Following news reports that the Democratic Congressional Campaign Committee (DCCC) was breached via a spoofed donation website, the ThreatConnect Research team and Fidelis Cybersecurity teamed up to collaborate and take a look at the associated domain to ferret out additional details on the activity.
The initial indications from the DCCC breach suggest FANCY BEAR pawprints based on the following:
- First, the registrant – fisterboks@email[.]com – behind the spoofed domain actblues[.]com has registered three other domains, all of which have been linked to FANCY BEAR by German Intelligence (BfV).
- Second, the timing is consistent with an adversary reacting to heightened focus after the DNC breach was announced.
- Third, the two name servers used by fisterboks@email[.]com to register four suspicious domains are the same ones used by frank_merdeux@europe[.]com, the registrant of misdepatrment[.]com, a spoofed domain that previously resolved to a FANCY BEAR command and control IP address used in the DNC breach.
- Finally, a pattern exists where the actor is creating fictitious registrant email addresses by leveraging free webmail providers, such as 1&1’s com or Chewie Mail, to register faux domains which contain minor character transpositions or modified spellings. Additionally, the actor is favoring registrars and hosting providers that seemingly provide anonymity by accepting bitcoin for payment.
The following would strengthen our assessment of FANCY BEAR’s involvement:
- Additional information indicating if the actblues[.]com domain was used to compromise the DCCC. At this point, we don’t know whether the domain was used for socially engineered phishing emails, serving up malware, or stealing user credentials.
- If malware is involved with this compromise, having a sample or information on the malware would help us identify whether it is consistent with other tools used by FANCY BEAR.
- If there is any other infrastructure involved with this compromise beyond the actblues[.]com domain and IP, identifying links between registration and hosting information for that infrastructure and known FANCY BEAR infrastructure could augment the confidence in our assessment.
Spoofed DCCC domain identified
Both of our companies respectively researched the domain secure.actblues[.]com, which spoofs the DCCC’s legitimate donation site secure.actblue[.]com. FANCY BEAR actors previously used the same technique with the domain misdepatrment[.]com, which spoofed the legitimate domain belonging to MIS Department, a Democratic National Committee IT contractor. The actblues[.]com domain, which is hosted on a Netherlands IP Address 191.101.31[.]112 (Host1Plus, a division of Digital Energy Technologies Ltd.), was registered using a privacy protection service through the I.T.
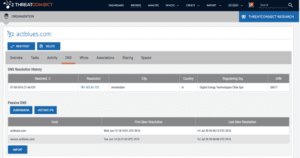
After reviewing the Start of Authority (SOA) record for actblues[.]com we were able to identify the email address fisterboks@email[.]com originally registered the domain.

This fisterboks@email[.]com email address has previously registered three other domains, intelsupportcenter[.]com (hosted on a dedicated server at 81.95.7[.]11), intelsupportcenter[.]net (not active), and fastcontech[.]com, all of which have been attributed to FANCY BEAR activity in an official German Intelligence (BfV) report Cyber Brief Nr. 01/2016. It should also be noted that fastcontech[.]com is hosted at the same ISP as one of the IP’s listed by Crowdstrike for FANCY BEAR (185.86.148[.]227).
Perfect timing
Upon further review of the actblues[.]com domain using the ThreatConnect Farsight Passive DNS integration, we were able to identify the date and time when the domain first resolved.
The actblues[.]com domain was initially registered on June 14th and resolved to the 191.101.31[.]112 IP shortly thereafter. This indicates that the domain was operationalised in less than a day. Stepping out and looking at additional context related to the DNC activity, we identified that CrowdStrike’s initial report on the DNC hack was also published on June 14th. This suggests that, after being outed, FANCY BEAR actors shifted their operation immediately to another target that might allow them to continue collection against Democratic figures involved in the U.S. election.
