In my last blog post on WiFi, I shared my traveling experiences of observing users’ behavior with their mobile devices, particularly how they tend to indiscriminately access public, insecure Access Points. Criminals and researchers alike could exploit such unsafe behavior to learn a variety of things about that particular user. If they so chose, they could then use that information to compromise his/her data.
I am now back in the UK, so I decided to see if my domicile would fare better in security than those AP’s and users whom I encountered while abroad. Unfortunately, my expectations were soon dashed. We are just as insecure here in the UK. In fact, when I take into account the greater number of users, as well as the onslaught of BYOD, I would even go so far as to say that we are far worse off when it comes to likelihood of compromises.
Using an unsecured public AP in the UK, I joined a crowd and connected my test device to the localised WiFi community. I then ran a couple of discovery tools that ultimately told me there were around 30 active users connected to the AP. Mimicking the behavior of an attacker, at this point I looked though the list of users to select juicy targets according to their suggested corporate profiles and the company of their devices [a nice touch, I thought]. I quickly found something interesting, but alas, it was secure from the employed modus operandi [MO] of PAN invasion. So I moved on. Then, as if by magic, a Windows 8 [8.1] system popped up. Moving along the attacker’s thought process, I decided to ascertain what services were running and what ports were offering potential access. In this case, a quick investigation revealed the following:
– Port: 135 – RPC Services
– Port: 139 – NETBIOS
– Port: 445 – SMB over IP
– Port: 2105 – rlogin
The one that got my attention was 445, so for my next step, I elected to see if the port allowed any access. I did so by running a SAMBA Client. Using the following profile, I attempted to connect:
Username = guest
Password = ‘Blank’
I received these results:
– ADMIN$
– C$
– D$
– PRINT$
– Users$
By changing the directory listing to Users$, I arrived at a number of folders, one of which was labeled “Public.” Selecting that particular folder from the list took me right to the directory listing of some potentially valuable data – see Figure 1 taken from this connection via SMB.
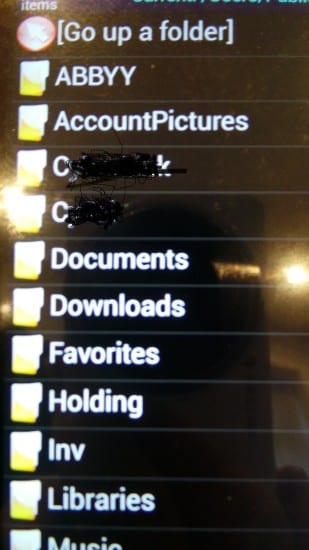
Figure 1
And there you have it. A directory full of valuable information, sitting on an unsecured AP and wide open to anyone who cared to take a look. Clearly, we still have a long way to go with BYOD, and there is, it would seem, a massive hill with regards to educating the public about using unsecured promiscuous environments.
[su_box title=”About Professor John Walker – FMFSoc FBCS FRSA CITP CISM CRISC ITPC
” style=”noise” box_color=”#336588″]
 Visiting Professor at the School of Science and Technology at Nottingham Trent University (NTU), Visiting Professor/Lecturer at the University of Slavonia [to 2015], Independent Consultant, Practicing Expert Witness, ENISA CEI Listed Expert, Editorial Member of the Cyber Security Research Institute (CRSI), Fellow of the British Computer Society (BCS), Fellow of the Royal Society of the Arts (RSA), Board Advisor to the Digital Trust, Writer for SC Magazine UK, Originator of DarkWeb Threat Intelligence, CSIRT, Attack Remediation and Cyber Training Service/Platform, Accreditation Assessor and Academic Practitioner and Accredited Advisor to the Chartered Society of Forensic Sciences in the area of Digital/Cyber Forensics.
Visiting Professor at the School of Science and Technology at Nottingham Trent University (NTU), Visiting Professor/Lecturer at the University of Slavonia [to 2015], Independent Consultant, Practicing Expert Witness, ENISA CEI Listed Expert, Editorial Member of the Cyber Security Research Institute (CRSI), Fellow of the British Computer Society (BCS), Fellow of the Royal Society of the Arts (RSA), Board Advisor to the Digital Trust, Writer for SC Magazine UK, Originator of DarkWeb Threat Intelligence, CSIRT, Attack Remediation and Cyber Training Service/Platform, Accreditation Assessor and Academic Practitioner and Accredited Advisor to the Chartered Society of Forensic Sciences in the area of Digital/Cyber Forensics.
Twitter: @SBLTD
John Walker is also our Panel member. To find out more about our panel members visit the biographies page.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


