The Human Factor 2015 Close-up: What are users clicking on
When we published The Human Factor for 2015 in April we provided an overview of the findings, which could be summarized as a shift by cybercriminals to targeting business users. This change occurred very rapidly over the latter half of 2014, and was visible in every aspect of the unsolicited email campaigns attackers launched, from the users they targeted and the times they sent the messages to the delivery techniques.
One area where the rapid change in tactics was particularly apparent was the message templates attackers used in 2014, and a year-over-year comparison highlights the new focus on business users.
The Human Factor report for 2014 described the most commonly used phishing lures in the previous year:
- Social network communication, such as invitations and connection requests.
- Financial account warnings, such as balance and transaction notices, account status updates, etc
- Order confirmation messages
Of these templates, fake LinkedIn connection requests were the dominant favorite, outnumbering other social media phishing lure templates by 2-to-1. Data from 2014 show that attackers didn’t just shift from these lures, they almost ran from them: in the twelve months to March 2015, there was a 94% decrease in the use of social media invitation lures.
In their place, attackers pivoted rapidly to communication notification templates, and corporate and personal financial communication lures. The communication message took a variety of forms, with voicemail and fax notifications being the most common.
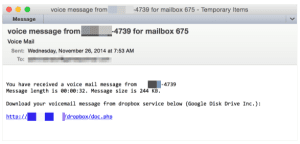
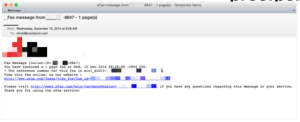 This shift to more business-themed phishing lures was also visible in the corporate financial message templates, which focused more on wire transfer, purchase orders, and business-type transactions than on simple personal account status updates.
This shift to more business-themed phishing lures was also visible in the corporate financial message templates, which focused more on wire transfer, purchase orders, and business-type transactions than on simple personal account status updates.
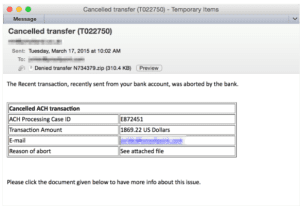
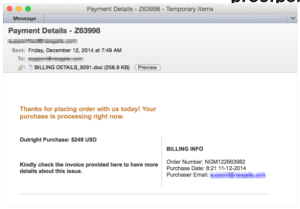 The corporate financial phishing templates also included targeted wire transfer or ACH phish sent to a specific user and with a spoofed “From” line that included the name an executive from the recipient’s company, often the CFO or CEO. These messages sometimes even had no links or attachments; combined with their relatively low volume this made them effective at evading defenses. In general, they had the lowest click rate of the top phishing templates, but conversely often delivered the biggest returns, as the numerous reports in 2014 of losses from fraudulent transfers demonstrated.
The corporate financial phishing templates also included targeted wire transfer or ACH phish sent to a specific user and with a spoofed “From” line that included the name an executive from the recipient’s company, often the CFO or CEO. These messages sometimes even had no links or attachments; combined with their relatively low volume this made them effective at evading defenses. In general, they had the lowest click rate of the top phishing templates, but conversely often delivered the biggest returns, as the numerous reports in 2014 of losses from fraudulent transfers demonstrated.
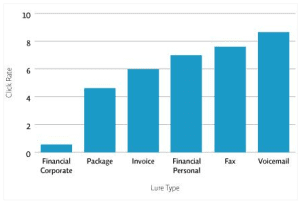
The most commonly used phishing templates in 2014 were also the most clicked.
 This rapid shift is another example of threat actors’ ability to rapidly adjust to changing defenses and new target opportunities, whether it is to target new countries – as we recently saw with France – or different user roles within organizations. Attackers continually adjust their techniques to adapt to changing defenses, whether such defenses are technical or psychological. While an important tool, user education cannot be the last line of defense: organizations should deploy automated defenses capable of detecting and blocking threats that do not look or behave like previously known threats.
This rapid shift is another example of threat actors’ ability to rapidly adjust to changing defenses and new target opportunities, whether it is to target new countries – as we recently saw with France – or different user roles within organizations. Attackers continually adjust their techniques to adapt to changing defenses, whether such defenses are technical or psychological. While an important tool, user education cannot be the last line of defense: organizations should deploy automated defenses capable of detecting and blocking threats that do not look or behave like previously known threats.
Click here to download The Human Factor for 2015 and read this and other analysis of phishing techniques.
[su_box title=”About Proofpoint Inc.” style=”noise” box_color=”#336588″]
Proofpoint Inc. (NASDAQ:PFPT) is a leading security-as-a-service provider that focuses on cloud-based solutions for threat protection, compliance, archiving & governance, and secure communications. Organizations around the world depend on Proofpoint’s expertise, patented technologies and on-demand delivery system to protect against phishing, malware and spam, safeguard privacy, encrypt sensitive information, and archive and govern messages and critical enterprise information.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



