The sad reality is that organizations that don’t use multi-factor authentication (MFA) are open to attack when their employees share passwords or fall for phishing scams. So, how can you explain the reluctance in adopting MFA?
Compromised login credentials are one of the biggest security threat to companies today. The reason is that the attacker is using valid credentials, even though they are stolen. Keeping that in mind, why would any of your security tools detect anything suspicious?
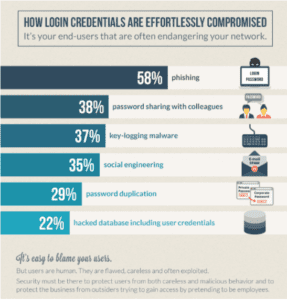
IS Decisions’ research into the access security priorities of 500 IT Security Managers in the US and UK
Despite this well-known threat, many organizations are still doing things the wrong way regarding password security. A few years ago, we surveyed 500 IT Security Managers in the US and UK, the results showed that only 38% of organizations use MFA. Sadly, more recent research show that things haven’t changed so much.
Four Multifactor Authentication misconceptions
Misconception 1: MFA is for large enterprises, not for SMBs
This is a misconception for the simple reason that any company can benefit from MFA, regardless of size. Whether your organization is an SMB or a large enterprise, the data you’re trying to protect is as sensitive. This is why using MFA should be part of every business’ security strategy. Furthermore, MFA is not necessarily complex, costly or frustrating!
Misconception 2: MFA should be used to protect privileged users only
The second misconception among organizations is that they believe they don’t need MFA because they don’t have privileged users. They consider MFA too much for users with no access to valuable data. Well, you need to understand that those “non-privileged” users have access to enough information to harm your company. Let me illustrate this with an example: a nurse selling a celebrity patient’s data to a newspaper. The value of the data is pretty clear here, as well as the possible harm that can be done if inappropriately used.
In addition, the vast majority of attackers don’t start with a privileged account, they usually leverage any account that will fall for phishing scams to then move laterally within the network.
Misconception 3: MFA is not perfect
Well, that’s true. But the thing is, no security solution is perfect. However, MFA is close. A warning was issued last month by the FBI regarding attacks in which attackers were able to bypass MFA. There were two main authenticator vulnerabilities which were ‘Channel Jacking’, involving taking over the communication channel that is used for the authenticator and ‘Real-Time Phishing’, using a machine-in-the-middle that intercepts and replays authentication messages. Experts say that this kind of attack requires high costs and effort. A majority of hackers who encounter MFA will move to their next target rather than try to bypass this measure. Organizations can also take simple precautions in order to avoid certain vulnerabilities such as choosing MFA authenticators that do not rely on SMS authentication. (The National Institute of Standards and Technology (NIST) discourages SMS and voice in its latest Digital Identity Guidelines).
The FBI still believes MFA is highly effective and that it’s a simple step to improve security.
Misconception 4: MFA disrupts users’ productivity
This doesn’t have to be true. Actually, this is a challenge every time you want to implement a new technology. You always need to think about how to least disturb your employees. If the solution is too disruptive, it’ll be adopted very slowly or not at all. That’s why flexibility is key when using MFA. The best way to avoid disrupting your users is to customize MFA to your own needs.
Anyone can be victim of stolen credentials. This is why MFA should be part of every business’ security strategy, whether you’re an SMB or a large enterprise.
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