Peripheral associations
The surrounding infrastructure around the secure[.]actblues[.]com host in the 191.101.31.0/24 network merited a closer look. In one example, we identified that the suspicious domain geopoliticsmonitor[.]com resolved to IP Address 191.101.31[.]116. According to DomainTools, the WHOIS information for geopoliticsmonitor[.]com lists boltini_sandy@post[.]com as the domain registrant and I.T. Itch as providing administrative and name services.

This domain appears to be a spoof of the legitimate domain geopoliticalmonitor.com. Geopolitical Monitor lists itself as a Canadian “international intelligence publication and consultancy”. This aligns with the suspicious domain stratforglobal[.]net, which uses the the Xtra Orbit name services (xtraorbit[.]com / xo.*.orderbox-dns.com) and registrant idolbreaker@mail[.]com detailed in our previous blog. Stratfor lists itself as a “geopolitical intelligence firm that provides strategic analysis and forecasting to individuals and organisations around the world.” Targeting of either of these organisations and or their customers might yield strategic insights or facilitate secondary operations.
In reviewing the peripheral networks associated with FANCY BEAR infrastructure, we saw correlation to the following hosts identified in PricewaterhouseCoopers’s Sofacy II– Same Sofacy, Different Day:
- globalnewsweekly[.]com
- osce-oscc[.]org
- enisa-europa[.]com
- enisa-europa[.]org
- militaryobserver[.]net
As well as other suspicious domains such as:
- academl[.]com – spoofing Blackwater’s new company name.
- tolonevvs[.]com – spoofing an Afghanistan news outlet.
- eurosatory-2014[.]com – spoofing Eurosatory, a yearly military defense conference.
- check-italia[.]ml – spoofing an organisation associated with Italy’s Ministry of Economic Development.
The name server connections
The fisterboks@email[.]com surfaced in our previous post on FANCY BEAR’s use of a bitcoin name server. At the time, we were interested in the two domains intelsupportcenter[.]com and intelsupportcenter[.]net because they looked like domain spoofs of the Intel Corporation, not necessarily because they were registered by fisterboks@email[.]com.
The name services in question – .bitcoin-dns[.]hosting – were also used by misdepatrment[.]com, a spoofed domain (of the legitimate misdepartment.com) that resolved to a FANCY BEAR command and control IP address used in the DNC breach. The same name servers have been used by other FANCY BEAR-linked domains as well as a long list of other suspicious domains that have not been attributed to any particular threat actor.
The domains actblues[.]com and fastcontech[.]com – the two fisterboks@email[.]com domains we identified from the SOA records – were registered through a different name server called I.T. Itch. fastcontech[.]com was also identified in the German Intelligence report on FANCY BEAR and is hosted on a dedicated server at the 185.61.149[.]198 IP address.
When we looked to see who else was using the I.T. Itch name server, we found httpconnectsys[.]com. This domain is notable as the SOA recordindicates that it was initially registered by frank_merdeux@europe[.]com, the same email address that was used to register the misdepatrment[.]com domain. At the time of this writing, we have not identified any other name servers used by either registrant.
I.T. itch registrar
I.T. Itch (ititch[.]com) bills itself as an anonymous web hosting, bitcoin hosting, private domain registration company with a “100% non-compliance rate” aiming to help entities maintain an anonymous digital presence. The company allegedly accomplishes this by “actively ignoring and impeding digital data requests and take-down notices”. Websites on the company’s infrastructure purportedly leverage “web servers located in secret locations on three different continents,” further protecting customers’ private information and freedom of speech, essentially making the site owners anonymous.
Naturally, this promise of anonymity is attractive to cyber threat actors. However, it is this proclivity for anonymous infrastructure, coupled with available SOA records, that led the ThreatConnect Research team to identify additional APT-related infrastructure using I.T. Itch name servers, despite the use of Privacy Protect services to mask registrant data.
