This season cybercriminals take advantage of online shoppers.
Below are four tips from Proofpoint cybersecurity experts on how to stay cyber safe this season.
- Don’t let your guard down—and don’t click. Holidays are a time when consumers want the fastest route to their end goal, and as a result, they don’t slow down to really pay attention to what they are clicking or what website they are writing into the search bar.
This might seem obvious, but it’s surprising how many people open an email that appears to be from a retailer or type a website address too quickly—only to end up on a malicious site. The easiest thing consumers can do to protect themselves is to avoid clicking on any links embedded in emails. If you want to visit a site, go to the site directly. Do not go via a URL that is provided to you, whether that is via email, text message or social media. Also, be sure to watch the spelling of the website. Cybercriminal “typosquatters” are known to create fake pages with spellings similar to legitimate sites.
Recognizing a bad site or bad links has rapidly evolved past the point of simple human detection. If you click on the wrong link, by the time the web page is visible in your browser, you’ve been compromised—and you’ll probably never know it.
- Mobile applications are convenient, but can cost your privacy. Proofpoint mobile application security specialists often find that people are unaware that the apps on their phone pose a serious security risk. A majority of these nefarious apps are out to steal information, mining private data and sending it to unauthorized servers around the world.
Before downloading an app make sure it has a privacy policy and confirm that the publisher is known. For example, verify that the publisher has an associated website and not just a Twitter feed. No legitimate application should ask for permissions to access data it shouldn’t need. For example, many apps ask for access to your location data, so it’s important to ask yourself whether the app really needs it. Also be sure to check the number of downloads for an app. If the number is low—stay away.
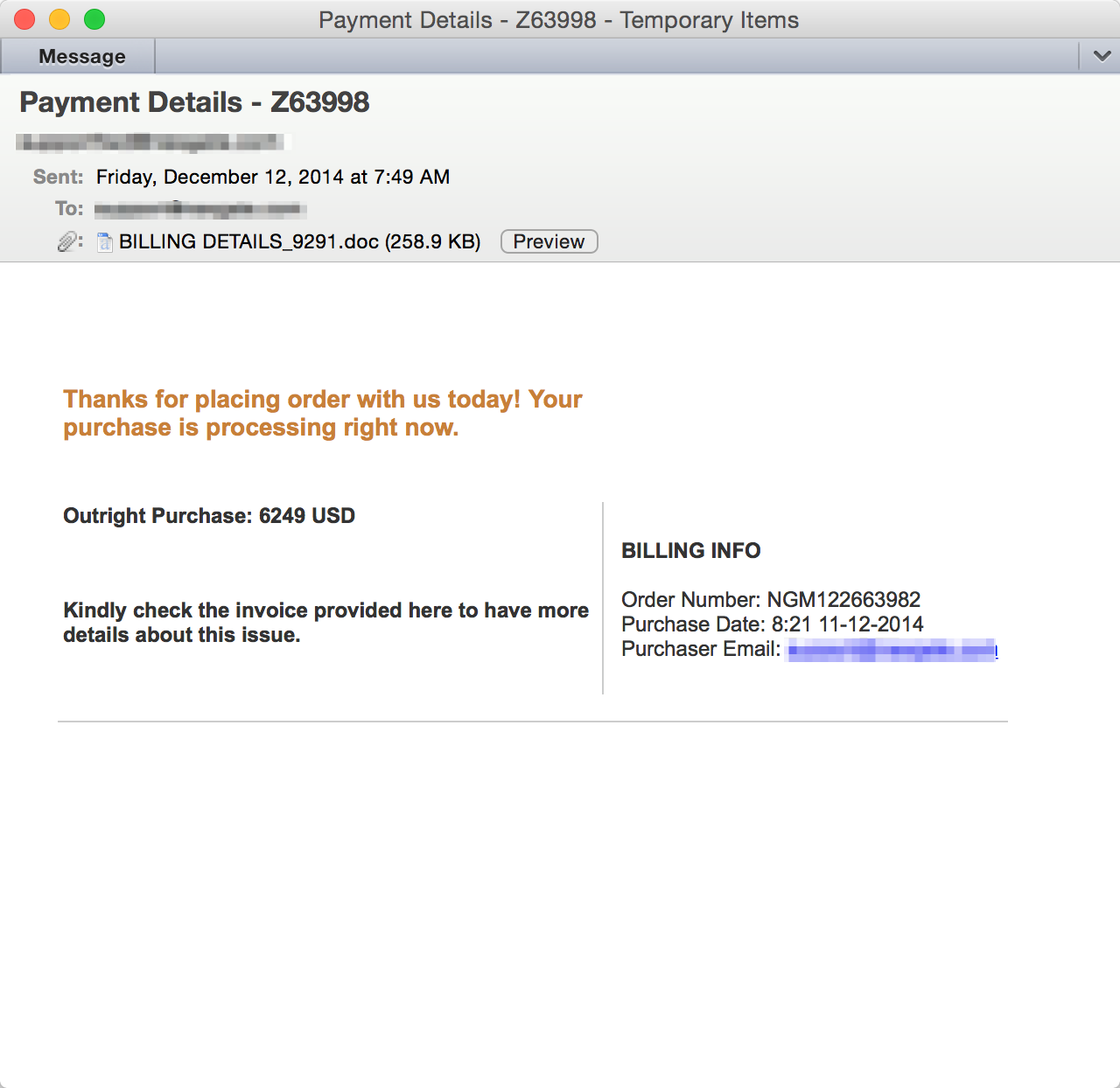
- Watch out for email order confirmations. Great, you placed an order and checked one item off your list, right? Or maybe you received an order confirmation for something you don’t remember ordering? You still need to stay vigilant if you receive an order confirmation via email. Cybercriminals often research potential victims via social media and will send targeted emails with fake order confirmations (see our example below). Psychologically if you receive what appears to be an unsolicited gift, perhaps in the form of an order, package, airline ticket confirmation or similar, an instinctive action is often to click for more information. The best practice is to open a new browser window and visit the vendor’s website to check your order. Below is an example of a fake order confirmation that cybercriminals are actively using.
- Social media isn’t always a friendly place. Watch out for fake brand social media accounts, fake gift card scams and fake customer service pages. We have identified many examples of cybercriminals actively creating fake accounts to lure fans, spam them with malicious links and attempt to extract confidential information. For example, cybercriminals actively creating fake customer service accounts on Twitter to solicit consumers for their financial information. The best practice is to visit the brand’s page and click on their social media links directly to ensure its safety.
[su_box title=”About Proofpoint” style=”noise” box_color=”#336588″] Proofpoint Inc. (NASDAQ:PFPT) is a leading security-as-a-service provider that focuses on cloud-based solutions for threat protection, compliance, archiving & governance, and secure communications. Organizations around the world depend on Proofpoint’s expertise, patented technologies and on-demand delivery system to protect against phishing, malware and spam, safeguard privacy, encrypt sensitive information, and archive and govern messages and critical enterprise information.[/su_box]
Proofpoint Inc. (NASDAQ:PFPT) is a leading security-as-a-service provider that focuses on cloud-based solutions for threat protection, compliance, archiving & governance, and secure communications. Organizations around the world depend on Proofpoint’s expertise, patented technologies and on-demand delivery system to protect against phishing, malware and spam, safeguard privacy, encrypt sensitive information, and archive and govern messages and critical enterprise information.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.