We are living in a world in which we have either embraced technology, or we have been forced to use it (an example her is online banking) – and of course, we also may accept that, today in the majority of cases we have must tollerate the state of the always-on, always connected world be it for business, or social purposes and we are now in the majority of cases either dependent, or hooked on technology!
Our technological dependency in 2020, leveraging its ease opportunity arrives in a number of different forms, be they hand-held devices upon which multiples of applications are installed (and deleted), Cloud and its related on-line services, or telecommunications such as low cost Voice over IP (VoIP) providing low cost calls; or maybe it is the smart, listening TV sitting quietly in the corner of the lounge along with the equally dangerous listening Smart Speaker with its ‘Hi-Spy’ on me capability. Yes, we are hooked in more than one way! However, when we pull the lid back and look at the wired business world, this really does start to ramp up observation of embracing tech, when one considers just how tied into technology they are, with an increasing and growing dependency on an infrastructure which was never actually designed to carry such a heavy load of business related activities – AKA the Internet. We may then cast our eyes to the Financial Sector, and in particular the failing of systems, ranging from banking outages, ATM infrastructures failures and debacles which have arisen out of RBS and Tesco Bank to name just two from our gallery of disasters which impacted the using public with outages. So we may conclude that, yes, when it comes to dependencies, not only is it proven that we are tethered to technology – in some cases flawed – to drive our lives, but that this very technology has also revealed its foibles, and weak underbelly when it comes to providing resilient capabilities to support our extant expectations of operability.
On the other side of the tech-coin however, we may then cast our eye to the development of Cyber Weaponry crafted and designed out of both low and high investment to be released to the awaiting public by Serious and Organised Criminals, Malicious Hackers, Hacktivists, and of course not forgetting those State Sponsored Actors such as North Korea, Russia, and ‘China’ who utilise malicious tools to underpin and achieve their warped political objectives, arriving in the form of adversity, and in particular at this time of a Pandemic, leveraging the current coronavirus outbreak as a cloak to spread misinformation, fear, doubt, and of course to use the unprecedented viral outbreak to spin off some criminally generated financial gain from the unprepared connected user. But the malicious intent goes much further than this, and moves toward what is downright cruel and heartless when one considers the successful attack against and Italian online Government Service providing much needed financial support to the impacted public to ease the financial consequence of coronavirus. Sadly even in the darkest hours, mankind must suffer those who see disastrous events as an opportunity for corruption, fraud, and other conjoined unacceptable, unethical practices.
The coronavirus Pandemic has by default created an enhanced level of cyber exposure which is being exploited by the adverse factions, feeding off the opportunity of Out of Office, imposed Home Working where the surface of possibility for exploitation has naturally increased in the absence of the overshadowing business hand of security, governance and technological defences. This imposition is possibly the reason why in March/April 2020 cyber attacks increased by around 30% when measured against previous periods, with one example of the WHO (World Health Organisation) seeing a fivefold increase in cyber attacks. Then link this to a study which was published in April 2020 with research from Gallagher, finding that Human Errors account for 60% of all Cyber Attacks, and then add to the mix the Accenture and the World Economic Forum observation that between 2019 and 2023 the cost of cyber attacks are expected to rise to a staggering $5.2 trillion. These reports also comment that that notwithstanding in 64% of cases companies run regular Security Education Sessions, employees were still considered the weakest link, with 39% reporting that employees had clicked on a malicious link, with a further 35% confirming that staff had been caught by Phishing emails. Given here we are talking about the business users who are working within the estate of their employment, just imagine the targetting opportunities of a Perfect Storm condition when we push our workforce into, what have been at times, a state of unpreparedness.
The facts of the matter are, where we are forcing our users to work out of office, in semi, or unsanitized secure homestead environments, it is doubly necessary to ensure that the level of Security Education and Awareness Training they receive is equal to, or more than what the user would normally enjoy inter business accommodation – demanding times place a heavier burden of the business mission to ensure their user base are aware, and fully informed about all cyber risks they now face off campus. By following a maximized approach, we may even be able to decrease the level of risk which exist within the business premises.
We must also assure that, notwithstanding our workers are now remote, they still have access to the company security policies, directives, and materials from which they may draw information to maximize their security effectiveness. Here, this can be achieved with on-line go-bag, or secure USB drive (such as the iStorage Certified FIPS 140/2 encrypted units (https://istorage-uk.com)) containing all the necessary materials, or maybe a server share plugged into Outlook – the possibilities are many.
The Town Hall of Education
On the subject of delivering Security Education and Awareness Training, here we may need to apply a little more imagination to take into account the new challenges of the day dictated by the imposition of coronavirus, conjoined with technology to deliver Town Hall Conferencing facilities and up to date training into the remote users physical locality. Here, the opportunity exists to update all users, at all levels on the latest scams, dangers, and other such point of exposure to which they may fall victim – along with the possibility of compromising sensitive business assets.
OSINT (Open Source Intelligence)
To accommodate the required level of Situational Awareness aligned to the coronavirus pandemic, business should be looking over the hill to gain intelligence as it becomes available though OSINT, leveraging simple tools to trap the associated tag-lines to enable a view of the world of potential hostilities. Watching Social Media, and other such forms of data feeds which can act as an early warning system. For example, utilising free applications such as Tweetdeck may not be rocket science, but in the right hands such a free application can prove to be a Intel god send. See Fig 1 below.
