware of the ramifications of what a Zone-Transfer implied, but could not locate it, and when eventually it was discovered after a period of a further 3 weeks of exposure – and even then, said expert was unsure how to secure this exposure. Again, as with the previous case, this expert went on to take up a senior role for a well-known band US soft drink company – who has it happens were compromised in May 2022!
It is here where there is an urgent need to grasp the Back-to-Basics approach in which we have an incumbent Cyber-Security Professional who have taken the quantum leap from quoting a line from the ISO/IEC 27001, PAS 555, or the directive of PCI-DSS, and evolved the knowledge and understanding the technology which is under their professional guardianship. Until such time we reach this juncture, the levels of insecurity will march on with swinging open doors exposed to ease of exploitation. Here we see the excellent model of what is referred to as Swiss Cheese Insecurity – with several selected holes in alignment, which then go on to facilitate a successful compromise.
Fig 5 – The James Reason ‘Swiss-Cheese Model’
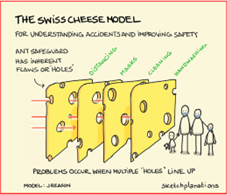
See: https://sketchplanations.com/the-swiss-cheese-model
* Had the attempted transaction been any sum -£99,001 the transfer would have been successful!
Incident Response
Given the grave state of insecurity, which, no matter the size or sector, they may all be expectant of some form of cyber-attack or compromise. This with the assertion that no matter the tier of the professional entity, they must be prepared for the expected with a deployed state of preparedness in the form of on-going OSINT mission discovery capabilities, and the supporting Digital Forensic toolsets residing under the ownership of the SOC and CSIRT teams as applicable to their roles. In such matters I have found tools such as PALISCOPE the investigators browser, and YOSE (Your Own Search Engine) to be what I consider to be my Lexical, searchable database of intelligence and objects (email, EXIF, images, Geolocation etc) to be of high value to associate, or discount forms of acquired data objects to provision an interlinked image of object, and/or personality associations – my must go to applications to formulate a professional engagement to identify and acquire, what I call Meaningful Intelligence out of the surrounding digital noise
Conclusion
Granted, it is my own opinion based on 30+ years, global hands-on engagements, I conjure up my observations based on what is a real-life interface with people and all things interconnected with technological, physical, and non-tangible aspects of IT, or as we now know it Cyber. Throughout this period, year-on-year we may observe the silver plated, magic bullet enter the world of cyber-technology, as the next saviour to save our cyber-bacon, and whilst many such solutions put a big dent in the tin of cyber adversity, by the following year (in in the case of a Microsoft Update, week), that dent of security progress had been reshaped back to where it started life by the aggressors.
I don’t wish to get into the world of teaching egg-sucking. However, I do want to clarify that the road we have, and are traveling in my opinion has, and is suffering from low quality surfacing. We need to rethink what the objectives are of the robust cyber security posture – and accept that 100% achieved security is but a pipedream. I feel we need to start to consider what tangible cyber skills are represented by and put to one side the form of talking-head, tick-box orientated knowledge. We may also wish to stop and think, what the new demi-god solutions are bringing to the table as a one-shot security solution, in an environment which is multi-layered and laced with complexities and configurations, which even their owners may are on occasions unaware of.
Given the state of the Nation (AKA the Planet), it may be to invest into the responsive capabilities of a SOC, CSIRT, and Digital Forensics solutions may be proven to be more beneficial in the reversal of defensive aspects, than that which over trusted provision of the much-sought battle-ready, robust-solution which arrives in the shape of the great hall of Valhalla.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