Scrutinising additional suspicious domains on I.T. itch name server
We took a look at all of the domains that were registered this year that currently use the same name server (ititch[.]com) as actblues[.]com. From there, we attempted to identify those domains that were hosted on dedicated servers and stood out the most with respect to their name, and potentially what domains or topics they spoofed. Malicious actors from a variety of APT groups will often host their malicious domains on dedicated IP addresses. While this is NOT indicative of malicious activity, it can help us prioritise domains for additional review.
It is important to note that name server co-location does not definitively associate suspicious domains with previous malicious activity. Furthermore, we cannot immediately confirm that the domains listed below are hosting malware or are otherwise attributable to malicious APT activity; however, they deserve additional scrutiny due to the patterns identified above, and the fact that they were registered using a service like I.T. Itch.
| Domain | Registrant Email | Create Date | Hosting IP | Number of Domains at IP |
| actblues[.]com | contact@privacyprotect[.]org | 6/14/16 | 191.101.31.112 | 1 |
| appclientsupport[.]ca | 2/22/16 | 195.62.53.44 | 1 | |
| appleappcache[.]com | contact@privacyprotect[.]org | 5/26/16 | 185.24.233.114 | 1 |
| appleauthservice[.]com | contact@privacyprotect[.]org | 5/12/16 | 185.106.122.100 | 1 |
| applerefund[.]com | larry19ct@gmail[.]com | 5/9/16 | 198.50.218.231 | 1 |
| archivenow[.]org | contact@privacyprotect[.]org | 6/24/16 | 91.216.245.38 | 1 |
| bbcupdatenews[.]com | contact@privacyprotect[.]org | 6/26/16 | 185.106.122.35 | 1 |
| bit-co[.]org | contact@privacyprotect[.]org | 5/7/16 | 141.105.67.90 | 1 |
| bitsdelivery[.]com | bastien[.]prignon@mail[.]com | 7/9/16 | 217.23.2.148 | 1 |
| buy0day[.]com | 0dayshop@ruggedinbox[.]com | 1/29/16 | 91.235.142.58 | 1 |
| dynamicnewsfeeds[.]com | contact@privacyprotect[.]org | 5/7/16 | 185.61.138.58 | 1 |
| ebiqiuty[.]com | contact@privacyprotect[.]org | 6/14/16 | 185.61.149.44 | 1 |
| eigsecure[.]com | contact@privacyprotect[.]org | 7/24/16 | 94.102.53.142 | 1 |
| facebook-profiles[.]com | contact@privacyprotect[.]org | 2/9/16 | 87.120.37.93 | 1 |
| great-support[.]com | contact@privacyprotect[.]org | 5/26/16 | 185.86.151.35 | 1 |
| hackborders[.]net | 7anoncats@yopmail[.]com | 5/31/16 | 91.121.146.56 | 1 |
| login-hosts[.]com | 12ez@freshs[.]co[.]uk | 2/23/16 | 76.74.177.251 | 1 |
| logmein-careservice[.]com | sslajot@mail[.]ru | 6/10/16 | 45.32.227.21 | 1 |
| new-ru[.]org | contact@privacyprotect[.]org | 7/21/16 | 46.148.17.227 | 1 |
| passwordreset[.]co | yosha@openmailbox[.]org | 4/16/16 | 5.100.155.82 | 1 |
| securityresearch[.]cc | contact@privacyprotect[.]org | 2/21/16 | 5.100.155.91 | 1 |
| symantecupdates[.]com | contact@privacyprotect[.]org | 5/3/16 | 185.24.233.122 | 1 |
| socialmedia-lab[.]com | contact@privacyprotect[.]org | 6/13/16 | 185.86.148.88 | 2 |
| vortex-sandbox-microsoft[.]com | contact@privacyprotect[.]org | 4/7/16 | 5.63.153.177 | 2 |
| mofa-uae[.]com | contact@privacyprotect[.]org | 2/11/16 | 185.61.138.53 | 3 |
| social-microsoft[.]com | contact@privacyprotect[.]org | 5/5/16 | 1 |
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



