As many of you know, there is a ransomware attack exploding across the globe. The last headline I read estimated that 90 countries were impacted. This could be one of the biggest cybersecurity incidents we have seen to date. The impact to hospitals is catastrophic and it’s absolutely inexcusable that people’s lives are being put at risk. Seeing ransomware attacks against a hospital gets my blood boiling, and I have some choice words about it, but will refrain for now.
What I do want to address is how this happened. I have seen a number of knee-jerk responses to this incident and want to take a step back and analyze them because I think some people are too close to the issue at the moment.
By now, you have likely seen many claims about the root cause of this attack – from the MS17-010 update not being applied to the “Crazy Bad” vulnerability discovered earlier this week in the Microsoft Malware Protection Engine, to phishing scams. In actuality, what we’re seeing is combination. Most effective malware has the ability to adapt and use a number of exploits to infect and propagate. We are witnessing a jackpot or perfect storm combination that has allowed this attack to be so effective so quickly. It reminds me of incidents like Conficker, where all the right exploits came together to create the Mona Lisa of cyber attacks.
One tweet criticized Edward Snowden and called out the NSA for not privately disclosing the SMBv1 exploit when they first discovered it. While I do not condone agencies for discovering exploits and keeping them quiet, which puts us at long term risk, this vulnerability had the potential to contribute just as badly to an attack of this magnitude, regardless. Think about it: whether the vulnerability was disclosed a year ago or just recently, a knowledgeable attacker would have taken advantage of the vulnerability. This update, regardless of when it was released, made a change in the handling of SMB traffic which could cause significant issues when rolling out an update.
Many companies tremble when a security update causes a significant change to common communication channels or protocols. This SMB update had significant changes and in large enterprises these types of changes can cause legacy applications or proprietary software to break resulting in delays in pushing updates until issues are resolved or other updates are made to affected applications to accommodate the changes.
The fact of the matter is, ransomware attacks keep happening and they’re following the same patterns every time. The scope of this attack and the massive global impact is drawing more attention to the incident, but the basic recipe remains the same: phish user, exploit and infect the system, propagate to more systems, encrypt data on local system, post ransom and get paid.
What has changed is the exploit used to get into the environment, and the means by which these phishing attacks are propagating systems. This attack has enjoyed more success due to the sheer luck of having the perfect combination of exploits to infect and propagate than others.
How do we defend against these types of attacks, especially at such a massive scale? Layered security. That is, a ‘Defense in Depth’ approach that ensures that no one security control is a point of failure. AV and Next Gen Threat Protection are still a critical part of defending against malware and ransomware, but they cannot do it all. I have heard reports that only 30 percent of the AV vendors have been able to catch this variant and there may already be some new variants that are slipping past those. This will continue to happen until the holes in your defense are plugged, as the attacks can keep using the same vulnerability to gain entry into your environment.
Patching is the fundamental way to reduce cyber risk because it reduces the attack surface. If your AV has to defend against 1,000 vulnerabilities, it will be harder-pressed than if it has to defend against 10. I believe, as many others do, the MS17-010 SMBv1 vulnerability is responsible for the massive reach and impact this attack is seeing in propagating itself. This update is only a couple of months old. Companies should be patching this update and many others as quickly as possible, regardless of impact at this point. With the impact companies are seeing, if they do get infected, it’s better to update, plug the hole, and fix a broken application than to have your systems held for ransom.
Application Control is broad security control – whitelisting, memory injection protection, privilege management, and others fall under its umbrella. Some fear whitelisting because of the hassle with implementation, maintenance, and the impact to users, but there are dynamic whitelisting and privilege management approaches that can effectively deliver a level of security without major drawbacks – ‘just in time’ or ‘just enough administration,’ as we refer to it at Ivanti.
Additional technologies can help as well, but these are the two most critical and at the top of most security frameworks because they can reduce the most risk and eliminate the largest amount of attack surface.
I have been having this discussion for a while, but with this incident, I put this into graphical form to make it easier to discuss. Cyber risk is basically a moving target and cyber security is a treadmill that security and IT operations must continue to run on to defend against threat actors. Taking a given update as the center of the discussion, we can start to talk about the risks, how we might defend against attacks, and how the risks continue to grow over time.
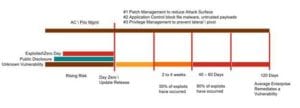
Looking at the graphic, you can see several vertical lines. These represent time frames starting at day zero or the day an update is released – leading up to day zero there is already growing risk.
Unknown Vulnerabilities. These are a risk just waiting to be discovered.
Public Disclosures. These are a considerable risk. Whether by malice or wanting to help, some researchers or activist groups have disclosed vulnerabilities to force a vendor to respond or to bring to light the activities or organizations they want to expose.
Zero Days. This is an exploit that occurs before the vendor has released an update. These three events account for our rising risk; the last of which is a considerable threat, which we can provide some defense against through properly implemented application controls, user education to reduce the effectiveness of phishing attacks, browser and email containerization to contain threats, and more.
Day Zero hits. An update releases – this week happens to be Patch Week. On Patch Tuesday, (or Update Tuesday as Microsoft is now calling it) there were a number of updates released from Microsoft resolving 56 distinct vulnerabilities, three of which were already being exploited in the wild. On top of this, Microsoft also learned of a vulnerability in its Malware Protection Engine. The advisory for this vulnerability went out the day before Patch Tuesday and an update was to be released through a content update within 48 hours. In just one week, we’ve seen Three Zero Days and multiple public disclosures. It’s for this very reason I refer to this risk model as a ‘moving target.’ Attackers can rest easy knowing they just need to be patient and another vulnerability will come along and allow them to exploit systems again.
Time to Patch. This is the measurement of how long from an update being released before it was updated in the environment. Depending on your source, a large enterprise can take as long as 120 days to push updates out to their environment. If we look at the past 120 days of updates from Microsoft alone, there have been eight Zero Days resolved. This means there are probably eight vulnerabilities that already have exploits available to threat actors with exposure to large enterprises.
If you look at information provided by the Verizon Breach Investigations Report for 2015 and 2016, they discuss some trends and patterns to watch for and live by. In the graphic you will see these as the two to four week and 40 to 60 day windows. At two to four weeks, 50 percent of vulnerabilities that will be exploited have been exploited. At 40 to 60 days, this number jumps to 90 percent. This is rather startling considering this is a moving risk window. Each month new vulnerabilities are discovered, disclosed, and exploited.
Ivanti recommends you target your ‘Time to Patch’ goal as two weeks from the vendor’s release. Now, many companies will say this isn’t possible, but I would challenge that. I recently spoke to employees at two large, well-known companies who achieve 90 percent of systems compliant within seven days of release from the vendor. One of those companies has nearly 90k endpoints, while the other has over 300k systems globally. One of these companies is already a customer, while the other is a prospect that wants us to help them do better.
Ivanti also recommends a layered approach to security, starting with the most effective preventative security controls, including patch management, application control, and privilege management. We also provide endpoint security solutions that combine these capabilities with the best threat protection vendors on the market.
The events we are seeing globally are terrible and the people who have executed these attacks should be condemned, but this same event will likely continue to happen unless we improve our defenses against them.
[su_box title=”About Chris Goettl” style=”noise” box_color=”#336588″][short_info id=’102023′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



