In the past few days, internet security researchers have uncovered a major hole in the internet traffic-routing system.The details about the hijack are still emerging. What is known is that someone has been intercepting traffic headed to corporate offices, governmental agencies, and financial organizations at least since the beginning of the year. They have then been redirecting the traffic through Belarus and Iceland before sending out the data en route to their intended destinations.
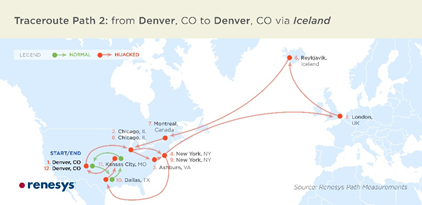 It is currently unknown who is responsible for the hijack. This is partly due to the nature of the hack: anyone with access to a Border Gateway Protocol (BGP) router could have staged the hijack.
It is currently unknown who is responsible for the hijack. This is partly due to the nature of the hack: anyone with access to a Border Gateway Protocol (BGP) router could have staged the hijack.
BGPs are path-vector protocols. That is, they advertise how data transmitted over the Internet can reach a certain Internet Protocol (IP) address. With a BGP router, an actor in cyberspace can send out an announcement to a select group of IP addresses, including those of banks and the offices of foreign ministries. If this announcement promises a faster, more direct, and more efficient route of transmission to destination IP addresses than other routers, these IP addresses will then send their information to that BGP router, at which point the router’s operators can sift through the traffic before releasing it back onto its legitimate internet pathway.
This last part presents the greatest challenge to cyber security experts. Unlike simple routing attacks, incidents of hijacking such as this, which are better catalogued as a Man in the Middle (MitM) attacks, leave no trace. The information reaches their intended targets after being redirected through the BGP routers. Furthermore, depending on the BGP routers, unusual latency in the time it takes to transmit the data might not be observed.
What does all of this mean? It means that someone with a BGP router can infiltrate the public Internet, propagate false messages, and collect a large amount of sensitive information, including credit card numbers and government correspondence, all within microseconds and without the senders’ knowledge that anything has happened.
This capability demonstrates one of the most severe problems associated with BGPs: they are based almost exclusively on trust. That is, other BGPs assume that router announcements are telling the truth about paths to certain IP addresses. They do not question the integrity or authenticity of these announcements, a gullibility which allows internet hijacking to flourish.
Going forward, as this cyber threat continues to develop, information security experts need to begin thinking about how they can better protect internet traffic. One way to do this might include facilitating more communication between BGPs in order to make announcements more trustworthy, such as by tightly granting certificates to IP addresses operating through a BGP router. This could be a promising first step in tackling a major cyber security issue.
 David Bisson |
David Bisson | @DMBisson
Area of Expertise:
David specializes in cyber security as it relates to U.S. national security and to American military and strategic culture.
Professional Biography:
David is currently a senior at Bard College, where he is studying Political Studies and writing his senior thesis on cyberwar and cross-domain escalation. He also works at the Hannah Arendt Center for Politics and Humanities at Bard College as an Outreach intern. Post-graduation, David would like to leverage his extensive journalism experience as well as his interest in computer coding and social media to pursue a career in cyber security, both its practice and policy.
Other articles from David include:
Cyber Coalition 2013: Training for the Future of Cyber Security
HealthCare.gov: The Cyber Security Nightmare
Cyber Security Lessons in the Wake of Project MUSCULAR
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



