Open source: Security through transparency
The contrast between proprietary and open source software is as old as the IT industry itself. Software in almost every category is available either from suppliers who develop and market their code by themselves or from developer communities who work with open code. Over the last decade the aversion to using open software, especially in the corporate field, has undergone a marked change. Managers realised that if even IT giants such as Facebook, Google and Amazon were relying on open source, ordinary companies should be able to do so too. The advantages of open source are well known: lower costs, the security and higher quality that arise from a large developer community and the absence of ties to one manufacturer are powerful arguments. In some areas open source products are already leaders in their field. Linux, Firefox and WordPress, for example, are hugely successful in the consumer sector. MySQL, Apache, Free BSD, Zimbra and Alfresco are frequently encountered in the corporate environment.
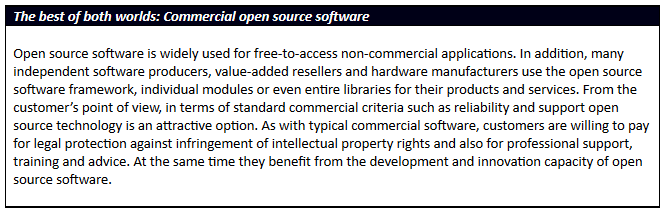
However, the distinction is not black and white: software cannot simply be divided into open and closed, free and non-free, open source and proprietary. There are all sorts of subcategories, which give rise to huge differences in their licensing terms. For companies, however, it is largely only the categories of open source and proprietary software that are of relevance, and it is the combination of the two in the form of commercial open source software that in fact provides the best of both worlds.
Below is a summary – by no means complete – of the most important categories of software on the market. Software is divided roughly into “free” and “non-free”, with a special category that combines open source and proprietary software.
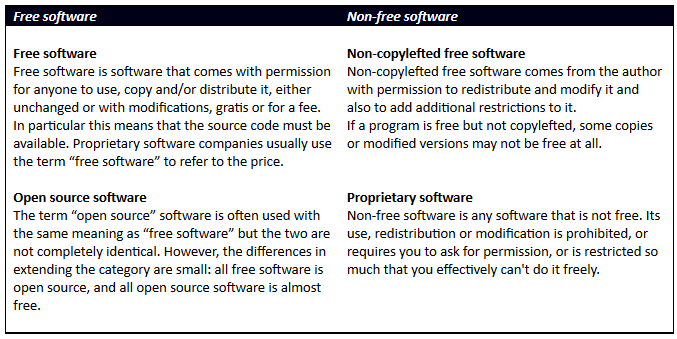
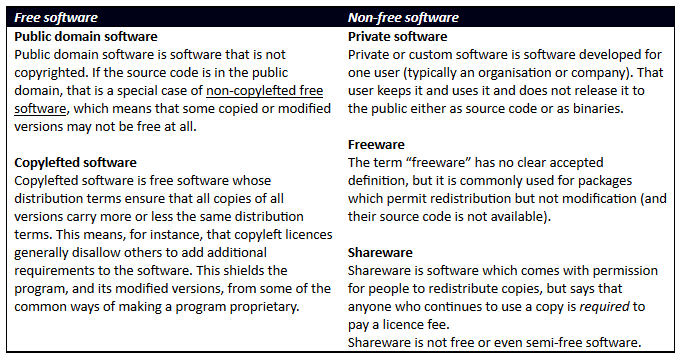 There are thus many different types of software, with software of different origin being used to meet different needs. Many software solutions are available in different versions, with different licence conditions and often a different range of functions. However, a general cultural change is taking place in favour of open source. For example, the EU and the government of the USA are investing huge amounts of money to increase their use of open source. And at CERN, which has long been a pioneer of IT, scientists are being encouraged to conduct their research using the next generation of open solutions. The trend is no longer limited to software. “Open hardware” is now becoming widespread: the Raspberry Pi, the Kano, the Arudion, the Firebox-based MatchStick, the NAO and the Hummingboard are all examples that show how open projects are gaining momentum and awakening new trends, such as the Internet of Things. And yet open source is not something really new. The ultimate open source computing platform is still the mainframe, which was also the nucleus of the present personal computer and hence has always represented a significant open source community.