Fig 1 – Tweetdeck
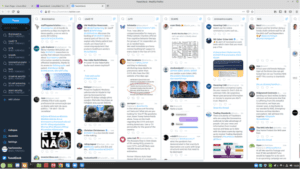
The other value add of utilising OSINT for your own Situational Awareness Purpose is, you may then enhance the delivery of the Town Hall Security Education and Awareness Training specific to your business brand, and you external workforce.
Virtual Security Teams
Another point to enhance the business exposure caused by the pandemic is the disruption of business operations such as the anticipated every day BAU Cyber Security Mission. Of course here we see yet another opportunity for impact on the potential of delivering to the desired security objectives – an exposure our attackers will be very aware off, and are exploiting as I write. It is in this imposition where the essential teams need to evolve new ways of working to meet the presented challenge. As an example, when I was a Security Manager at General Motors (GM) we had our main Security HQ based in Detroit, with multiple global locations spread all over the world. The solution was to introduce a Virtual Security Team (VST) to tie together the security operations, to share intelligence, and of course to achieve many working from one platform to a common goal. Today with the coronavirus challenge, here we see the potential of the VST really stepping forward to plug any potential gap of insecurity-creep.
First Responders – Incident Engagement
Notwithstanding our user are out of sight, they should not be out of mind, and no matter an incident may occur outside of the usual business environment, it nevertheless needs to be accommodated with the same, or a like-for-like robust engagement strategy, which deliver all of the mechanisms of support, including First Responder assignment, and where required collection of artifact, Digital Forensic Capabilities, and of course Incident Resolution.
So, just because we are dealing with users who have been forced into home based, lock-down conditions it does not imply we can ignore the in-house business responsibilities. Again, evolving new ways of working to for forge and adjust our in-house approach, and extend it to reach-out to the multiple remote worker environments. We need to apply imagination and focus on how we deal with any external case related artifacts which may need to be acquired, documented, and then secured as an intrinsic element of evidential materials that will be added to the case-load file. And of course it is equally important, as we discover such remote artifacts that they are subject to the same internal processes, applying robust handling procedures, documenting location, time, date, and the personalities concerned and of course applying the required virtual bag-and-tag process for the case; remembering that any artifact that is taken into virtual custody without the required processes may be worthless if not robustly processed – do not forget, GDPR has expectations no matter where the data rests!
Forensic Defences
Moving onto the practicalities of defending against cyber evasions, and invasions, let us consider where our operational and professional responsibilities exist, and what we should be accommodating to ensure we have a robust position from which to defend and respond to an actual, or suspected, cyber incident. On this level we also need to overcome what can be a regular observation insofar as, why provision a set of capabilities (AKA First Responder Incident Response) when the organisation has never really had any need? Could this represent a bad investment? The counter argument of course is to play the Headless-Chicken at time of crisis, or during a full blown attack upon our remote user is never high on my list of security recommendations – and in the midst of the current intelligence reports of Scams and other such facts of coronavirus cyber aggressions against home based workers, we need to prick up our ears and take note. We must plan for the worst case scenario, and respond from an informed, prepared position – anything less in the current landscape of challenges should be considered reckless.
Tools and Support Materials
I am hopeful that in many cases the business will possess the required tool-sets and materials which will enable them to engage and respond to a cyber incident, but equally accept that some may not meet my expectations. Again driving the point home that in this current landscape of home working, we need to look at the mission with fresh eyes, considering the multiple out of office end points and human operatives for the potential of exploitation.
Run-Books
The first element of the tool-set is to have well documented Run-Books (Security Protocols) which set out the steps, approach and make available the related knowledge to deal with any one of many types of incident – ranging from Malware, Phishing right up to conducting a Digital Forensic acquisition. I have delivered many such document sets into teams all over the world and have observed that when Run-Books are used, no matter the skill level of the engaging First Responder Team Member, as they are working to one formally accepted approach the level of successful outcome is greatly increased to the advantage of the business. And example of a Run Book is at Fig 2.
Fig 2 – Extract from a Run-Book

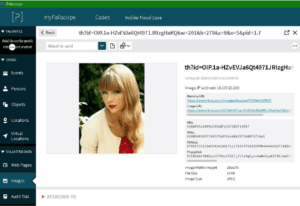
On the subject of tools, when running any kind of investigation it is important to keep track of what has been done, and where you are in the process. Tools such as the Paliscope browser (https://www.paliscope.com/) is one of my always-recommend choices to have in the armoury of the First Responder as Paliscope acts as your Contemporaneous friend, recording all case related activity into a shareable local system secured folder – See Fig 3 where Paliscope is being used to investigate the EXIF data of an Image.
Fig 3 – PALISCOPE
To overcome the challenges of remote acquisition the First Responder may call on a number of tools to achieve their remote investigation requirements, and in this space one of my recommended tools is the Belkasoft Evidence Centre ( https://belkasoft.com/ec) which facilitates all the needs of the First Responder/Digital Forensics Investigator. In particular within this conversation of the home based working communities, the tools ability to acquire and investigative across the wire – a real advantage in the era of disrupted working practices.
Conclusion
As with 911, again our ways of accepting the norms of working have been imposed by the coronavirus pandemic which has imposed the need to evolve and respond to securing our business environment and users. But it is also about using our technology and imagination to defend the Global Economy, and above all we must step up to the plate, start to think out-of-the-box, and recognise the evolution of adversity must drive the mindset of survival in the Information Age.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.


