Viral phishing campaign targeting Google users and enterprise Google deployments
Introduction
An aggressive phishing campaign went viral yesterday that impacted multiple Google Mail users, which includes enterprise Google deployments. The campaign involved unsuspecting users receiving an email with a Google Doc link from one of their known contacts. If the user clicks on the link and further grants access, their contacts would be leveraged to send the same phishing e-mail with a link from the impacted user account.
The attack involved squatted domains that were recently registered and hosting the malicious web app. Google permitted this app to request access to a user’s email and contacts leveraging the Google authentication service. As such, many users believed that they were responding to a request from Google, not a third party and clicked on it.
Campaign details
We saw mailinator service being leveraged to send out some of the initial spam e-mails with Google Doc links to harvested e-mail addresses. Below is a screenshot of one of the inboxes used in this campaign:
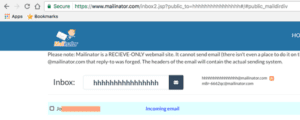
Figure 1: Mailinator inbox leveraged in one of the spams
Here is a sample e-mail that the target user will receive from this campaign:

Figure 2: Google Phishing email with link
If the user clicks on the ‘Open Docs’ link, they will be redirected to Google’s OAuth to select their Google account:
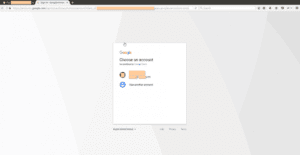
Figure 3: Google’s OAuth redirection
Once the user selects the Google account, the malicious app will request the following permissions, which to the end user looks like being requested by Google Docs:
- Read, Send, Delete, and Manage your emails
- Manage your contacts
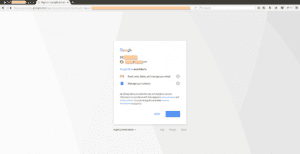
Figure 4: Google OAuth permission for accessing email & contacts
The user will be redirected to a site hosting malicious web app, if they allow access. We noticed ten unique recently registered domains that were being leveraged for this activity. Each of these domains were registered on the same day – April 22, 2017. We saw more than 10,000 hits in two hours yesterday for these squatted domains.
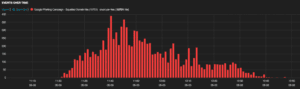
Figure 5: Hits to squatted domains involved in Google Phishing campaign
Conclusion
The attacker leveraged the tried and tested method of social engineering to make this phishing campaign successful. This campaign became viral within minutes because majority of these spam e-mails were sent from legitimate Google user accounts to their known contacts making it difficult to detect.
Google was quick to resolve this issue and provided regular updates on their twitter handle (@googledocs). Zscaler implemented blocks for multiple domains tied to this campaign within minutes of the initial reports, ensuring protection for the customers. Customers leveraging strict ‘Suspicious destination’ based policies were proactively protected from this campaign.
IOCs
g-cloud[.]pro
g-cloud[.]win
gdocs[.]download
docscloud[.]download
docscloud[.]info
gdocs[.]win
g-docs[.]pro
docscloud[.]win
gdocs[.]pro
g-docs[.]win
[su_box title=”About Zscaler” style=”noise” box_color=”#336588″][short_info id=’100036′ desc=”true” all=”false”][/su_box]
The opinions expressed in this post belongs to the individual contributors and do not necessarily reflect the views of Information Security Buzz.