There are thus many different types of software, with software of different origin being used to meet different needs. Many software solutions are available in different versions, with different licence conditions and often a different range of functions. However, a general cultural change is taking place in favour of open source. For example, the EU and the government of the USA are investing huge amounts of money to increase their use of open source. And at CERN, which has long been a pioneer of IT, scientists are being encouraged to conduct their research using the next generation of open solutions. The trend is no longer limited to software. “Open hardware” is now becoming widespread: the Raspberry Pi, the Kano, the Arudion, the Firebox-based MatchStick, the NAO and the Hummingboard are all examples that show how open projects are gaining momentum and awakening new trends, such as the Internet of Things. And yet open source is not something really new. The ultimate open source computing platform is still the mainframe, which was also the nucleus of the present personal computer and hence has always represented a significant open source community.
Security concerns with open source? Quite the opposite!
With the increasing acceptance of open source software, pure proprietary software is losing ground in the market. Many users have doubts about the future flexibility of proprietary software and many experience dependence on the supplier as an unwanted restriction. As they eye up the future of digital business and government services, companies such as Facebook and Google regard open source as indispensible; most providers are already using open source in various areas of their IT operations. In particular, open source solutions provide a platform for customer-ready technology that can be customised for different products. Nevertheless, despite the growing acceptance of open source, companies still have concerns about liability and security. But what are the facts of the case?
The preconception that open source software is not secure is certainly not valid. The worldwide network of developers, architects and experts in the open source community is increasingly being recognised as an important resource. The community provides professional feedback from experts in the sector who can help companies produce more robust code and create patches faster and can develop innovations and improvements to new services. In a proprietary model the software is only as good as the small group of developers working on it. Companies that rely on third-party vendors for their proprietary software may feel safer, but they are labouring under an illusion: in the name of proprietary intellectual property producers can easily prevent business customers finding out whether there are security flaws in their code – until hackers exploit them. There have been numerous examples of this in the recent past, causing problems for many customers.
Because of the high level of transparency within the open source community, the work of this network of experts is of first-class quality; members attach great importance to maintaining an unblemished reputation. Nobody puts their professional credibility at risk when the whole community can view the code published under their name and comment on it. In consequence community members subject their newly compiled code to painstaking checks before they publish it. This should allay the unjustified fear of security flaws.
Commercial open source solutions – a give and take
Naturally companies want a development model that supports continuous improvement. The open source development model enables companies to support the project in a technologically appropriate way with code tailored to their requirements – and hence to give something back to the community. In commercial open source software all new code undergoes a strict quality assurance process to ensure the security of corporate clients and their end users. Changes that are of benefit to the wider body of corporate customers are checked and the community then adds them to its codebase. To be able to utilise all the advantages of open source, there must be a close relationship with a provider of commercial open source solutions. This is essential in order to promote creativity and contributions within the community. Companies can also provide code to support their business. Providers of commercial open source solutions supply the support and the strict product development process, including the tests with databases, containers and quality assurance that typically form part of the development of proprietary software.
Open architecture plus unlimited scalability provides reliable solutions
Social media, the cloud, big data, mobility, virtualisation and the Internet of Things are constantly turning IT upside down. Existing technologies struggle to keep up with these changes. Companies and institutions must provide their services via numerous channels while ensuring complete data security. With rigid, proprietary systems this is virtually impossible to achieve and the open source community demonstrates daily that open source code products are more than ready to take on important services. Apache is already the number one. MySQL is on the way up; sooner or later OpenStack is highly likely to become the software of choice for the management of computing centres and OpenAM is one of the best products for access rights based on digital identities. Companies that refuse to use open source are likely to fall behind in terms of function breadth and depth and are unable to offer their clients a comprehensive digital user experience.
The success of open source is measured by its ability to ensure a high level of security and innovation. If openly developed software were not safe, security and innovation would not be possible. Open source thus provides security through transparency – something that does not apply to proprietary software. Companies would do well to keep a good eye on open source solutions.
[su_box title=”Simon Moffatt, Solutions Director at ForgeRock” style=”noise” box_color=”#336588″] Simon Moffatt, is a solution director, at ForgeRock. The ForgeRock mission is to transform the way organizations approach identity and access management, so they can deliver better customer experiences, strengthen customer relationships, and ultimately, drive greater value and revenue. We make it happen with the best commercial open source identity stack for securing anything, anywhere, on any device.[/su_box]
Simon Moffatt, is a solution director, at ForgeRock. The ForgeRock mission is to transform the way organizations approach identity and access management, so they can deliver better customer experiences, strengthen customer relationships, and ultimately, drive greater value and revenue. We make it happen with the best commercial open source identity stack for securing anything, anywhere, on any device.[/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



